

As an instant response firm, the Cyber Defense Group focuses on two critical aspects of cyber security, the proactive side, which they call a virtual CISO, and the reactive side, which is the instant response to some sort of cyber attack.
The team over at the Cyber Defense Group (CDG) came to Garland Technology because they were looking for an affordable way to improve the visibility into their clients’ networks. Visibility is a critical component of their business, proactively to know what’s going on in the network, which can be difficult with the existing infrastructure; and reactively, when visibility is a must, because a client is under attack, and time is of the essence.
With a complicated network full of legacy equipment, an onsite IT team unaware of the problems, and an underperforming MSSP, CDG had a challenge when they were called into an instant response case with a large, healthcare organization. It quickly became apparent that visibility was needed to monitor the traffic and understand where the attackers were coming from, and what network traffic they were accessing. The switches the client originally had weren’t configured/updated correctly, so the only option was to turn to TAPs.
“We’re under attack and every minute that we don’t have visibility, is another minute that bad guys are exfiltrating sensitive data.” -Lou Rabon, Founder/CEO, Cyber Defense Group
A search for TAPs on the internet turned up Garland Technology as an alternative to the huge providers like Gigamon, who can be expensive and don’t provide a custom solution, and buying a cheap TAP off of Amazon wasn’t an option. CDG chose Garland Technology as their TAP vendor of choice due to the fact that right from the start, there was personalized support from the sales and design team to find the right solution for their needs.
By utilizing two Breakout TAPs and one Bypass TAP, in aggregation mode to feed the packet capture, intrusion detection, enterprise security monitoring and log management tools. Despite having only one network link ingressing into port A, the bypass TAP will still egress the traffic out of port B and create a copy of Port A to egress out of Port C.
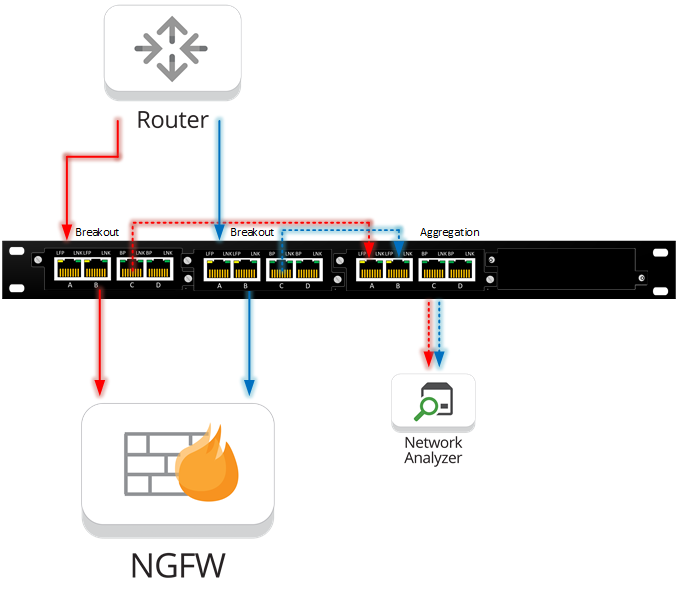
Using the Breakout TAP on each end of the connections to feed Port C from both TAPs into the Bypass TAP (Set in Aggregation Mode). The Bypass TAP takes the breakout inputs and egress them together out a single port to the monitoring appliance. Since each network link is at most 500Mpbs, there is no risk of oversubscribing the 1G monitor port on the Bypass TAP. Cyber Defense Group was able to get the visibility they needed to find the source of the breach, and kick the hackers out.
[Want to learn more about how this solution solved a critical challenge for CDG? Read our latest use case on the topic.]
If the inline security tool goes off-line, the TAP will bypass the tool and automatically keep the link flowing. The Bypass TAP does this by sending heartbeat packets to the inline security tool. As long as the inline security tool is on-line, the heartbeat packets will be returned to the TAP, and the link traffic will continue to flow through the inline security tool.
If the heartbeat packets are not returned to the TAP (indicating that the inline security tool has gone off-line), the TAP will automatically 'bypass' the inline security tool and keep the link traffic flowing. The TAP also removes the heartbeat packets before sending the network traffic back onto the critical link.
While the TAP is in bypass mode, it continues to send heartbeat packets out to the inline security tool so that once the tool is back on-line, it will begin returning the heartbeat packets back to the TAP indicating that the tool is ready to go back to work. The TAP will then direct the network traffic back through the inline security tool along with the heartbeat packets placing the tool back inline.
Some of you may have noticed a flaw in the logic behind this solution! You say, “What if the TAP should fail because it is also in-line? Then the link will also fail!” The TAP would now be considered a point of failure. That is a good catch – but in our blog on Bypass vs. Failsafe, I explained that if a TAP were to fail or lose power, it must provide failsafe protection to the link it is attached to. So our network TAP will go into Failsafe mode keeping the link flowing.
Single point of failure: a risk to an IT network if one part of the system brings down a larger part of the entire system.
Heartbeat packet: a soft detection technology that monitors the health of inline appliances. Read the heartbeat packet blog here.
Critical link: the connection between two or more network devices or appliances that if the connection fails then the network is disrupted.