

With so many components to a functioning network – performance, security, and monitoring, just to name a few – it’s easy to let what seem like minor details go unaddressed in your network design.
When you’re implementing expensive hardware and software, you can’t afford to let overlooked details related to data flow compromise your investments.
Keeping data and traffic flow at top of mind is essential to optimizing these enormous investments.
However, you may not be aware of certain limitations of a given device, nor the various ways to deploy or install it. With your daily demands, it’s difficult to stay current on the latest in network design.
Learn about support that helps you ensure the best flow of data and network traffic, maximizing the effectiveness of your high-priced devices.
In order to ensure the sanctity of your network, you must first answer several fundamental network management questions. These concern the presence of different applications, existing hardware, media and more.
Below are some sample questions Garland Technology would ask you to understand your network and needs:
With the answers to these questions, Garland Technology design experts create a whiteboard drawing (and later, a Visio drawing) to visualize the design of your network. Whether it’s Garland or you yourself, mapping out your network is critical to ensuring the flow of your data.
With a physical drawing, you should depict where traffic comes in, goes out and flows through. It can go to your distribution layer, server farms (which can access internet/desktop connections), or out to wide area network.
In essence, the data and traffic flow can be very complex.
A drawing helps you understand the flow of your network – essential to determining where to capture appropriate data and how to send it to appropriate devices, including:
Below is an actual drawing of what Garland produces for you.
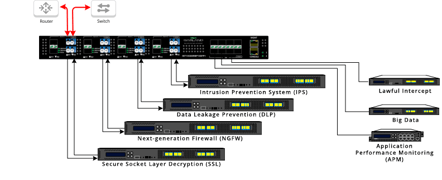
Whether it’s on your own or with the support of a network management and data access expert, take the necessary steps to flawlessly plan your network design and ensure the flow of data to your expensive devices.
Schedule a consultation to discuss your needs and map out a network design that ensures proper data access.
If the inline security tool goes off-line, the TAP will bypass the tool and automatically keep the link flowing. The Bypass TAP does this by sending heartbeat packets to the inline security tool. As long as the inline security tool is on-line, the heartbeat packets will be returned to the TAP, and the link traffic will continue to flow through the inline security tool.
If the heartbeat packets are not returned to the TAP (indicating that the inline security tool has gone off-line), the TAP will automatically 'bypass' the inline security tool and keep the link traffic flowing. The TAP also removes the heartbeat packets before sending the network traffic back onto the critical link.
While the TAP is in bypass mode, it continues to send heartbeat packets out to the inline security tool so that once the tool is back on-line, it will begin returning the heartbeat packets back to the TAP indicating that the tool is ready to go back to work. The TAP will then direct the network traffic back through the inline security tool along with the heartbeat packets placing the tool back inline.
Some of you may have noticed a flaw in the logic behind this solution! You say, “What if the TAP should fail because it is also in-line? Then the link will also fail!” The TAP would now be considered a point of failure. That is a good catch – but in our blog on Bypass vs. Failsafe, I explained that if a TAP were to fail or lose power, it must provide failsafe protection to the link it is attached to. So our network TAP will go into Failsafe mode keeping the link flowing.
Single point of failure: a risk to an IT network if one part of the system brings down a larger part of the entire system.
Heartbeat packet: a soft detection technology that monitors the health of inline appliances. Read the heartbeat packet blog here.
Critical link: the connection between two or more network devices or appliances that if the connection fails then the network is disrupted.