Network Visibility Products
Garland Technology ensures complete packet visibility by delivering a full platform of network TAP (test access point), inline bypass and packet broker products.
Visibility Solutions
Garland Technology is committed to educating the benefits of having a strong foundation of network visibility and access. By providing this insight we protect the security of data across your network and beyond.
Resources
Garland Technology's resource library offers free use of white papers, eBooks, use cases, infographics, data sheets, video demos and more.
Blog
The TAP into Technology blog provides the latest news and insights on network access and visibility, including: network security, network monitoring and appliance connectivity and guest blogs from Industry experts and technology partners
Partners
Our extensive technology partnership ecosystem solves critical problems when it comes to network security, monitoring, application analysis, forensics and packet inspection.
Company
Garland Technology is dedicated to high standards in quality and reliability, while delivering the greatest economical solutions for enterprise, service providers, and government agencies worldwide.
Contact
Whether you are ready to make a network TAP your foundation of visibility or just have questions, please contact us. Ask us about the Garland Difference!
Building A Zero Trust Visibility Architecture

In response to rapidly evolving cybersecurity threats, Zero Trust, a concept that emerged over 15 years ago, is now a strategic priority for government network agencies. Following reports from the Defense Innovation Board (DIB) and the American Council for Technology - Industry Advisory Council, the federal government is now putting Zero Trust at the forefront of its increased cybersecurity spending.
What is Zero Trust (ZT) exactly? The concept is a departure from perimeter-based cybersecurity as the focus shifts toward individual access and away from protecting wide segments of the network. By narrowing the scope of network defenses, and increasing protection for resources as they span across an increasingly distributed network. Sounds easy enough, right? While there are many facets of implementing a Zero Trust strategy, this blog will review a few main architecture concepts, including ZT Network Requirements, ZT Framework, and ZT Visibility fabric.
Top 10 Zero Trust Network Requirements
In a Zero Trust environment, all traffic must be inspected and logged on the network and analyzed to identify and react to potential attacks. When building a Zero Trust Architecture, additional network requirements include:
- Have basic network connectivity. The local area network (LAN), enterprise controlled or not, provides basic routing and infrastructure (e.g., DNS).
- Must be able to distinguish between what assets are owned or managed by the enterprise and their current security posture.
- Must capture all network traffic - recording packets seen on the data plane, and can filter out metadata about the connection if needed, to dynamically update policies.
- Resources should not be reachable without accessing a Policy Enforcement Point (PEP).
- The data plane, or application data traffic and control plane, which is the policy engine, policy administrator, and PEPs are logically separate.
- Users must be able to access the PEP component to gain access to resources. This could take the form of a web portal, network device, or software agent that enables the connection.
- The PEP is the only component that accesses the policy administrator to establish communication paths from clients to resources. All business process traffic passes through one or more PEPs.
- Remote assets should be able to access resources without needing to link back to the enterprise network (i.e., virtual private network [VPN]) to access services utilized by the enterprise and hosted by a public cloud provider (e.g., email).
- Zero Trust Architecture infrastructure used to support access decisions should be made scalable to account for changes in process load.
- Assets may not be able to reach certain PEPs due to observable factors, possibly based on location (geolocation or network location), device type, or other criteria.
>> Download Now: Zero Trust Cybersecurity [Free Whitepaper]
Zero Trust Framework
After understanding the network requirements for a Zero Trust environment, start mapping out the various components on the network. The National Institute of Standards and Technology (NIST)’s logical framework model focuses on how the policy engine, policy administrator, and policy enforcement communicates with each other.
The policy engine lets a user access each resource, with the decision based on enterprise policies. The policy administrator connects to the policy engine, once the policy engine determines whether the user is allowed to access a resource, and whether to execute and create the authentication credential needed.
