

Computer networking terminology can become overly fickle once vendor products get into the mix. To help alleviate the confusion, we’re going to go over how Garland Technology approaches terminology and hopefully clear up some understanding about Network TAPs.
Both terms mean Bi-Directional but are distinctly different when used in a Network TAP context.
Bi-Directional refers to the actual flow of network traffic between two networking devices as they send and receive traffic. The “Bi-“ in Bi-Directional refers to “two”, meaning that there are two flows of traffic going over the cable at the same time. These directions of traffic are often given cardinal directions (North & South, East, & West) to help visualize traffic flow from a network design perspective.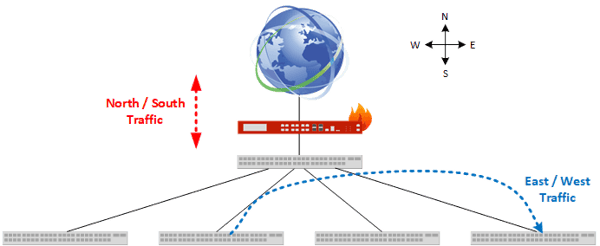
From a Network TAP perspective these flows of traffic represent data traveling over the cable that can be captured and copied. Depending on which TAP and TAP Mode that is being used determines how the different flows of traffic are distributed to Network Tools or Aggregators.
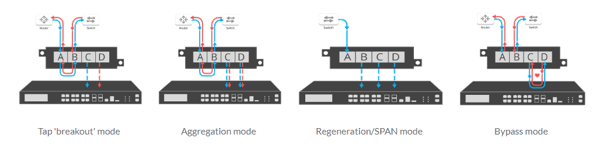
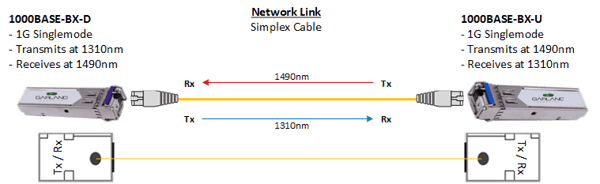
“BiDi” refers to a type of transceiver that can place two different directions of traffic on a single fiber cable.
BiDi transceivers allow companies to extend the life of existing LC Multimode Fiber by enabling it to support 40 Gbps throughputs instead of requiring an infrastructure upgrade to MTP/MPO cables.
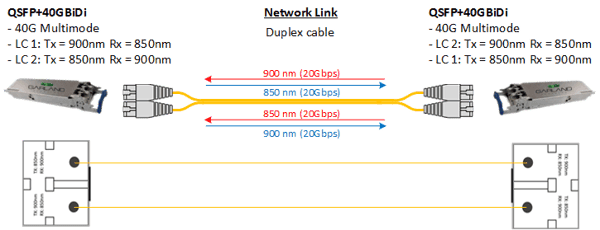
Special BiDi Network TAPs are needed when monitoring BiDi network links. These BiDi TAPs have splitters that can isolate out the wavelengths being used over the network link, allowing each direction of data to be captured as its own dedicated monitor link.
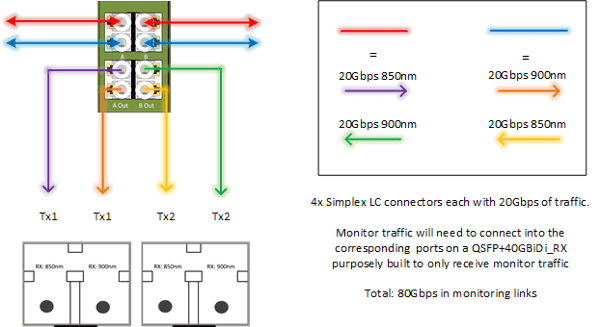
While all our TAPs can see and capture Bi-Directional traffic, not all TAPs are equipped to deal with BiDi traffic generated from BiDi transceivers. Being aware of terminology like this is an important step in making sure you’re network monitoring solution is the correct one.
Looking to add Network TAPs to your security deployment, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do!
If the inline security tool goes off-line, the TAP will bypass the tool and automatically keep the link flowing. The Bypass TAP does this by sending heartbeat packets to the inline security tool. As long as the inline security tool is on-line, the heartbeat packets will be returned to the TAP, and the link traffic will continue to flow through the inline security tool.
If the heartbeat packets are not returned to the TAP (indicating that the inline security tool has gone off-line), the TAP will automatically 'bypass' the inline security tool and keep the link traffic flowing. The TAP also removes the heartbeat packets before sending the network traffic back onto the critical link.
While the TAP is in bypass mode, it continues to send heartbeat packets out to the inline security tool so that once the tool is back on-line, it will begin returning the heartbeat packets back to the TAP indicating that the tool is ready to go back to work. The TAP will then direct the network traffic back through the inline security tool along with the heartbeat packets placing the tool back inline.
Some of you may have noticed a flaw in the logic behind this solution! You say, “What if the TAP should fail because it is also in-line? Then the link will also fail!” The TAP would now be considered a point of failure. That is a good catch – but in our blog on Bypass vs. Failsafe, I explained that if a TAP were to fail or lose power, it must provide failsafe protection to the link it is attached to. So our network TAP will go into Failsafe mode keeping the link flowing.
Single point of failure: a risk to an IT network if one part of the system brings down a larger part of the entire system.
Heartbeat packet: a soft detection technology that monitors the health of inline appliances. Read the heartbeat packet blog here.
Critical link: the connection between two or more network devices or appliances that if the connection fails then the network is disrupted.