Provide Visibility and Improved Operational Efficiency for Banking Cloud Endpoints
February 27, 2020

With the migration to cloud networks underway, companies are focused on the long term benefits of lowering their costs, utilizing faster innovation and improving customer satisfaction. Many industries have been taking a wait and see approach due to maturing technology and the limited monitoring and security capabilities available, but they are busy testing and planning for the eventual leap to the cloud. The banking industry - known as a leader in technical innovation - is again at the forefront. Banks must design solutions that protect sensitive and valuable customer assets and comply with stiff regulations and security protocols along with a high-volume of data.
With our new Garland Prisms cloud TAP solution, Garland Technology has been busy working with many financial and banking companies who are designing such solutions and were lacking much-needed visibility into the applications running in their virtualized environment.
That was the case recently with one major banking customer who needed better visibility into new branch deployments of teller station and ATM endpoint devices. Their architectural goal is to get visibility to their individual instances throughout their network instead of monitoring all of their data as a whole, which was causing bottlenecks and blind spots. The ultimate goal was improving their IT operational efficiency and customer experience while achieving regulatory compliance. Here’s how we did it.
Performance, Security and Regulatory Considerations
First, with improving operational efficiency, we wanted to provide access to each individual endpoint to be able to properly monitor the performance, allowing the IT team to have visibility into latency issues. Being able to pinpoint that when “Teller A” accessed a customer’s bank account, they were experiencing 1000 milliseconds of latency, providing a less than optimal experience. Setting a baseline, so they know that if “Teller A” wants to have a good experience processing a customer’s account, they need to be under 20 milliseconds of latency. Analyzing this granular data not only improves the performance, efficiency, and productivity of the public-facing representatives but allows the IT team the visibility to continually monitor and scale into the future.
Next, cybersecurity is an obvious issue to address. Providing the added access and visibility for each endpoint, also ensures the security monitoring tools in the solution can real-time monitor and quickly detect any security breach attempts to protect privacy or trigger incident response.
To achieve regulatory compliance, banks must comply with many local, state, federal and international regulations, like Sarbanes-Oxley (SOX), GLBA (Gramm-Leach-Bliley Act) and PCI (Payment Card Industry Data Security Standard). Again, providing visibility into the vast amount of generated data helps provide the granular insight needed for audit reports.
>> Watch Now: Garland Prisms Traffic Mirroring [Free Demo]
Providing Access and Visibility in a Virtual Environment
In on-prem data centers, architecting traditional network TAPs and packet brokers have become standard operating procedure for providing complete network visibility and feeding your network and security tools. In a virtual environment, this is important if not overlooked pain point for many companies migrating to the cloud. You have your AWS, Azure or Google platforms, can’t they just mirror the traffic? In this maturing environment, Virtual TAPs can be limited and pricy, and AWS is the only cloud platform with a viable vTAP yet it has many limitations. Garland Prisms not only outperforms all existing virtual TAPs, but you can replicate 1:many sources at a very cost-effective rate.
