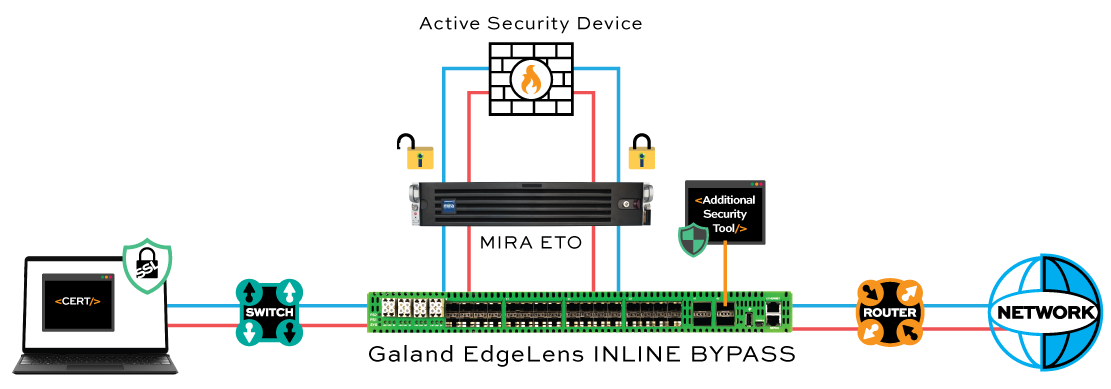
Mira Encrypted Traffic Orchestration (ETO) software provides safe and secure visibility into encrypted traffic allowing the tools used by enterprise security teams to function effectively, even when all the important traffic is encrypted. Enabling the enterprise security stack to detect and mitigate threats while providing features to enable privacy and ensure compliance requirements can be met is central to Mira ETO software. Mira ETO software decrypts traffic and feeds it to one or more security tools that actually detect and mitigate any threats that may be present. No special interfaces or software changes are required to the security tools; they simply receive traffic from Mira ETO as if it was traffic directly from the network.






Key Features
- Automatically detect all SSL/TLS and SSH traffic in the network, no matter what ports are being used
- Capable of decrypting SSL v3, TLS 1.0, 1.1, 1.2 and 1.3, as well as SSHv2
- Transparent to the higher-level protocols being carried on top of the encrypted layer providing decrypted flows to security tools for any existing or future protocols
- Seamless integration with existing security tools protects existing security investments
- Policy control over which encrypted traffic is made visible allows compliance with industry requirements and enterprise policies on data privacy
Additional
- Mira ETO software is licensed as a subscription model
- Specifications
- Resources
- Network Diagram
- Request a Quote
| vETO (Virtualized Decryption Appliance) |
ETO-DL-0.5 | ETO-DL-1 | ETO-DL-2.5 | ETO-DL-5 |
| Licensed Decrypt Gb/s | 0.5 | 1.0 | 2.5 | 5.0 |
| Min CPU Cores/Memory | 8/16GB | 8/16GB | 10/24GB | 12/32GB |
| TLS Sessions/s RSA 2048 | 750 | 750 | 2,200 | 3,000 |
| TLS Sessions/s EC256 | 1,400 | 1,400 | 3,800 | 5,800 |
| Max TLS sessions | 100,000 | 100,000 | 300,000 | 400,000 |
| Boosted CPU Cores/Memory | 10/24GB | 10/24GB | 12/32GB | 14/40GB |
| TLS Sessions/s RSA 2048 | 2,000 | 2,000 | 3,000 | 4,500 |
| TLS Sessions/s EC256 | 2,000 | 2,000 | 8,800 | 8,800 |
| Max TLS sessions | 300,000 | 300,000 | 650,000 | 650,000 |
Interested in purchasing this product?
Simply fill out this request a quote and one of our team members will contact you. Thank you.






