
A firewall is a network security device that monitors both incoming and outgoing network traffic, and based on a set of rules, decides whether to allow or block that traffic, protecting the network. Whether you are replacing a legacy firewall or adding an additional NGFW (Next-Generation Firewall) for internal security, a detailed deployment plan is required.
Palo Alto Networks’ Next Generation Firewall has different deployment methods. Let’s explore the different options to see which one works best, and why. Some content has been adapted from Palo Alto Networks’ Designing Networks with Palo Alto Networks Firewall. Let’s state the most important thing regardless of what deployment method you choose; your Palo Alto Networks NGFW needs to be inline in order to block and prevent suspicious behavior.
Four Methods of Deployment for a Palo Alto Networks NGFW:
- TAP Mode - Should only be used for Proof of Concept (POC) when gathering information to be fed via SPAN/Mirror port. This method does not see the direction of the traffic and is not useful beyond POC.
- Layer 3 - Routing mode deployment - the problem with this is that the network ‘sees’ the NGFW
- Layer 2 - Switch mode - same as above, the NGFW is visible to the network
- VMware mode - is located below layers 2 and 3 and the NGFW is invisible to the network, it is a simple, ‘bump in the wire.’
>> Download Now: 3 Keys to Network Resiliency [Free Whitepaper]
The most common and best form of deployment is VMware mode. In this instance, you can see the direction of the network traffic and enforce security settings with real network data. Ideally, you want to couple the VMware deployment with a Bypass TAP to monitor the health of your inline device and provide 100% network visibility.
Why is this a best practice?
One disadvantage of an NGFW is there is no failsafe built into the appliance. This means if there is a power outage or appliance issue your network will be down. Garland Technology’s EdgeSafe®: Bypass Network TAPs have a failsafe feature built-in for full uptime. When you use Garland’s EdgeSafe®: 1G Bypass Modular Network TAP within a 1U or 2U chassis, with a simple one-click command you’re able to take the NGFW off-line without taking down the network. When the power is resolved, simply click back to active, inline mode via a remote management card.
Managing Your Palo Alto Networks’ Deployment Lifecycle
Vmware mode deployment coupled with a bypass network TAP is part of best practices because it benefits the entire lifecycle of an appliance, including POC, validation & deployment, and troubleshooting - with only taking the mission-critical network down once, at initial deployment.
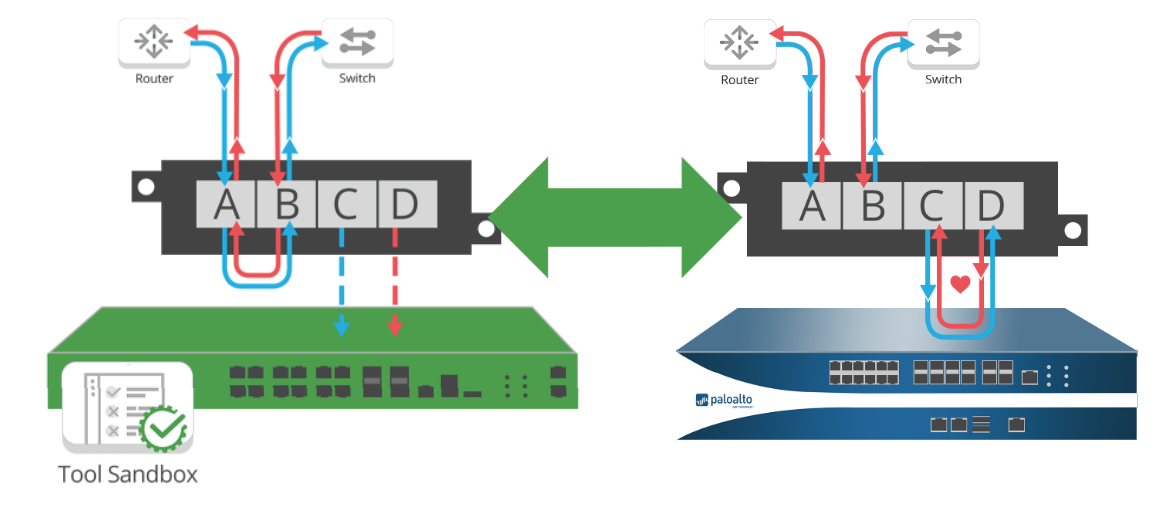
“A bypass TAP is invisible to the network. During a proof of concept (POC), the network sees all directions of the traffic - as if it was inline, allowing you to write policy because the traffic direction is known and is based on ‘real and observed data'.
It takes away the headache of cutover and allows you to 'test your policy' by having the NGFW process traffic as an inline device while providing the ability to put it back to virtual inline when troubleshooting potential problems - all without affecting production traffic. With one-click, the bypass TAP can operate from inline to out-of-band for POCs, troubleshooting, and for failover protection. Even when your tools are out-of-band, the Bypass TAP will passively see all traffic, but will not affect it. Another benefit to using Network TAPs as part of your deployment is since Network TAPs don’t possess IP or Mac addresses, they are completely invisible to hackers. This means that when deploying network TAPS with your NGFW your visibility method into the traffic cannot be hacked.
Palo Alto’s NGFW combined with a Garland Technology EdgeSafe Bypass TAP is a fundamental best practice that offers a unique ability to implement inline lifecycle management. From improving your POC, sandboxing new tools, troubleshooting, and most importantly, avoiding costly network downtime, the bypass TAP becomes the essential complement to your NGFW.
As you move forward to prepare and secure your data center, don’t leave your network out in the cold. Obtain 100% visibility and network uptime when you deploy a Palo Alto NGFW and Garland Technology bypass TAP.
Looking to add a bypass solution to your security deployment, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do!