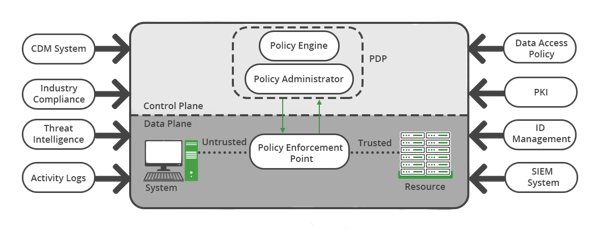
The policy enforcement point handles the connections between users and resources. Its job is to monitor and determine the continued access between the two.
This framework also lays out how complementary components are integrated, including a Continuous diagnostics and mitigation system, Industry compliance system, Threat intelligence feed, Data access policies, Enterprise public key infrastructure, ID management system, Security information, and event management (SIEM) system and Network and system activity logs.
Zero Trust Visibility Fabric
Within this framework, “Network and system activity logs” represent an enterprise system that aggregates asset logs, network traffic, resource access actions, and other events that provide real-time (or near-real-time) feedback on the security posture of enterprise information systems.
While every government agency network will require a unique design to meet specific needs, any Zero Trust Architecture needs a visibility fabric to capture all network traffic.
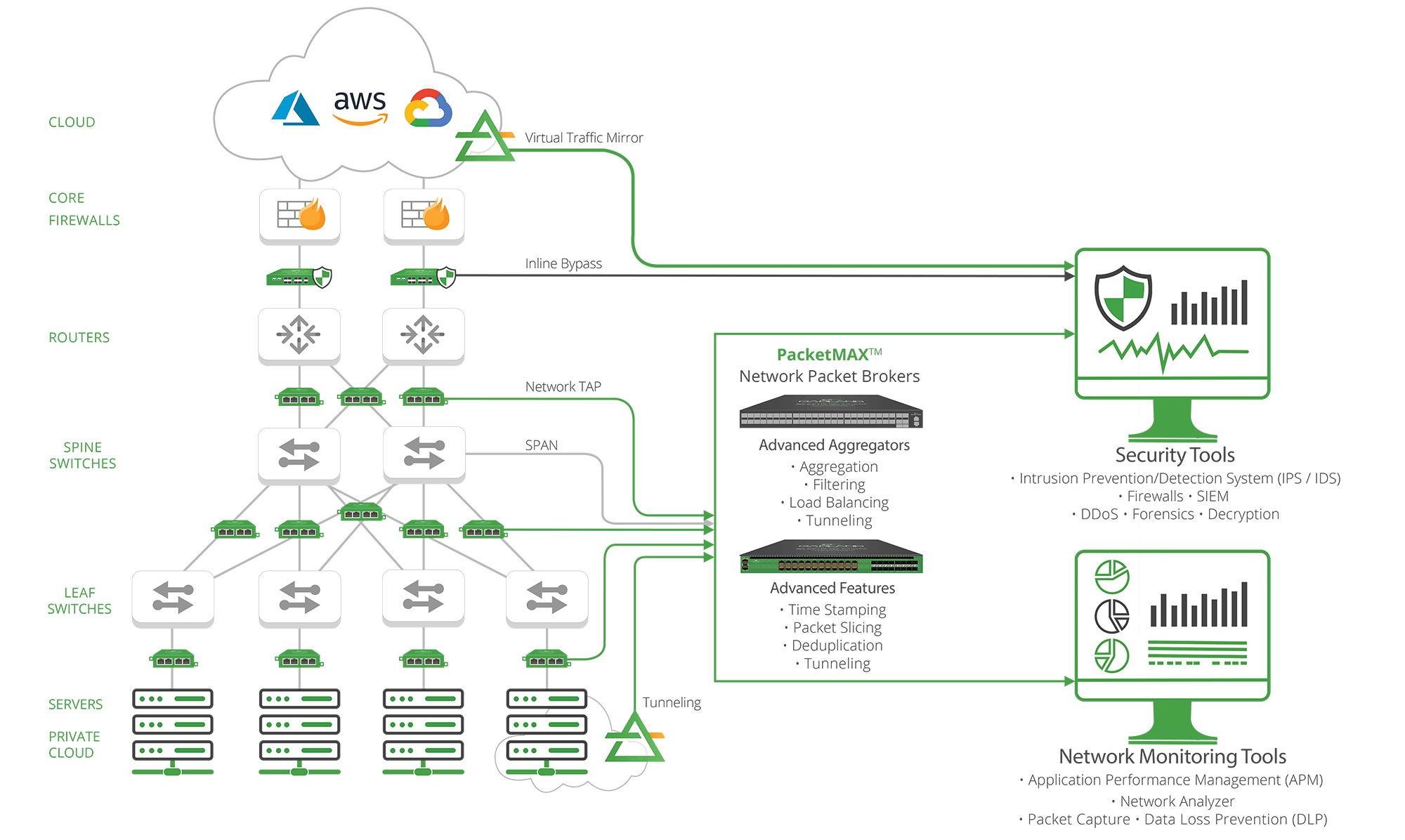
When you implement a visibility infrastructure that leverages network TAPs and network packet brokers (NPB) that ultimately feeds data to your network monitoring and security solutions, you’re able to maximize the effectiveness of Zero Trust through:
Improved Risk Assessment: Being able to guarantee total visibility into your network traffic and data flows makes it easier to spot vulnerabilities and manage changes to the protect surface.
Reduced Network Complexity: Network TAPs and NPBs make it easier to maximize tool utilization through load balancing, packet filtering, and other features. These features minimize the number of tools you need to deploy to maximize visibility, reducing complexity in sprawling government networks.
Streamlined Infrastructure Upgrades: A visibility layer creates more access points to your network and an ability to implement inline or out-of-band security and monitoring tools. Instead of taking the network down for extended periods of time to upgrade infrastructure components, you can maintain data flows while making changes to the architecture.
Better Tool Performance: The only way for your security and monitoring tools to deliver the best results is for them to see every necessary packet of traffic. Your network visibility layer ensures each tool is fed with every bit of data it needs to support Zero Trust.
