
If you have been in networking long enough, you may have heard the phrase “breathe new life into old tools.” This concept is simple - security and monitoring tools only perform as well as the data they process. So solely relying on SPAN (Port mirroring) for packet visibility is well known to present issues that minimize tool performance like dropped packets and introducing blindspots. Also, as network speeds advance, tools that operate at lower speeds of 1G and 10G may become obsolete.
Therefore, feeding your old tools with packets from Network TAPs ensures they perform how they were intended: processing complete packet data without loss. Also, adding network packet brokers (NPB) to aggregate, load balance, and optimize the traffic, relieves any additional processing burden on the tools, allowing teams to utilize those lower speed tools longer while ensuring they are running at peak performance.
As cybersecurity demands grow, as companies incorporate virtual traffic, and with the growth of higher traffic speeds and greater complexity, teams are looking to manage IT budgets more effectively. Especially trying to improve the return on investment of their existing network - not just the tools, to ultimately increase their spend on security solutions and headcount.
Improving Your NBP Return On Investment
Companies may have their core infrastructure in place, have their backbone tools and network packet brokers working well, but face blind spots. Likewise, there may even be performance or security issues that demand additional visibility into new segments in the network to expand their tool’s coverage. More visibility links lead to port retention on the core packet brokers, leading to expansion of core packet brokers and to an even larger return on investment than was originally anticipated.
Unfortunately with some packet broker vendors, operation costs hide in plain sight and can be very hard to get under control. License fees and lock-ins unintentionally expand the footprint and reduce the ROI of the initial investment.
Many times the Garland Technology team is brought into a project to add additional tapping visibility, deduplication, and traffic aggregation to an existing infrastructure because:
- We are the trusted leader in network TAP innovation: if you have a unique need, we have a TAP for it.
- Our packet brokers are very cost-effective: you can ‘deploy what you need when you need it.’
With Garland’s help network architects can improve not just the security and monitoring tools at the top of the stack but also breathe new life into those existing core packet brokers.

Enhancing Existing Deployments
Adding network TAPs, deduplication, and traffic aggregation to existing deployments in a cost-effective way bolsters the original investment while improving the solution's overall effectiveness. But how does that work, and why wouldn’t we just use the same vendor?
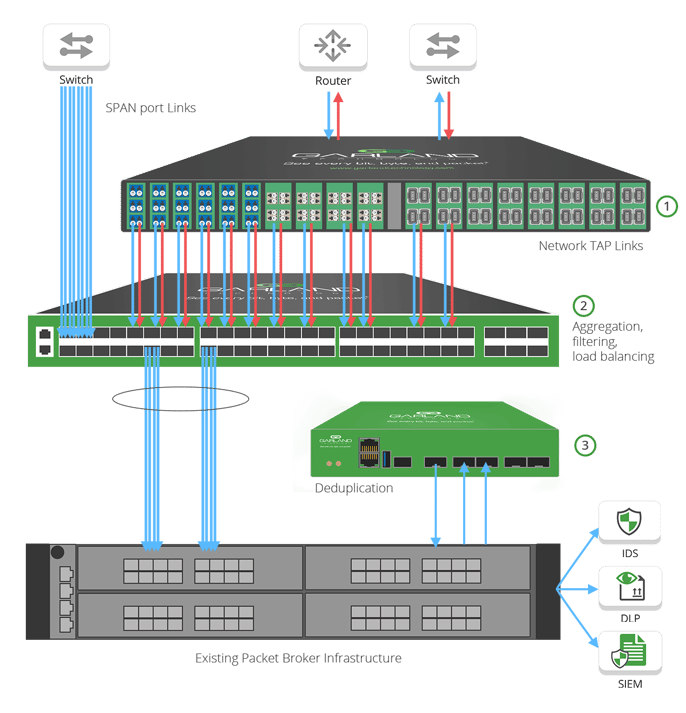
1. Additional Packet Visibility
The demand for network visibility is only growing as teams look to secure the network. Adding packet visibility is now a critical component of any modern security and performance strategy, because simply ‘you can’t secure what you cannot see.’Additional visibility comes down to incorporating network TAPs (or the switch port mirroring alternative) into your deployment, expanding the amount of network coverage your tools monitor. Adding standard ‘breakout’ TAPs typically doubles the number of ports needed for monitoring (e.g., adding 16 additional passive fiber TAPs may require 32 ports on the packet broker).
It is common to face various challenges adding network visibility to existing infrastructure, like speed upgrades, cabling upgrades, throughput, unique media requirements, harsh environments, and the list goes on. We believe network visibility should be an easy, seamless experience. That is why teams turn to Garland for their tapping needs. After 10 years focused on network TAPs, we can tackle any environment or requirement to ensure you ‘see every bit, byte, and packet.’
2. Traffic Aggregation
What to do with those additional tapped links? Adding an aggregation layer between your TAP links and core packet brokers, frees up valuable existing core packet broker ports, reducing license and port fees from the existing packet broker.
An aggregation layer allows you to take the traffic from the 32 links in the example down to 1 or 2 links on your existing packet broker. Additional filtering and load balancing in this layer can further reduce traffic burden to the NPB and tools by up to 50%, enhancing performance.
3. Packet Deduplication
With the rise in packet duplication, as many networks are now seeing between 30-90% of duplicate packets, it is an important function for modern network packet brokers. The proliferation of duplicate packers ultimately burns up NPB and tool processing utilization. Garland’s approach allows you to add a plug-and-play purpose-built device to take the deduplication burden off of your core packet broker, reducing the costly NPB dedup feature licensing fees.Garland’s PacketMAX line of packet brokers makes it cost-effective to incorporate these layers. You can add specifically what you need, whether it’s traffic aggregation or advanced features without license and port fees, ultimately reducing operation costs over time.
While many NPB vendors have shifted their focus to become a full security and monitoring platform, competing with security solutions like NDR (Network detection and response, Garland has pursued a different path). We are solely focused on getting wire and virtual packets to your tools. We will continue to innovate and develop network TAPs and packet brokers to enable an evolving network.
As I say to customers all the time, “You have Gigamon or Keysight Ixia? Great, let’s help improve your packet visibility so you can ‘breathe new life into your existing packet broker!’”
Looking to breathe life into your existing deployment, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do.

