
In April 2021, a ransomware attack shut down the largest pipeline network in the United States. Colonial Pipeline, which supplies almost 50% of the Northeast’s energy needs, lost nearly 100 gigabytes of proprietary data. In light of the multi-day shutdown of a major fuel distribution network, the NIST Cybersecurity Framework (NIST CSF) is generating renewed interest among energy stakeholders.
To date, ransomware attacks on the energy industry continue to multiply, targeting vulnerable IT systems to incapacitate critical energy infrastructure. Disturbingly, 50% of attacks on global energy infrastructure occur in the United States.
Most organizations (47.8%) in critical infrastructure sectors map their control systems to the NIST CSF. Other popular frameworks include the IEC 62443 (32%), NIST 800-53 (31.5%), NIST 800-82 (29.6%), and ISO 27000 Series (29.1%). However, in the last two years, the MITRE ATT&CK® ICS framework has emerged as a force multiplier in responding to cybersecurity threats, particularly in the oil & energy sector.
Before we explore the MITRE ATT&CK framework, we’ll look at new updates and overview the wide range of industrial compliances, including cybersecurity standards and frameworks that safeguard the critical infrastructure sector.
Pipeline cyber defense: The new, synergistic partnership between NISTIR 8374 and API std 1164
On June 17, 2021, NIST released a preliminary draft of its new Cyber Security Framework Profile for Ransomware Management (NISTIR 8374). In September, it produced a revised draft — public comments on this new draft were closed on October 8, 2021.
The NISTIR 8374 provides an actionable roadmap to help organizations respond to and reduce their susceptibility to ransomware attacks. It outlines basic cybersecurity controls and defensive measures mapped to the five elements of the NIST Cyber Security Framework: identify, protect, detect, respond, and recover.
The Ransomware Profile is specifically suited for organizations that have already adopted the NIST Cybersecurity Framework and NERC-CIP (Critical Infrastructure Protection) standards.
Meanwhile, to underline the energy sector’s commitment to securing the nation’s critical infrastructure assets, the API published its 3rd Edition of Standard (Std) 1164 on August 18, 2021. According to API Senior Vice President of API Global Industry Services (GIS) Debra Phillips, “The new edition API Std 1164 builds on our industry’s long history of... collaborating with the federal government to protect the nation’s vast network of pipelines and other critical energy infrastructure from cyber-attacks.”
This third edition also aligns with the objectives of the Justice Department’s newly created Ransomware and Digital Extortion Task Force.
Together, the new NISTIR and API STD 1164 updates serve as a powerful means of securing the nation’s critical infrastructure.
How the MITRE ATT&CK® ICS framework fits within the energy IT/OT security landscape
An effective governance blueprint can strengthen an organization’s response to IT/OT cyber-related risks.
This is where the ATT&CK® ICS framework comes in. This new framework provides the basis for creating a successful defense strategy against the tactics and techniques threat actors use. According to the SANS 2021 OT/ICS Cybersecurity survey, 47% of respondents leverage MITRE ATT&CK® ICS to mitigate IT/OT cybersecurity incidents.
Although the NIST Cybersecurity Framework provides a comprehensive governance structure for identifying and responding to threats, it doesn’t offer a template for anticipating ransomware behaviors, detecting stealth reconnaissance activities, isolating attacks, or conducting a post-mortem analysis of cybersecurity incidents. However, the ATT&CK® ICS framework does.
Together, the NIST Cybersecurity and ATT&CK® ICS frameworks serve as a critical basis for mitigating the risks of IT/OT convergence in the energy sector.
Common cybersecurity standards industrial teams map control systems to
NIST Cyber Security Framework (CSF): This is a five-function approach to mitigating an organization’s cyber security risks. It’s usually combined with the following standards:
- ISA/IEC 62443: This framework is aimed at reducing current and future security vulnerabilities in industrial automation and control systems.
- NIST 800-53: These security and privacy controls are aimed at supporting the federal government and all critical infrastructure.
- NIST 800-82: This guide provides a roadmap for securing industrial control systems.
- ISO 27000 Series: These standards are focused on helping organizations strengthen their information security practices.
- CIS Critical Security Controls: These are a set of actions that help organizations secure their data against cyber attack vectors.
- NERC CIP: These standards are aimed at protecting our national power grid.
- NIS Directive: This legislation aims to bolster cybersecurity across the EU.
- MITRE ATT&CK ICS Framework: This is a globally accessible knowledge base of tactics and techniques used by cyber threat actors.
- NISTIR 8374 (Draft): This guide is aimed at helping organizations manage their risks of ransomware attacks.
Other frameworks include:
- GDPR: This legislation addresses data privacy and security in the EU.
- Cybersecurity Maturity Model Certification: An assessment program that measures the maturity of cybersecurity processes for over 300,000 organizations that support the DOD’s Defense Industrial Base.
- C2MC (Cyber Capability Maturity Model): This tool evaluates the strength of cybersecurity practices across all of America’s critical infrastructure sectors.
- NIS Directive, ANSI/AWWA G430-14: This standard defines the minimum requirements for a protective security program for our nation’s waste and wastewater facilities.
- Qatar ICS Security Standard: This standard underlines security controls for industrial automation systems in Qatar.
- Chemical Facility Antiterrorism Standards (CFATS): This regulatory program targets security at high-risk chemical facilities in America.
- ENISA Guide to Protecting ICS (EU): This manual serves as a guideline to mitigate attacks on industrial control systems across the EU.
How deploying the right asset management, threat detection & response tool promotes a more secure industrial network
To satisfactorily comply with these important OT compliances, energy-related organizations must deploy the right asset management, threat detection, and response tools.
Today, gaining full asset visibility for discovery and management begins with 100% packet visibility, afforded by network TAPs (test access points). Relying on switch SPAN or mirror ports is not going to cut it in today’s environment, as they were not designed for continuous monitoring.
Complete visibility is the foundation of an effective cybersecurity threat detection and response solution. Threat detection and response are more critical than ever due to IT/OT convergence in the energy sector. For example, the IoT sensors that allow oil & gas firms to remotely monitor worker safety on offshore rigs rely on internet connectivity, which offers multiple security loopholes that endanger OT infrastructure.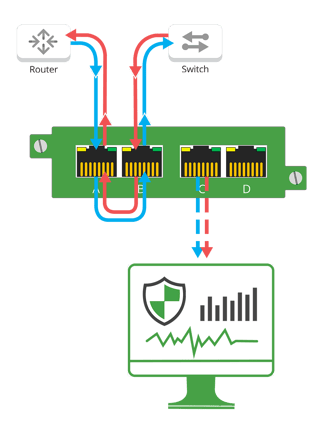
Industrial teams turn to Network TAPs to provide packet visibility, not only because of the clear advantages over SPAN but because they are easy to deploy, rugged plug-and-play devices that are passive or failsafe and do not affect current configurations. Network TAPs are added to provide full-duplex copies of network traffic 24/7/365 that are secure and can provide unidirectional as well as media conversion and traffic aggregation options. All designed to make asset inventory and threat detection tool deployments seamless, ensuring compliance and security standards are met.
Looking to add network TAP visibility to meet compliance, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do.