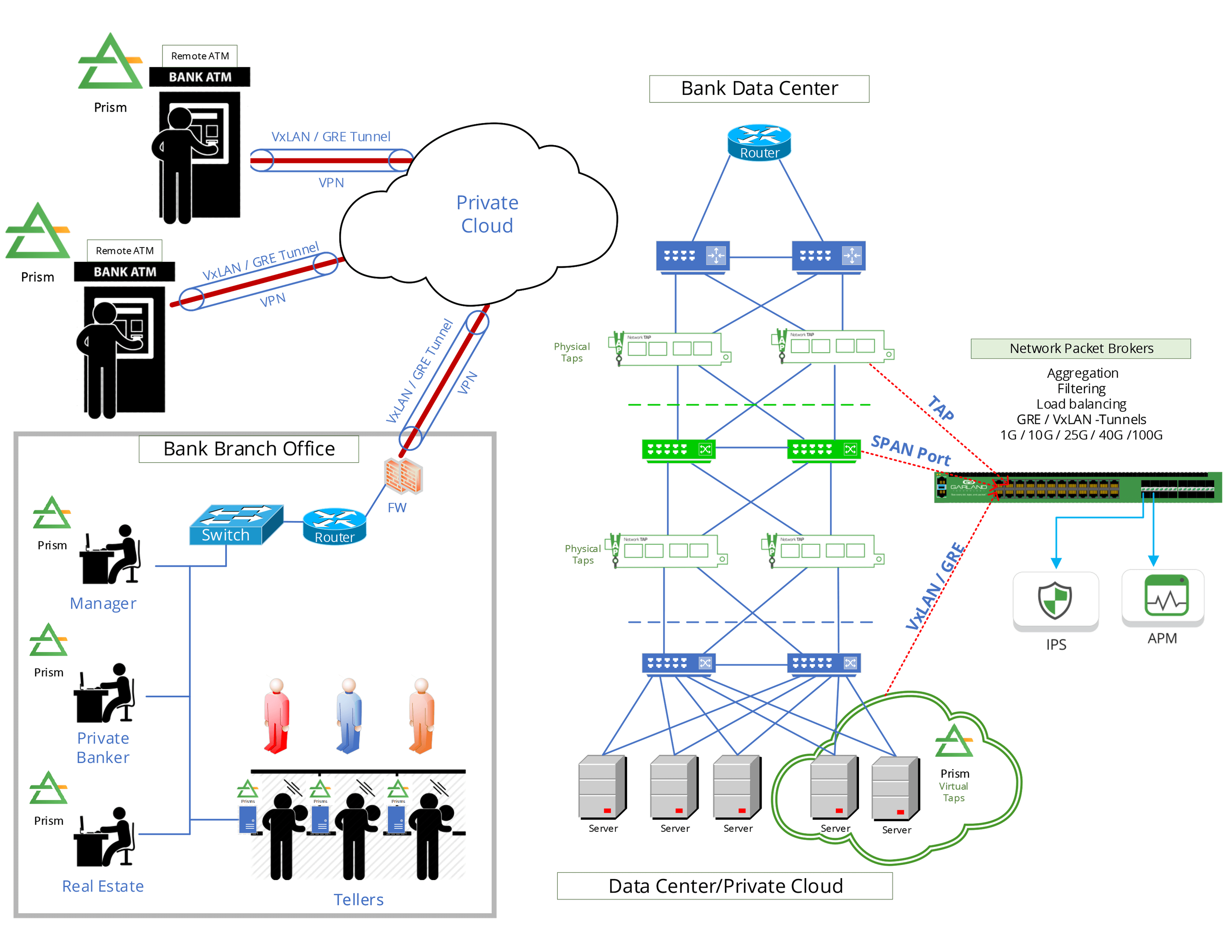
Architecting to the Solution
In this deployment, we used application performance monitoring tools, like Splunk or Flowmon to provide critical insight into IT services, applications and infrastructure performance needed to achieve our goals to improve operational efficiency, customer experience, achieving regulatory compliance, while using threat detection and response applications like Extrahop.
The first challenge within a client-server architecture was providing access to all of the endpoint devices, each teller, ATM and employee stations across the full deployment. We deployed a Garland Prisms sensors into a VM for each endpoint device. This allows us to take the one VM instance and mirror the source data to 1-or-many tools, in this case, we sent one stream to Splunk, Flowmon, and Extrahop where needed. We were easily able to deploy this across the whole network, leaving us a blueprint for scaling this footprint for future growth.

In this solution, there were three key components to consider: the agents, the VMs and the Garland Prisms sensors, the second would be the controller, Garland Prisms has either a SaaS option or a private “air-gapped” controller, where you easily manage the source data, the third component is the destination, meaning the different monitoring and security tools being used. We are finding this design useful in many other deployments because of its flexibility and ease of use.