
Today, 50% of large enterprises are spending over $1 million annually on cybersecurity.1 The worldwide information security market is forecast to reach over $170 billion by 2022, as enterprises are making huge investments when it comes to securing mission-critical applications and data-center performance quality.2
This result reflects growing breaches across the networking landscape costing on average $3.92 million in 2019 alone,3 including the cost of networking infrastructure to combat these threats, as well as the impact the company faces through downtime, recovery and reputation.
We’ve talked about the 3 keys to network resiliency being bypass technology, failsafe technology, and network redundancy, as well as understanding your single points of failure. But let’s dig deeper and review what network redundancy is, when it is needed and how to deploy High Availability (HA) solutions in your network.
What Is Network Redundancy?
Enterprise IT operations strategize failure, recovery and business continuity plans that typically include redundancies for critical servers, network segments, security tools and internet connectivity, where a failure would cause significant downtime. In the event of a failure, redundancy allows your network to remain in service by providing alternative data paths or backup equipment.
Network redundancy is introduced to improve reliability and ensure availability. The basic concept that if one device fails, another can automatically take over. With the goal to maximize availability with minimal complexity.
The concept of network redundancy is accomplished through what is referred to as High availability (HA) deployments. HA network designs incorporate redundant components for critical power, cooling, compute, network, security and storage infrastructure with the goal of eliminating any single point of failure that could compromise the network.
When Is Network Redundancy Needed?
Many companies can minimize their downtime through bypass TAPs. However, for industries that have the highest cost of downtime, unplanned downtime is not an option, including Financial Services, Energy, Telecom, Manufacturing, Retail and Healthcare, where critical services and information must be secure and available 24/7/365. Just last year, 86% of worldwide enterprises reported an average hourly downtime cost of their servers at over $300K, with 15% being over $5M.4
Despite the enormous investment in infrastructure and security tools, many IT teams continue to experience database, hardware, and software downtime incidents that can last a few minutes to days, accruing not only these revenue losses but enduring negative customer experiences and having sensitive data compromised. Many times the repercussion of a down security tool like a firewall or Intrusion Prevention Systems (IPS) can lead to additional breaches or security events.
Downtime can happen for a variety of reasons, through cyber attacks, human errors or misconfigurations, understaffed IT departments, power failures and hardware failures. To reduce downtime, it is essential to plan for unexpected events that can bring down the systems. HA systems minimize the impact of these events, and are designed to automatically recover from failures.
Adding Reliability to Your Security Strategy
Inline security tools like IPS, Web Application Firewalls (WAF), and firewalls are typically architected inline, meaning they are sitting directly in the path of critical links. The purpose is to block threats in real-time before they get into the broader network. Unfortunately this introduces potential single point of failure (SPOF) challenges like what happens if the device failed, and how do you properly update or optimize once it is inline?
As a recent EMA [Enterprise Management Associates] report states, “An oversubscribed device can degrade network performance and a device failure can bring down the network. Managing the risk of downtime is a critical consideration when connecting security devices to the network.”5
Industry best practice encourages all inline tool availability to be managed by an external bypass TAP. The next step is taking this technology and applying redundancy to critical links ensuring that in the event of a failure to critical links, High availability (HA) bypass deployments are your foundation to cybersecurity redundancy.
Garland offers two scenarios for incorporating High Availability (HA) solutions into your network, Active/Standby and Active/Active. Active Standby (or Active/Passive) deploys to a secondary tool, providing failover from primary device to backup appliance. The Active/Active Crossfire design incorporates a secondary tool, bypass TAP and redundant link, providing the ultimate failover if either active device fails.
Deploying Redundant Inline Security Tools
HA Bypass TAPs can connect two inline tools with a primary / secondary or an active / standby design. These Bypass TAPs sit inline on a single network link and can connect to redundant tools without adding additional complexity or a new point of failure to the network.
In these single link situations, the Bypass TAP will send live traffic from the network to both tools. One tool will be the primary or “active” appliance managed inline with the Bypass TAP. The secondary or “passive” appliance also receives live traffic out-of-band, but will not forward traffic back onto the network. This provides “Hot Standby” redundancy. In the event the primary tool goes down triggering the bypass heartbeats to stop, the secondary tool immediately takes over as primary and is brought inline by the Bypass TAP.
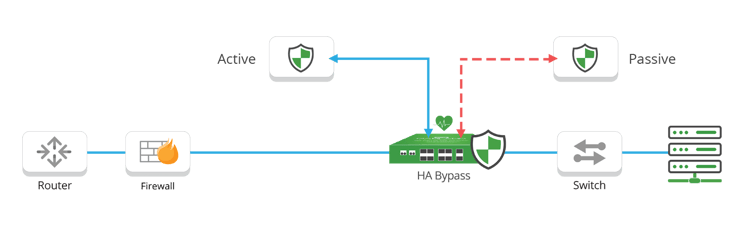
Diagram: HA solution for Active/Passive, provides failover from primary device to backup appliance.
Deploying Inline Security Tools with Redundant Links
In architectural designs where redundant network links are used, a similar bypass TAP design can be incorporated. This time the redundant security tools are cross-connected between the two HA Bypass TAPs. In this Active/Active Crossfire design, each tool and Bypass TAP should be the primary appliance for their respective link, and the redundant for each other, usually resulting in asymmetric routing. If an appliance goes down, the network link’s traffic will fail-over to the secondary link, allowing all the traffic to be seen by the remaining active appliances.
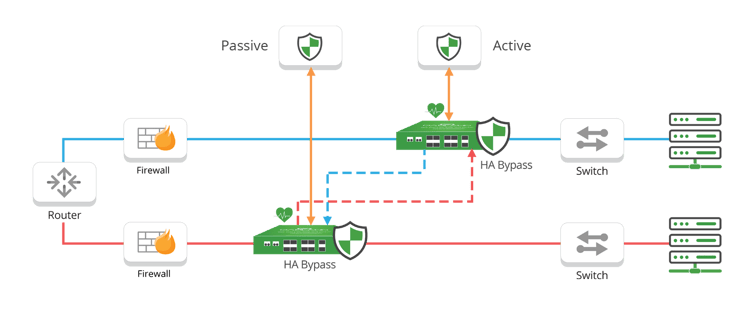
Diagram: HA Crossfire solution for Active/Active, provides failover if either active device fails.
Cybersecurity relies on redundancy to ensure network availability, because for critical links, downtime is not an option. Using Bypass TAPs on inline appliances will not only ensure these tools are constantly protecting the network, but providing functionality to expedite troubleshooting and shorten maintenance windows.
If you are deploying redundant security solutions into your network, Garland has specifically designed HA Bypass TAPs and Inline Security Packet Brokers that not only provide the same reliability and management controls of a standard bypass, but also provide the ability to manage multiple inline and out-of-band tools from the same device with packet broker functionality. This was the case recently when a large financial corporation, who specialize in Business and Commercial Banking and Financing came to Garland Technology looking to future proof their security deployment with a cost effective, scalable connectivity strategy that provides resilience and redundancy.
We achieved this HA solution deploying Garland’s EdgeLens® Inline Security Packet Broker, which transformed their network security capabilities with added functionality, easily complementing the new HA architecture.
Looking to add an HA solution to your security deployment, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do.


