
General Data Protection Regulation (GDPR) is a mandated regulatory standard designed to unify data privacy and security requirements. This regulation affects companies that provide services within the European Union; however, any company that provides services over the internet can be subject to this regulation. With the ubiquity of internet based services, whether it is social media, streaming content, shopping or accessing your personal records online, personal data privacy and security practices will need to be regulated. Adoption is currently taking place in other regions around the world while using GDPR as a model to scrutinize privacy and security practices.
Why does it matter to my organization?
GDPR was implemented on May 25th, 2018. Due to its regulatory nature, any company that does not comply to GDPR is subject to large fines: $23.3M USD (as of August 2018) or 4% of the total worldwide annual revenue of the preceding financial year, whichever is higher. Consequently, being non-compliant to GDPR can bring an organization to a negative light from the perspective of employees, business partners, customers and ultimately, the public. While applicable only to organizations providing services within the European Union, other regions around the world are using GDPR as a model to enforce regulations for the betterment of security and privacy. Due to the inevitable widespread adoption of GDPR, ensuring that your network and services are compliant will be mandatory. Preparing your organization early is key to avoiding trouble with GDPR or its regional variant.
This regulation is designed to protect individuals that access and use your organization’s service from privacy breaches, identity theft, credit card fraud, ransoms, blackmailing and many others. Many online services typically handle sensitive personal information as a way of authentication.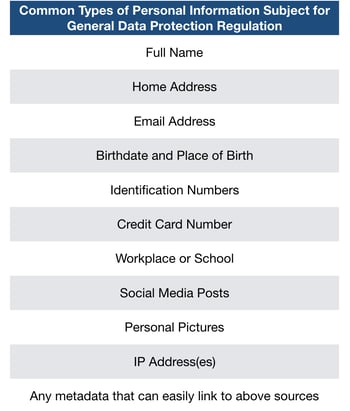
What is the reason behind GDPR?
GDPR replaced the Data Protection Directive which was designed to regulate how companies handle and protect personal data. However, the Data Protection Directive served more as a “guidance/recommendation” to companies and was not enforceable enough to actually regulate as it was initially intended to do.
Before GDPR, organizations that were previously attacked and had their customers’ personal data compromised took at least 4 months (in some cases 1-2 years) before disclosing the incident publicly or to a respective regulating body. GDPR enforces that organizations should disclose the incident at most 3 days after it happened and have the substantial amount of evidence to determine the root cause and the extent of that particular incident. If the organization fails to provide both, then the organization will be sanctioned.
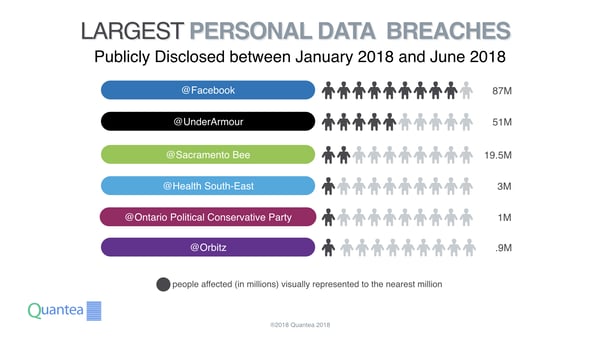
Facebook, Under Armour and Orbitz – what do they have in common? All three organizations suffered incidents where millions of individuals are affected. Without a strong regulation in place, many of these data breaches can happen for months to years without the organization taking reasonable action. There are plenty of publicly disclosed high profile breaches between January to June 2018; with all of them having incidents starting 2017 and earlier but decided to disclose in 2018.
What does it take for my organization to be penalized for GDPR non-compliance?
There are many ways an organization can be sanctioned for being GDPR non-compliant:
- Not properly taking measures of improving data handling and security per GDPR guidelines
- Sharing (even unintentionally) private/personal information to third parties without disclosing to the subject end-user
- Collecting private/personal information and not using it purposely within the nature of the service
- Failing to disclose to the end-user, in practical detail, all the types of information being collected and how it is being used
- Failing to provide the end-user an easy way of deleting and accessing their information
- Not disclosing to the end-users and the regulating body that the services were compromised/hacked and what information is affected within 3 days from the date of the incident
The quickest way your organization can be fined for non-compliance and possibly lose public trust is by leaking private/personal information as a result of a security breach by not implementing data handling and security practices within the GDPR standard.
