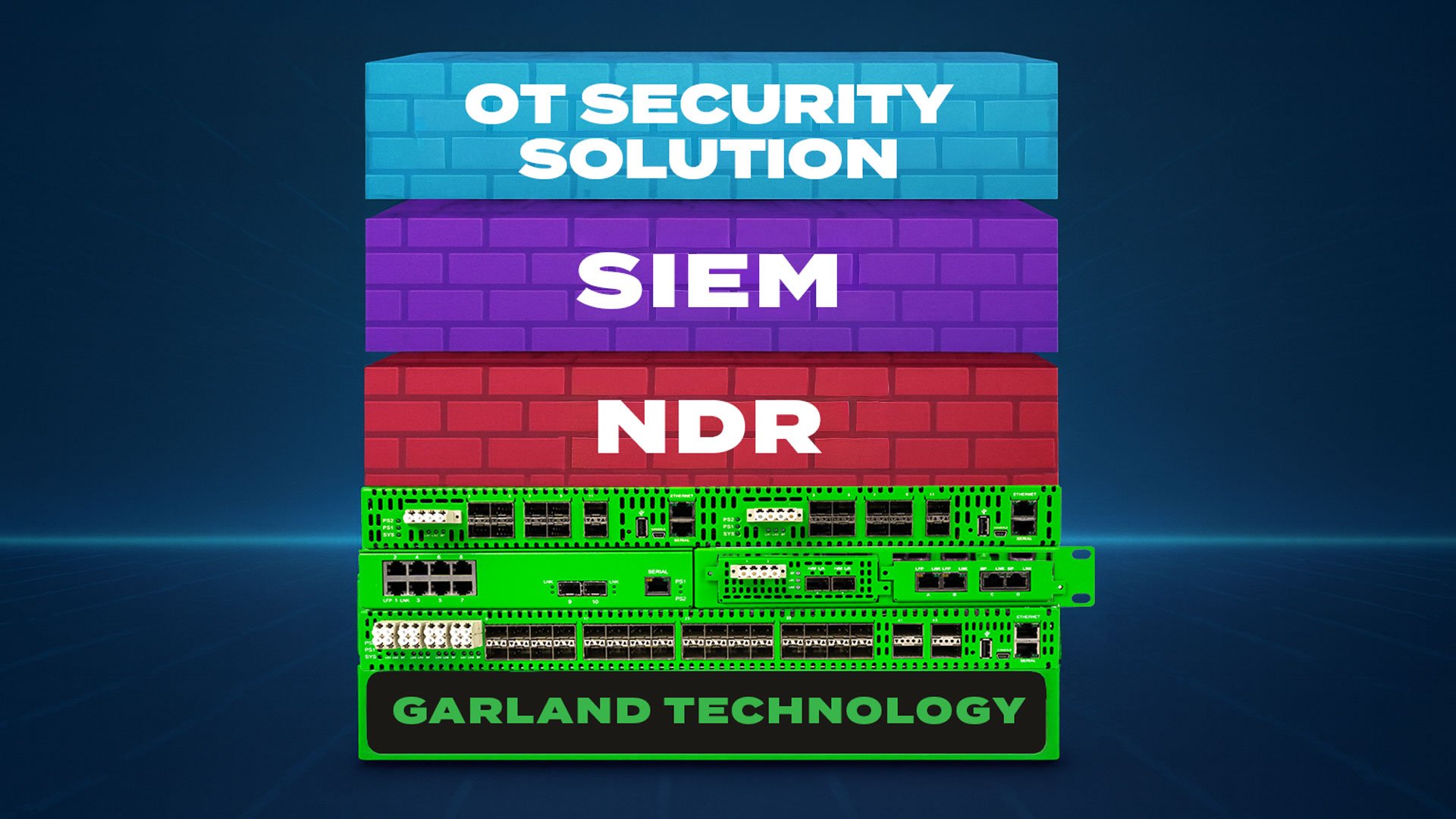
Network Monitoring and Incident Response for SMBs: Beyond Alert Fatigue
Editor’s Note This blog was written by Garland Technology’s channel partner OT Cyber Direct. It is part of a 5-part series detailing recommendations for SMBs (small and medium sized businesses) to...