
Garland Technology has been working with the Department of Defense (DoD), providing visibility solutions for various tactical operations, including developing custom network TAPs for the team at Fort Bragg for battlefield communications exercises, as well as various agency network visibility needs.
For most of these environments, as you look at situational awareness, where information warfare is a reality, network visibility becomes a critical component of cybersecurity. Counter measures are important right now, so the more we can be on top of it, the more we can be aware of the kinds of evolving attacks we are seeing.
Recently, we’ve been working with the DoD and federal civilian Cyber Protection Teams (CPTs) to provide visibility for their fly-away kits. The challenges they kept running into were size-related: the solutions our competitors provide are 1U data center appliances that do not work for the travel and mobility that is needed. Running into flexibility and “ease of use” issues, they need to be able to plug and play with various media and speeds in a moment's notice. Also, cost and reliability, they need a visibility product that will last. For example, they had a big Department of Homeland Security (DHS) deployment where a device was End of Life (EoL) and was no longer supported. It becomes critically important because these federal organizations can't deploy anything that can't be supported.
The Need for Troubleshooting Disparate Networks Environments
As you can imagine the federal government’s computer network is a sprawling operation. The Department of Defense Information Networks (DoDIN), has on every Garrison, post-camp station, naval base, or remote location an access point where the DoDIN connects to that facility, and from that point, all of the network traffic that is DoD related gets dispersed across the Garrison.
Fort Bragg, Fort Lewis, Fort Huachuca, for example, is what they call a power projection platform, it's a place where the US government can deploy its military might. Fort Bragg and Pope Army Airfield are right next to each other, so you've got this combination of the military transport, and the 82nd and the 101st airport division together. The DoDIN network connects to Fort Bragg at a drop off point. And then all the DoD traffic from that drop off point, that connection point, is disseminated across the fiber optic switches and local area networks Garrison-wide. Within a Garrison there are enclaves, which are basically organizations or entities that connect to the DoDIN, but have no connection to the internet.
With these disparate networks, troubleshooting performance and security are critical to not only communication and information but situational awareness and mission critical response.
The various government networks can be looked at in a similar way enterprise networks may use managed security service providers (MSSP) teams with their security. Their network enterprise center (NEC) team is responsible for providing the services that run the network, from the telephone, cable, internet, a lot of different technologies. But, in many cases, each location may not have a team well-versed in cybersecurity and troubleshooting.
So they've organized this procedure and structure that has those are assets available to fly out on a moment's notice. Leading to the need for the Fly-away kit.
>> Download Now: Zero Trust Cybersecurity [Free Whitepaper]
What is a Fly-away Kit?
A Fly-Away Kit (FAK) or expeditionary kit is a self-contained suite of equipment, typically with the DoD and CPTs to operate in both tactical field-deployments and back-office environments.
The suite of cyber tools are used to conduct vulnerability analysis, incident response, and other forensic analysis on both classified and unclassified networks.
