A10 Networks
Secure the Edge
Expecting a PDF?
We created this solution brief as a web page for better mobile optimization and accessibility. If you'd still like a PDF version of this use case, you can download it here:
Provide Visibility and Secure Blind Spots With SSL Decryption
When trying to support network continuity, mitigating the risk of scheduled or unscheduled downtime is an issue for any operation. The need for a secure layer to identify and actively block hidden threats can be difficult and costly, especially while also keeping your network resilient. Deploying inline appliances on mission-critical network segments requires active-passive flows to decrypt data for network security.
A10 Networks has partnered with Garland Technology to provide an inline security layer without compromising network uptime. A10 Networks Thunder SSLi eliminates blind spots within your network for efficiency within your security device. Garland Technology’s Inline Edge Security solutions, which provides bypass technology mirrors the SSL decrypted traffic from A10 Networks to application performance monitoring tools, adding seamless SSL decryption to necessary workflows.
Inline Bypass
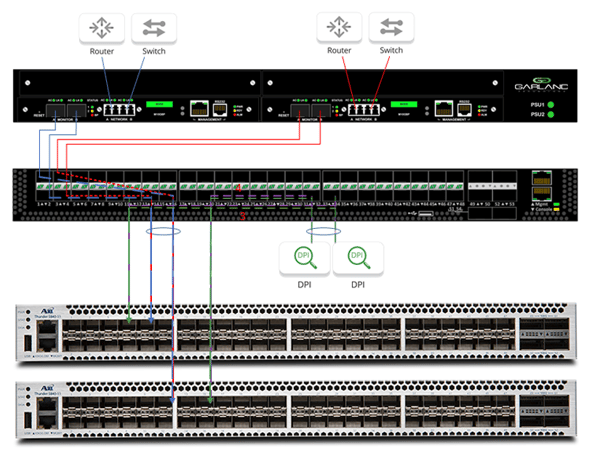
For a single source deployment, traffic is sent from the router through the A10 Networks’ Thunder SSLi CFW 5840 for data decryption. The decrypted traffic is directed back to the Garland Technology EdgeSafe™ Network Bypass TAP, exiting the daisy-chained network port to the next bypass segment.
Once the network data is sent through the DPI and into a second network port, the traffic travels through the second A10 device for re-encryption. The simplicity of this connection allows a single point of decryption throughout the network to eliminate blind spots, ensuring compliance and privacy.
Seamless Integration with Multiple Links
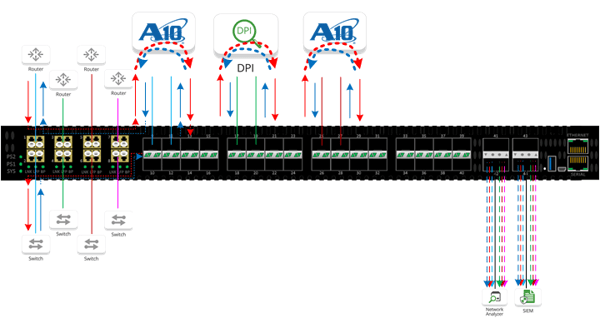
When deploying in multiple networks, traffic from each network link is brought into the Edgelens® inline security packet broker and VLAN tagged. Once tagged, the traffic is aggregated and load-balanced through the two A10 Thunder SSLi devices. The data is decrypted and routed to the DPI appliances in reverse order back to the A10 devices for re-encryption. This seamless integration throughout your infrastructure allows comprehensive, real-time and actionable insights with application-level visibility.
The joint solution provides visibility to all security devices, including inline, out-of-band and ICAP- enabled devices. Together, A10 Networks and Garland Technology detect advanced threats with low impact and load-balance to distribute traffic across multiple networks.
About A10 Networks
A10 Networks believes the future of cyber security for 5G and multi-cloud rests on Intelligent Automation coupled with machine learning, ensuring that business critical applications are protected, reliable, and always available. Visit: www.A10-networks.com
- Delivers the performance, scalability, and agility for the largest multi-cloud and 4G/5G networks
- Leverage built-in connected intelligence and analytics for smarter protection throughout your mission critical network
- Use artificial intelligence, machine learning, and predictive analytics to protect against threats, today and in the future
- With automation and open API’s, seamlessly stregthen your security posture while optimizing IT resources

Garland Technology and A10 Networks provide a continuous SSL Decryption security solution. Looking to add this solution, but not sure where to start? Join us for a brief network Design-IT Demo or consultation. No obligation - it’s what we love to do.