
When the subject of Network TAPs (Test Access Points or Traffic Access Point) are brought up, the image that may come to people’s mind is a device that 'taps into the network' to provide packet visibility by sending copies of traffic to an analyzer.
And on a basic, yet important level this is spot on. Network visibility has quickly become the backbone of modern network and security architecture. Though many people may not think about the optimization options a TAP also provides engineers and architects as they plan the best way to connect a network.
Let's review six different TAP designs: Breakout, Aggregation, Regeneration/SPAN, Filter, Bypass and Media conversion, that could help your next deployment.
1. TAP 'Breakout'
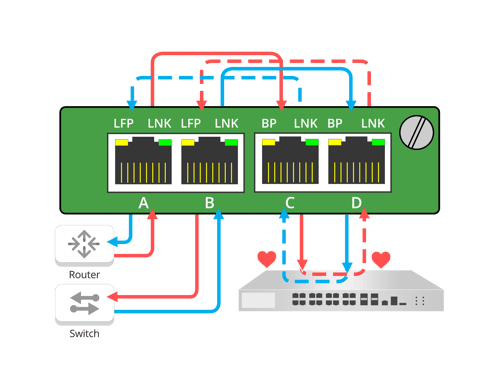
This is the typical use case people use a network TAP for. A standard TAP is made up of four (4) ports A, B, C and D. Ports A and B are the network ports and C and D are the monitor ports.

Diagram 1: Breakout "Normal TAP" Mode
Simple Implementation of a Breakout TAP
- The eastbound traffic from a network device, in this case a router, flows into network port A and flows out of network port B to another network device, in this case a network switch.
- Port B then sends it to monitor port C.
- The traffic that flows from network port B to network port A and send it to monitor port D.
This TAP is generally used when the traffic on the attached link is heavy enough to cause over subscription if the send and receive traffic were aggregated together to one monitor port. This TAP requires that the tool or appliance it is attached to requires two network interface cards (NICs) in order to capture both the eastbound and westbound traffic streams. Learn more about breakout or normal TAP mode.
>> Download Now: Network TAPs 101 [Free eBook]
2. Aggregation TAPs
To take the traffic that flows from ports A to B and B to A and merge them together into one monitoring port. As long as the combined traffic does not oversubscribe the monitor ports, the TAP will send all the traffic out to the attached tool or appliance. Because all the traffic can be sent on a single port, the TAP can send all the traffic out to two monitoring devices. Learn more about aggregating TAP mode.

Diagram 2: The Aggregation TAP copies data in both directions for monitoring .
3. Replicating/SPAN TAP
Often times there are not enough SPAN ports on a network router or switch to go to multiple analyzer tools and appliances. A convenient way to solve this problem is to send the SPAN or mirrored input to a replicating TAP. The traffic on the SPAN input can now be distributed out to up to three (3) different tools. Learn more about replicating/SPAN taps.

Diagram 3: The Replicating TAP takes a SPAN input and sends this data to multiple locations.
4. Filtering TAPs
Network TAPs are designed to copy all of your data, but often your tools don’t need to see 'everything.' Your VoIP or Wireshark only needs to see the traffic required to do it's job. This is where Garland's unique filtering is a desired feature because you can filter out what is not required by the tool – ensuring the monitoring ports will not be oversubscribed.
This scenario (below) shows four 1G links with a filter applied and then aggregated together and sent out port D on TAP four to the monitoring tool. Learn more about filtering taps.

Diagram 4: Four 1G links aggregated together and sent out port D
5. Bypass TAP
6. Media Conversion TAP
What happens when you have a monitoring tool that isn’t the same media type as your live connection, or visa versa? You might have a single-mode, extended-range fiber network link that stretches about 10km. But your network analyzer is sitting two feet away. Your first option might be to purchase the transceivers to match the links; however, this is an expensive and inefficient approach. Or more common, converting a fiber link to copper monitoring ports allowing you to still use your copper tools and appliances. This is just one scenario below of media conversion utilizing a network TAP. Learn more about media conversion network TAPs.

Diagram 6: Converting a fiber link to copper
Media Conversion Single-mode to SFP: convert single-mode fiber over to multi-mode fiber in the same manner by deploying a TAP that has single-mode network ports and SFP monitoring ports, shown below.

Media Conversion: Copper to SFP: Take a copper link and convert it to single-mode or multi-mode fiber using a TAP that has copper network ports and SFP monitoring ports, shown below.

Diagram 8: Converting a copper link to SFP
Aside from all the various types of TAPs, it's also important that a TAP must be able to do a very important task, it must not introduce a “point of failure.” If anything were to go wrong with the TAP, the live traffic must continue to flow. And in the case of the bypass TAP, if anything were to go wrong with the in-line appliance, the link must continue to flow.
I hope this takes some of the mystery out of network TAPs and how they can help you keep your network running smoothly and secure.
Garland Technology's, The 101 Series is an educational series on how network TAPs work and the different functions they provide to the overall network design for access and visibility.
Looking to add a visibility solution to your next deployment, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do!

