
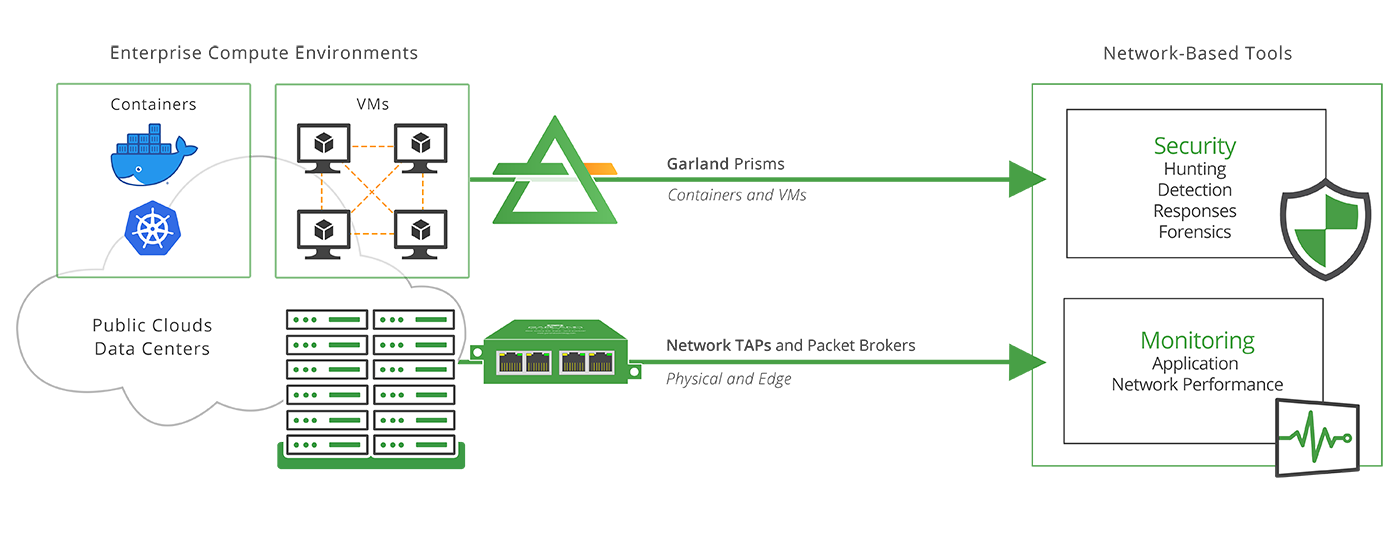
The solution to data security in the cloud, is to incorporate full packet capture, analysis and distribution with a born-in-the-cloud, host-based read-only sensor for packet mirroring. Traffic mirror solutions like Garland Prisms exist today and provide the best solution to full packet-level data monitoring the enterprise is familiar with in their current data center environment.
At face value, the advantages and cost savings of moving enterprise applications to the public cloud are easy to grasp. Why wouldn’t your enterprise leverage the scale and power of the cloud, which grows as your business grows without the huge capital investment of adding to an existing data center?
Well, just like they do in your own data center, applications sometimes misbehave in the public cloud. Let’s say, for example, your organization moves its enterprise resource planning (ERP) application to the public cloud. The data your business stores in its ERP belong to the company and you expect full control access to that data. No one else can get that critical information without your permission, right? Suddenly a software bug allows other users to gain access to the data. How did this security slip-up happen in the cloud?
>> Download Now: Cloud Visibility [Free Whitepaper]
“There is an astonishing number of insecure ERP applications directly accessible online, both on-premise and in public cloud environments, increasing the attack surface and exposure.” –Source: ERP Applications Under Fire: How Cyberattacker's Target the Crown Jewels.
While the cloud simplifies infrastructure provisioning and management, the new challenges that present themselves (security, to name one) must be solved before full-scale cloud deployment takes place. Part of the answer to the security challenge is gaining full visibility into the data you’ve decided to host in the cloud. Network engineers need to determine how they will gain access, visibility and control of the data before moving enterprise applications to the cloud because, once there, they lose access to the tools used in the data center to diagnose these problems.
Packet Visibility to the Rescue
As in the data center, packet capture and analysis are the secret sauce to troubleshooting performance issues in the cloud environment. Full packet capture is like having an 80-inch 4k picture-in-picture screen running your favorite programming 24/7. Unfortunately, public cloud providers only offer up summary information like flow logs – and that information simply doesn’t cut it when your team needs detailed information about a security event. So what should a network security team do?
Staying ahead of security breaches or network issues, and understanding the importance of every single packet matters for the security and performance of your business. To achieve this level of insight in the cloud, you need:
- Accurate packet-level history of network activity so the security team can recreate events and look at related packets to identify exactly what happened and when.
- 100% packet capture of traffic that will help you detect a threat or identify a network performance issue in real time.
- A network monitoring tool that copies packets of all sizes and types to give you complete visibility.
To acquire, process and distribute cloud packet traffic to your monitoring tools, IT teams are turning to next-generation sensors like Garland Prisms. These highly specialized host-based read-only sensors enable packet monitoring and analysis in detail.
Because they are cloud-native, modern sensors like Garland Prisms can be used where there is no virtual network terminal access points (vTAP), or enhance existing infrastructure based tap/mirroring like AWS, which allow you to continuously stream virtual machine network traffic to a network packet collector or analytics tool. With Garland Prisms, users can acquire packet traffic from any public cloud provider and cloud compute resources.
Garland Prisms technology is designed to filter and process the packets and then replicate and distribute the information to the tools and teams that need it. The agent can send traffic to any routable IP address including tool destinations like IDS and DPI security tools, other VPCs or VNETs, and to load balancers that front tool clusters. Garland Prisms can also easily forward traffic with GRE/ VXLAN encapsulation to any specified IP address for your on-premises systems.
What else is next-gen about Garland Prisms? It cuts down on data transport charges while increasing the life and utility of the tools and teams you’ve already put into place. Garland Prisms literally is designed to help you connect your cloud and maximize your access, visibility and control of the data you place there.
The public cloud offers incredible opportunity for your enterprise and with the right formula, you can get full packet capture, analysis and distribution using born-in-the-cloud, for-the-cloud, packet visibility. If it’s confidence and security you’re thinking about as you consider how to fully leverage the cloud, let Garland Prisms serve as the policy driven, cloud networking solution to activate and enable your security and monitoring tools.
Looking to add visibility to your cloud deployment, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do!

