How Historical Look-back is Revolutionizing Network Forensics and Inline Deployment
July 30, 2020

As you can imagine, cyberattacks are now increasing year over year from a combination of cybercriminals, hackers, malicious insiders, unwitting insiders, nation-state attackers and hacktivists. Their attack methods include social engineering, advanced persistent threat, ransomware and unpatched systems attack methods such as phishing, distributed denial-of-service (DDoS) and Man-in-the-middle (MitM) attacks.
Maybe sensing global vulnerability in the midst of COVID-19, 92% of IT and security professionals say cybercrime is increasing. According to ISACA’s global State of Cybersecurity Survey, 53% of today’s enterprises believe it’s likely they will experience a cyberattack in the next 12 months.1
With the sophistication of cybersecurity threats growing, the tools deployed to counter these risks are a combination of out-of-band and inline security solutions that include Intrusion Prevention Systems (IPS), Firewalls, DDoS (Distributed Denial of Service) protection and network forensics and analyzers.
Network forensics strategies monitor the network for anomalous traffic, identifying intrusions and compromises. Attackers are known to cover their tracks by erasing log files on a compromised host leaving network-based evidence as the only viable evidence available for forensic analysis. Network data is considered more volatile and unpredictable as computer forensics where evidence may be preserved on disc, and is usually collected in two forms:
- Catch it as you can: This method captures and saves large amounts of packet data to storage, that are passing through specific segments of the network. Then forensic analysis is being conducted subsequently in batch mode.
- Stop, look and listen: This method takes a more granular approach, analyzing each packet and only certain information is saved for future forensics. This requires a greater processing power to handle incoming traffic.
With the combination of out-of-band and inline security solutions that are vying for specific data streams, and many times handled through different IT teams, this can create added complexity and strain to network architecture and team collaboration. Another challenge teams are facing is how to run forensics off the critical links their active blocking tools are on without using SPAN ports. Teams that are run forensics off the critical link, cannot properly ensure the data being analyzed is 100% accurate and may be dropping anomalous traffic.
One approach Garland Technology has pioneered to address this challenge is deploying a method we call “Historical Look-back.” This adds packet capture and storage capabilities to your inline deployment without using SPAN or additional access points, providing the next evolution of network security. Not only are you managing Intrusion Prevention System (IPS) and Firewalls inline from the same device, you now have data collected for “catch it as you can” or “stop, look and listen” forensics, while also providing “before and after optimization” options.
>> Download Now: Managing the Edge [Free whitepaper]
Look-back Forensics
You can now provide visibility to out-of-band packet capture, storage and analysis tools the traffic from your inline IPS, Firewalls and WAFs tools. If active blocking failed to stop a threat, you now have the ability to analyze why. With the ability to look into breach forensics with the collected traffic, you can:
- Capture network traffic, without loss, at full line rate
- Provide easy to correlate events generated by IPS/NGFW PCAP data
- Facilitate the time-critical workflow for security incident response.
- Enables forensic timelines of days/weeks/months
- Extracted PCAP data may be presented as evidence in court as “chain of custody”
With this data you can facilitate time-critical workflows for security incident response. After critical events are detected, or signature policies are triggered, by the IPS/NGFW, the end user can retrieve full sessions and other detailed context around those important events.
Extracted PCAP files may be further analyzed by a variety of available tools for Deep Packet Inspection (DPI) or security forensics. This PCAP may be presented as evidence in court, with “chain of custody” protection features.
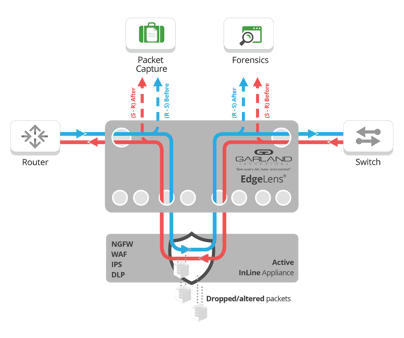
Before and After Optimization & Validation
Another use case we run into with many finance institutions, who need to guarantee their inline tools are properly blocking threats with “Historical Look-back” is the "before and After" method. This is used to analyze packet data “before and after” your inline device to ensure optimal tool performance to validate any updates or troubleshoot why threats weren’t blocked.
This provides visibility into this critical traffic around your inline IPS, Firewalls and WAFs, capturing traffic before it goes into the tool and after it leaves the tool, allowing you to send both copies of data to out-of-band packet capture, storage and analysis tools. This provides next level tool analysis ensuring your inline device is configured properly or if indicating it may be missing the threat, with the ability to:
- Provide easy to correlate events generated by IPS/NGFW PCAP data
- Enable real-time security proof-of-concept evaluations without impacting the network
- Validate changes or updates that your tool is configured properly
- Increase efficiency of inline tools
With the growing demands of out-of-band and inline solutions including SIEM, logging, IPS, DDOS, encryption, firewall, threat detection, and web application firewall, many teams are looking for ways to simplify their security stack by deploying and managing multiple security tools from one access point.
Garland understands that your security stack will continue to grow, and it's going to be a mixture of inline and out-of-band tools. Not only that, multiple teams may need access to that same line of data and SPAN ports aren’t going to cut it.
All of this is solved by the new EdgeLens®, which is a failsafe bypass TAP with a built-in network packet broker for complete management of your network edge. It enables you to deploy and manage multiple active, inline security tools as well as out-of-band monitoring tools, while providing the reliable uptime you're accustomed to with bypass technology. And yes, the ability to easily deploy the “Historical look Back,” method to take your security forensics strategy to the next level.
Looking to add inline or out-of-band security monitoring solutions, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do.
ISACA’s global State of Cybersecurity Survey
1- www.isaca.org/state-of-cybersecurity-2020

