
2020 was a watershed year for IoT; for the first time ever, IoT connections like connected industrial equipment and home devices outnumbered non-IoT connections (smartphones, laptops, and desktop computers). And while analysts have predicted this arrival for some time now, no one could have anticipated the timing, right in the middle of a global pandemic. For better or for worse, IoT has now taken the lead as the most prolific of internet users.
Unfortunately, the pandemic was also the backdrop for a record-breaking year for healthcare-related cyber attacks, spurred by the massive shift to remote work, continued adoption of bring-your-own-device (BYOD) policies, and other lockdown-related drivers. More connected medical devices and the rise of smart hospital facilities management have put healthcare IoT in the crosshairs of cyber attackers; for this reason, healthcare IoT networks require equal if not more monitoring and scrutiny as enterprise IT networks, given the nature and criticality of their operations.
Crucial Visibility into Healthcare IoT Networks
Hospital IT environments play host to a myriad of workstations, devices, and sensor nodes; if designed correctly, different classes and types of devices will be situated on different network segments/subnets. For example, a more secure network may be in place for connected devices for the monitoring of patient vitals (think connected blood glucose monitors, pulse oximeters) while another network may host fall detection monitoring devices and other physical patient monitoring systems. Because patient safety is at stake here, healthcare IT must maintain a high degree of confidence in their data and trust that it has not been altered. For example, medical IoT devices for patient monitoring may be compromised and return false values, or none at all. Network monitoring is therefore critical for maintaining integrity and awareness in healthcare IoT networks.
Threat Monitoring on the Edge
The most direct way to monitor the edge network for integrity is to inspect the network traffic itself, packet by packet. This can be accomplished by using an intrusion detection system (IDS): which is a cyber monitoring sensor consisting of closed or open-source software (e.g, Bro or Suricata) or a hardware appliance that monitors traffic moving on networks and through systems to search for suspicious activity and known threats.
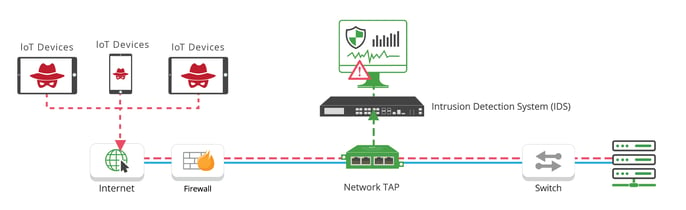
Diagram: Traffic flow of a hacker triggering an IDS solution with Network TAP visibility
The IDS receives all the network traffic for inspection by way of either a port mirror or network TAP, with the latter being preferred in cases where high throughput spot-checking is necessary. In fact, network switches may drop mirrored packets when oversubscribed or under heavy use, as SPAN traffic is considered low priority processing. On the other hand, network TAPs make an exact copy of network traffic and provide packet visibility to the IDS and other out-of-band monitoring tools. IDS solutions used in conjunction with network TAPs enable IoT asset owners to monitor their sensor networks for anomalies and suspicious activity.
In the case of ransomware, a malware-infected host will scan the hospital network and attempt to enumerate exploitable vulnerabilities. With an IDS connected via network TAP, an alert is generated based on this malicious behavior, allowing for proper mitigation of the threat before the ransomware propagates. This scenario is all too common in healthcare settings: according to a recent Checkpoint Security report, ransomware attacks have jumped 45% since early November of 2020.
As connected things in the healthcare space become even more commonplace in the coming years, IDS with TAP Visibility will continue to be critical items in the medical cybersecurity professional’s tool chest. Garland Technology’s full platform of network TAPs allows IDS solutions to gain unfettered access to network traffic without the risk of altered response times, duplicate traffic, and other issues that come with a SPAN configuration.
Looking to add TAP visibility to your out-of-band security monitoring solutions, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do.


