

The decision to use Network TAPs instead of relying on SPAN (mirror) ports can be the simplest, yet most important decision that must be answered for any network monitoring or security project. Case in point. The US Military knows the value Network TAPs provide, and that when it comes down to ensuring the effectiveness of a mission, TAPs are a must.
The US Army regularly participates in the Department of Defense’s War Fighter, an information technology exercise testing the command center’s ability to execute mission command and mission control tactical communications between units in the field.
During setup for a recent exercise, the team ran into immediate issues with their sniffers due to packet loss. This can be attributed to using the SPAN ports on the switches as the access method for the sniffer. The packet loss was due to configuration issues, which lead to the port being rendered permanently inoperable, and even caused the entire division’s headquarters building to go down. When it comes down to it, packets matter. Without having a complete copy of the packets, no matter what monitoring tools you’re using, it’s impossible to perform an accurate analysis of the project at hand.
It was these issues with the SPAN ports that led the 82nd Airborne Division to look for an alternative access method for their sniffers. After some initial research, they found that Network TAPs were the superior option when it comes to capturing network traffic. By using a TAP instead of a SPAN port, issues with packet loss and network downtime, that hindered the cyber security analysts ability to do their job, were eliminated.
The cyber security team was in communication with another Army division who recommended Garland TAPs, and lent the 82nd Airborne Division one of theirs for the exercise. And after additional research, the team was overnighted additional TAPs necessary to help complete the exercise. By selecting Garland Technology as the TAP provider for this exercise, the team was guaranteed 100% wire data for packet capture, which was the foundation for the entire communication exercise.
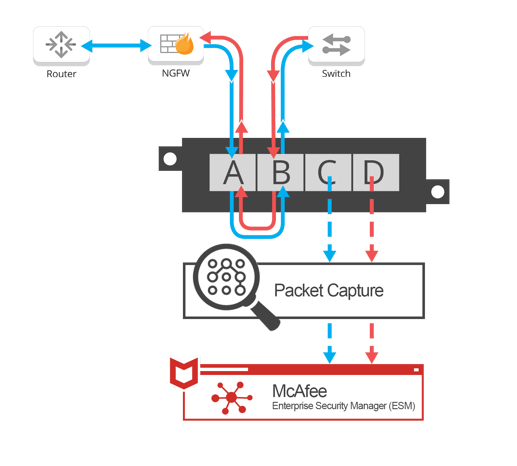
The 82nd Airborne Division used Garland Technology XtraTAPs during the DoD’s War Fighter to feed wire data to SecurityOnion’s sniffing interface to capture the traffic. Logs for the routers, switches, and anything else within the network infrastructure, was forwarded to a McAfee Enterprise Security Manager, ESM, which provided alerts if anything beyond the Palo Alto NGFW should be analyzed for any reason.
Garland is engineered, designed, made in America. With anything these days, especially with technology, you have to be fairly careful what you buy.” -Cybersecurity Chief, 82nd Airborne Division
Looking to add a visibility solution to your next deployment, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do!
If the inline security tool goes off-line, the TAP will bypass the tool and automatically keep the link flowing. The Bypass TAP does this by sending heartbeat packets to the inline security tool. As long as the inline security tool is on-line, the heartbeat packets will be returned to the TAP, and the link traffic will continue to flow through the inline security tool.
If the heartbeat packets are not returned to the TAP (indicating that the inline security tool has gone off-line), the TAP will automatically 'bypass' the inline security tool and keep the link traffic flowing. The TAP also removes the heartbeat packets before sending the network traffic back onto the critical link.
While the TAP is in bypass mode, it continues to send heartbeat packets out to the inline security tool so that once the tool is back on-line, it will begin returning the heartbeat packets back to the TAP indicating that the tool is ready to go back to work. The TAP will then direct the network traffic back through the inline security tool along with the heartbeat packets placing the tool back inline.
Some of you may have noticed a flaw in the logic behind this solution! You say, “What if the TAP should fail because it is also in-line? Then the link will also fail!” The TAP would now be considered a point of failure. That is a good catch – but in our blog on Bypass vs. Failsafe, I explained that if a TAP were to fail or lose power, it must provide failsafe protection to the link it is attached to. So our network TAP will go into Failsafe mode keeping the link flowing.
Single point of failure: a risk to an IT network if one part of the system brings down a larger part of the entire system.
Heartbeat packet: a soft detection technology that monitors the health of inline appliances. Read the heartbeat packet blog here.
Critical link: the connection between two or more network devices or appliances that if the connection fails then the network is disrupted.