
Until you remember that you can go to the source to investigate data transmission.
That's right, I'm talking about getting your hands dirty and diving into the minutiae of your network.
To investigate the root cause of your application's poor performance, you need to access the packet data.
What is packet data?
Network packets are a granular unit of data used to distribute information across the internet and network. These packets are broken down into two general sections — a header or control information and the payload or user data.
The header contains information for delivering the data in the payload, like Ethernet ll segments, where the DMAC and SMAC addresses are defined; if there is a VLAN or not; and IPv4 or IPv6 protocols where the Source IP and destination IP address are defined — these are considered layer 2-3 data.
The payload is the data that is the actual intended information, the end user videos, phone audio, images and information data — like the page you are reading right now. This layer 4 data can include user data protocol (UDP).
Depending on the service, TV, computer, or mobile device, millions of packets are transmitted in a certain sequence and need to arrive in the same sequence. Receiving packets out of sequence or experiencing dropped packets, leads to network latency, slow service, interrupted or pixelated experience.
But sending data over a network is just like shipping a package: you have to follow certain rules and go through a specific process before your final product gets delivered. You can think of this process as the import/export laws of the internet.
This set of rules, known as the Transmission Control Protocol/Internet Protocol (TCP/IP), is called a protocol stack. It's composed of four layers:
- Application protocol is the first TCP/IP layer. It defines and standardizes how data gets sent over your network.
- Transmission control protocol (TCP) is where your data packet is assigned port and sequence numbers to ensure that it arrives at the correct application, in the correct order.
- Internet protocol (IP) assigns source and destination IP addresses to your data packets. It also determines the best route for your data to travel over your network so it can reach its final destination efficiently.
- Hardware is the machine that receives all this information to reassemble your data packets in the correct order.
To interpret what's happening with your data packets as they travel through these layers over your network, pinpointing network latency or dropped packets, you need a packet analyzer.
What is a packet analyzer?
Packet analyzers, also known as packet sniffers or network analyzers, are a network monitoring tool that examines data traffic moving in and out of the network. These tools analyze network performance issues that can lead to traffic bottlenecks, network downtime, and other common performance issues that ultimately effect end-user experience and a companies productivity.
Continuing with our shipping analogy, you can think of packet analyzers as the gate agents and security scanners in the data transportation process. They work behind the scenes to ensure everything runs smoothly on your network.
Packet sniffers are a go-to tool for everything from making sure network traffic is routed correctly, to ensuring employees aren’t using company internet time for inappropriate websites. Packet analyzers also help detect potential network intrusion by looking for network access patterns inconsistent with standard usage.
In a process known as packet capture (PCAP), analyzers snag packet data as it moves over your network. It saves a copy of this data as a file on your monitoring device. You can analyze these copies of your packet data, to detect usage spikes, suspicious data transfer, and inconsistent network performance.
What are the advantages of packet sniffing?
Aside from achieving network visibility by having all your data on hand, there are a handful of other huge benefits you can achieve through packet sniffing.Find the root cause of various issues to secure your network
When you have access to your packet data, you can dig into the root cause of network issues. Thinking like a good threat hunter, you can familiarize yourself with typical traffic patterns and use your knowledge to identify inconsistencies.
When you understand your standard network performance, you can also use packet analyzer data to detect network vulnerabilities. When you know where you can improve, you can bolster your network security to prevent future threats, issues, or attacks.
Better understand your network speed
Armed with your PCAP analysis, you can figure out the average time it takes for a packet to travel across your network. Using these numbers, you can more quickly and easily figure out the source of any network slowdowns. When you understand the source, you can determine which applications are impacted and take action to fix any issues.
Identify inefficient network usage
Packet analyzers can help you categorize the traffic on your network. With this data, you can identify non-business uses of your network, like visits to social media sites, that might slow your network performance.
How do Packet Sniffers access the Packets?
There are two different methods you can use to access packet data: network TAPs (test access points) and port mirroring or switch port analyzers (SPAN).
We’ve already covered the differences between network TAPs and SPANs; but to recap how each functions to perform PCAP analysis.
Network TAPs
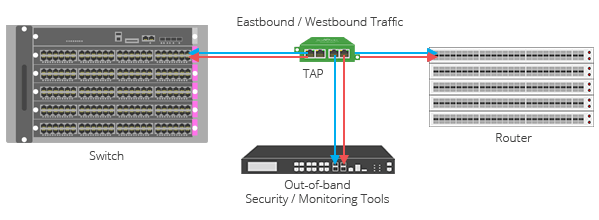 Network TAPs sit between devices in a network and send complete copies of data packets to your analyzer device in real time. Unlike SPAN, TAPs don't alter data when they make copies to send to your monitoring device. This lack of alteration means TAPs can provide accurate timestamps and errors, which makes analysis and auditing much easier.
Network TAPs sit between devices in a network and send complete copies of data packets to your analyzer device in real time. Unlike SPAN, TAPs don't alter data when they make copies to send to your monitoring device. This lack of alteration means TAPs can provide accurate timestamps and errors, which makes analysis and auditing much easier.
Considered the industry best practice for packet visibility, “EMA recommends that enterprises use TAPs as much as possible in the access layer to avoid network performance impacts and assure packet fidelity.” -EMA [Enterprise Management Associates]
SPAN Ports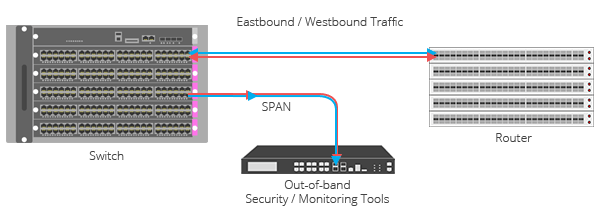 The SPAN method also creates a copy of data sent from one port to another of a network segment. However, SPAN is not recommended for networks with high throughput, as it was designed for lower volume spot checks. If your designated SPAN port is overutilized, it can drop and duplicate packets. These dropped and duplicate packets can make thorough, accurate analysis difficult or impossible.
The SPAN method also creates a copy of data sent from one port to another of a network segment. However, SPAN is not recommended for networks with high throughput, as it was designed for lower volume spot checks. If your designated SPAN port is overutilized, it can drop and duplicate packets. These dropped and duplicate packets can make thorough, accurate analysis difficult or impossible.
Looking to add network TAP visibility to your packet analysis, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do.