Greater Scalability: Over time, government networks will need to increase speeds to keep pace with modern use cases. A proper visibility layer makes it easier to plan bandwidth increases and demands for greater traffic support.
Fewer Compliance Violations: Compliance violations occur because of blind spots in government networks. When your monitoring and security tools can see all data packets, you can stay ahead of problems that would otherwise build until your network was out of compliance.
Each of these benefits can be built into a Zero Trust Architecture if you leverage the right tools. To build a visibility fabric that supports the most effective Zero Trust Architecture, you need to design the right combination of network TAPs, network packet brokers (NPBs), bypass TAPs, and cloud visibility solutions.
Taking steps toward Zero Trust starts with implementing a Zero Trust Visibility Architecture, by guaranteeing total network visibility that meets the highest government cybersecurity maturity levels.
Garland Technology is here to help you succeed on the path to Zero Trust. Our full portfolio of network TAPs, network packet brokers, bypass technology, and cloud visibility solutions will simplify your cybersecurity upgrades. Set a Design-IT meeting with one of our network engineers for a no obligation, Visio network design session.
Written by Harry Berridge
Harry is Garland's Director of Federal Operations. With over 30 years of experience in sales, marketing, and channels, Harry brings a wealth of knowledge and expertise working in the Federal space to Garland Technology.
Authors
Topics
- IT Security (200)
- Network TAPs (138)
- Network Monitoring (133)
- Hacks and Breaches (87)
- Network Management (77)
- Network Design (73)
- Industrial OT (70)
- Technology Partners (63)
- Network Infrastructure (56)
- Inline Security (49)
- TAPs vs SPAN (47)
- Network Packet Brokers (40)
- Data Center (37)
- Cloud Solutions (33)
- Software Defined Networking (SDN) (24)
- Events & News (20)
- The 101 Series (18)
- Federal (17)
- Cisco Solutions (16)
- Wireshark (14)
- DesignIT (13)
- Healthcare (11)
- MSP/MSSP (9)
- Palo Alto Networks (8)
- Finance (7)
- Troubleshooting (5)

