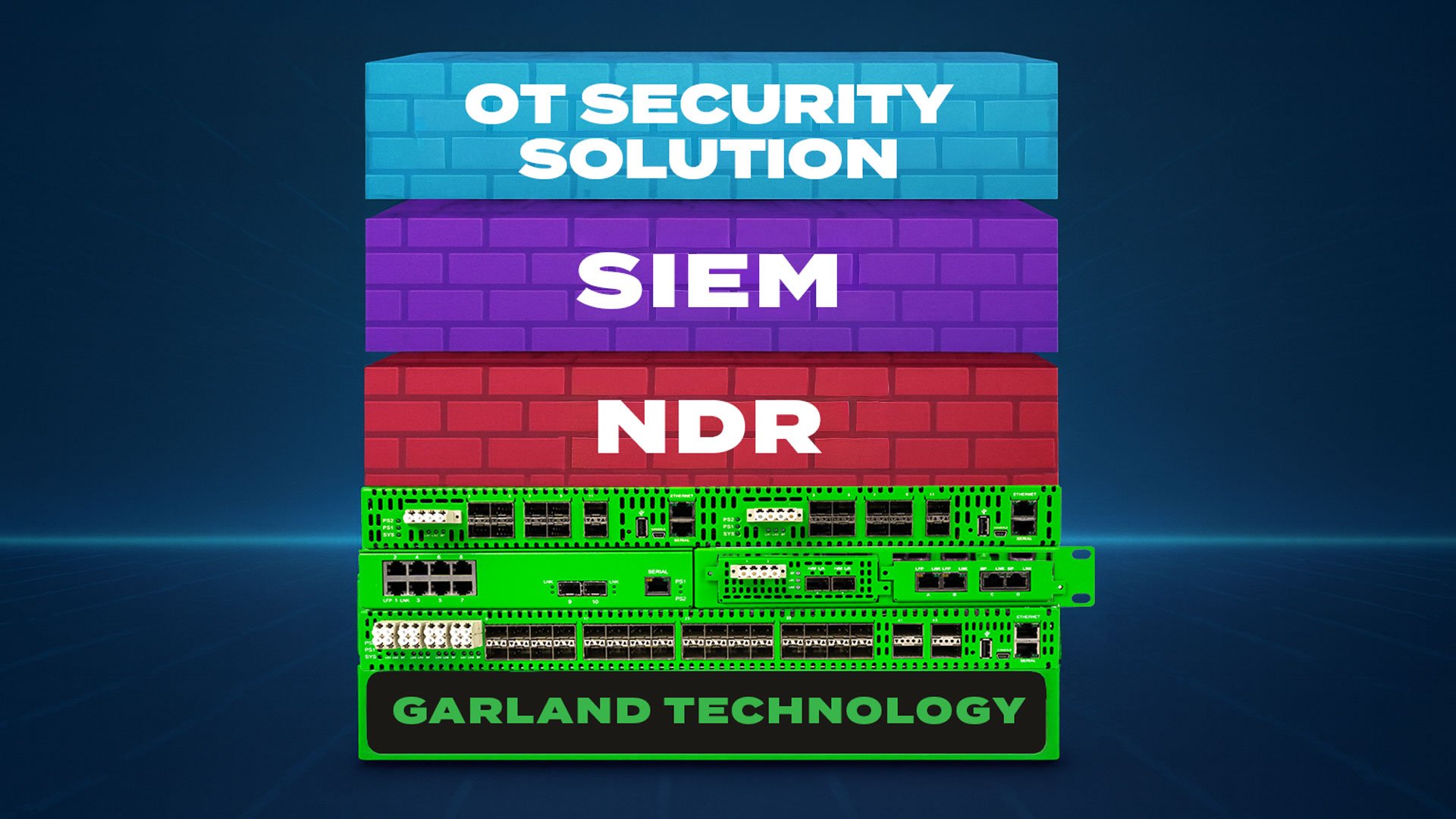
Benefits of Installing MSSP Sensors Utilizing Network TAP Visibility
Congratulations on the deal closing! You worked it for several months and convinced Customer A to install your MSSP Sensor. This Sensor’s objective is to plug into the customer’s IT network, capture...