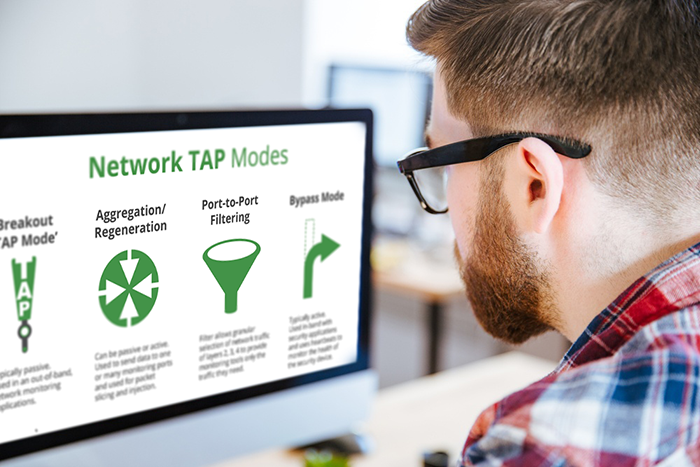
[Training] TAP Modes - Test Your Knowledge
A few weeks back, my sales team introduced a new training video concept to our reseller partners. We sampled a group of 100 by asking them to watch this five minute video, take a 5 question quiz, and...