For a majority of companies that are not yet GDPR compliant, it only takes a single successful breach to raise a “red flag” for the regulatory body to start scrutinizing on the organization which will lead to an eventual sanctioning.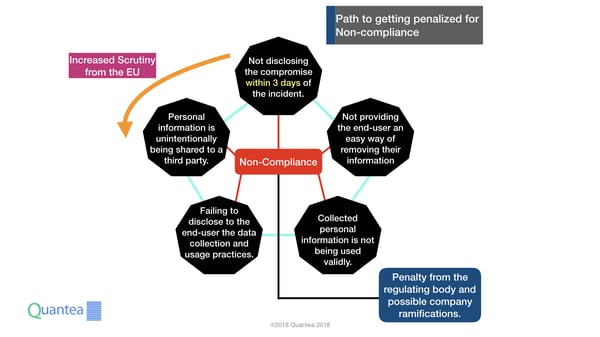
Achieving GDPR Compliance
How your organization can stay out of the headlines
Besides changing or updating your organization’s privacy policy, GDPR compliance has two primary components: privacy and security. Ensuring privacy means assessing data subject rights to consent, access, correct, delete and transfer personal data. Readiness in security includes identifying vulnerability, recent/reoccurring breaches and validating the current strategy.
In terms of networking and security, here are the essential goals to becoming a GDPR compliant organization:
- Attain Complete Visibility: Have widespread visibility and awareness of data transactional activities across the network.
- Have Traffic Data Be Readily Available for Audit: Be able to provide incident data (in its entirety) and have it available for the internal or regulatory body.
- Gain Network “Self-Awareness”: Routinely determine whether your organization has crossed the line when it comes to compliance. Have a method of performing a self-audit of personal (and private) data utility, transparency whether internally or externally to an authorized/unauthorized third party and purposeful usage of that said data.
- Assess and Validate Current Strategy: Utilize the capabilities to get to the three goals above to determine whether your organization’s current security strategy is more than enough to deter recent and reoccurring data breaches.
One good point to consider is even when the organization is sanctioned, the regulating body can provide avenues of leniency given that the company has evidence that they are taking measures in good faith. This means an organization can minimize and mitigate against the potential consequences and sanctions that they could face with a genuine (and proven) commitment and effort to meeting their GDPR obligations.
Achieving compliance should not be a monumental undertaking; by utilizing Garland’s visibility solution and Quantea’s network monitoring solution, any organization will be a step ahead in attaining GDPR compliance.
Garland’s inline Network TAPs ensure the highest network visibility by providing data at line rate to a monitoring device, like Quantea’s and providing connectivity to an inline security device. Quantea provides trust and transparency by recording and indexing 100% of whole traffic data while providing the organization ease of accessibility of data for auditing and incident tracing. By utilizing the Quantea’s RESTful API, internal data auditing and assessment can be automated by creating advanced triggers to search and replay particular data types to determine whether there is a personal data loss during a breach incident. Having these capabilities at an arm’s reach is necessary in attaining GDPR compliance.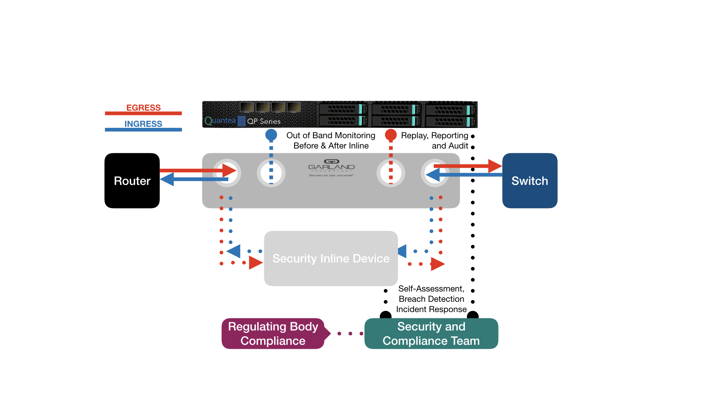
Capabilities:
- Augmented network visibility at 1/10/40/100Gbps
- Inline and bypass capabilities
- Reliably monitor up to +100Gbps from devices, applications, users and servers
- Harness days and months of traffic data for auditing and incident tracing
- Built-in search engine filters data that is subject to GDPR
- Re-evaluate incidents and assess current security strategy by using traffic replay
- Generate reports based on the applications, devices and data that took place during a breach incident
Becoming GDPR compliant starts with monitoring the current state of your network to get a solid understanding of what's going on in the network and where your data is going. [Download Garland's whitepaper, The Ultimate Guide to Network Monitoring for an overview on network monitoring tools and best practices.]