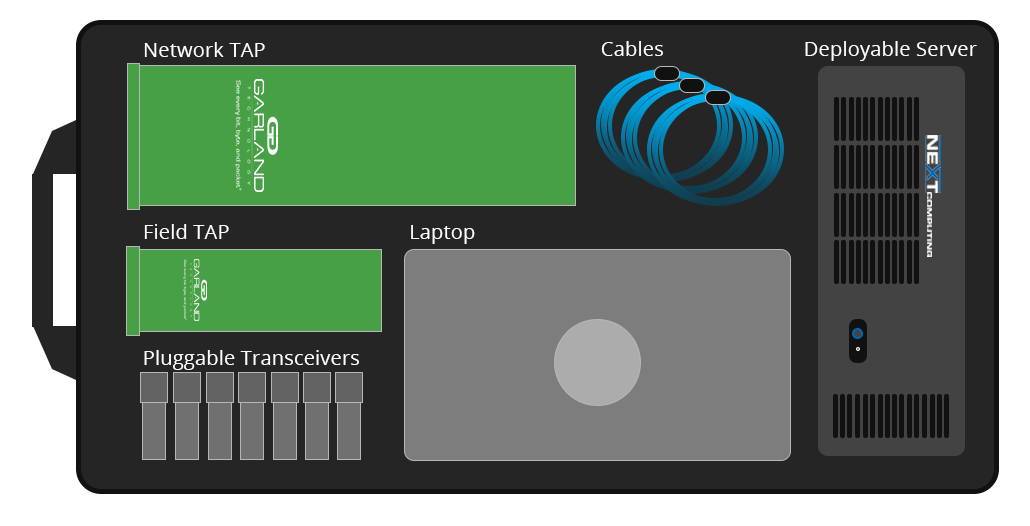
To properly access and analyze these solutions cyber teams require network data from sensors from deployable servers, packet visibility with network TAP, analytic capability from the hardware and software, and user interface typically via their laptops. These suites support a wide variety of user-supplied software modules, including Government Off-the-Shelf (GOTS), Commercial Off-the-Shelf (COTS), and free and open-source software (FOSS).
The Fly-Away Kit Tactical Team Deployments
"Tiger teams” refer to the tactical teams deployed around the world, they can be both uniformed services or government contractors. These tiger teams equipped with Fly-away kits are deployed at a moments notice to various garrisons, bases and offices to perform diagnostics, certifications, accreditations and are periodically testing for vulnerabilities.
These tiger teams often fly commercial airlines and their fly-away kits need to be carry-on luggage, either a backpack or pelican case that typically needs to fit into the overhead compartments.
Network Diagnostics for a Modern Military
- Network Performance. As an example, when the NEC team gets a complaint from a commanding general from the 82nd airport division that the internet's slow, the tiger team is deployed for diagnostics. The team ultimately found that there were guys in the organization that were flooding the network with YouTube videos, leading to a slow response to emails.
- Cyber Security. The various teams are constantly monitoring who is attacking the network, learning what kind of attacks they are using. They regularly perform cyber surveillance, where they fly out and install equipment, leave it there, record the data, just to check and see what's going on in the network, testing vulnerabilities.
- User access. The government has very formal outlines with respect to what you can do on a government computer. So they regularly look for unauthorized laptops that are trying to connect to the internet or monitor users who aren’t approved to access the internet.
Enhancing Fly-away Kit Visibility and Ease of Use
The challenges government integrators run into are easily solved by Garland Technology’s network TAP line, which excels in providing complete packet data in any environment.
Size Form Factor
Garland Technology provides two portable form factors, both being used in Fly-aways kits today. Our portable 4 port network TAP and our new pocket size USB FieldTAP - both easily fit in a backpack or Pelican case and are made of a rugged steel casing that easily handles bumps and drops.
Flexibility and Function
Garland XtraTAPs set the bar in the industry for innovation and ease of use, allowing teams to go into any environment and get to work, without having to dissect network access. Our TAPs not only provide complete packet visibility, they can perform various advanced functions not found in competing TAP devices, including ‘breakout’ tap mode, aggregation, regeneration, inline bypass, as well as advanced filtering and media conversion.
Media conversion is critical going into different environments where you have to adjust on the fly accessing various media options like single-mode, multi-mode, 100base-FX fiber and copper. Utilizing the FieldTAP’s USB monitoring makes it even easier to connect to your laptop.
Applying TAP level filtering becomes useful when troubleshooting high bandwidth critical 1G or 10G links that may be running at 50-60% utilization. Simply filter only the traffic you need without overloading your analyzer.
Quality and Lifespan
Made, supported and tested in the USA, Garland Technology prides itself on quality standards, ensuring all TAPs are stress tested with live network data and validated; proving to be the industry’s most reliable TAP with zero failures. Network TAPs are made to never die, to be the reliable backbone of network visibility.
Looking to add network TAP visibility to your troubleshooting or fly-away kit, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do.

