Network resiliency and availability without downtime
Inline Bypass Solutions
Deploying and Managing Your Inline Appliance

When architecting inline security tools into your network, incorporating network bypass technology is a fundamental best practice to avoid costly network downtime. Simply put, a Bypass TAP, also referred to as a 'bypass switch', provides the ability to manage the availability of your inline tool any time without having to take down the network or impact business availability for maintenance or upgrades.
In the tense moments of unplanned downtime, a bypass TAP provides expedited problem resolution in the event of a tool failure, with the flexibility to bypass the tool and keep the network up, or failover to a High Availability (HA) solution.
Managing the Risks of Downtime
As inline security devices sit either between network segments or at a network edge, managing the risk of a downtime is a critical consideration when deploying security devices. Security teams commonly face:
• Device failures can bring down the network
Downtime Impacts more than the Network
• Lost revenue
• Loss of customers and trust in the company, reputational damage
Why Use An External Bypass TAP?
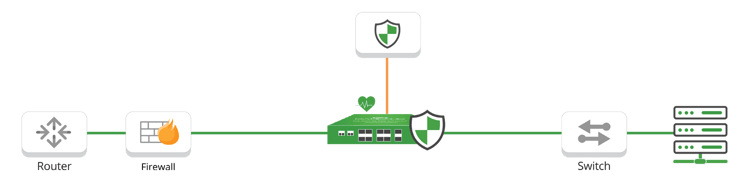
The Bypass TAP was developed specifically to resolve the problem of an inline tool causing a single point of failure (SPOF) in the network. In the event an inline device becomes unavailable, it is bypassed and traffic is automatically forwarded around the failed tool.
“Research found that extensive use of external bypass devices is a best practice.”
-EMA [Enterprise Management Associates]
Appliances may have internal bypass capability, but adding this feature is known to be costly and still lacks key functionality associated with Bypass TAPs, including:
• Administrative isolation - No maintenance windows• Operational isolation - Expedited problem resolution of unplanned downtime without impacting network connectivity
• Tool Sandbox - Pilot or deploy new tools
• Deployment efficiency - Extend the reach of the same tools into multiple network segments
• Network resilience - Flexibility to bypass the tool and keep the network up, or to failover to a High Availability [HA] solution
Heartbeat Packets Monitor the Tools Health
Heartbeat packets, a soft detection technology, are configured to monitor the health of inline appliances. Instead of relying on the direct connectivity of the network to the tool, the bypass TAP is purpose-built, designed specifically to pass heartbeat packets back and forth to detect an issue with the connected appliance. A heartbeat packet is added by the Bypass TAP to the data, and both are sent out to the input port of the inline device. The inline device performs its task and then sends the data back into the TAP with the heartbeat. The Bypass TAP strips the heartbeat from the data, which is sent out of the TAP and back into the live network.
Heartbeats are never sent into the live network. If the heartbeat sent from the TAP is not received back, indicating the device is offline for some reason, the TAP will automatically bypass the device, keeping the network up even though the device is offline. No network downtime. No single point of failure.
Inline Lifecycle Management
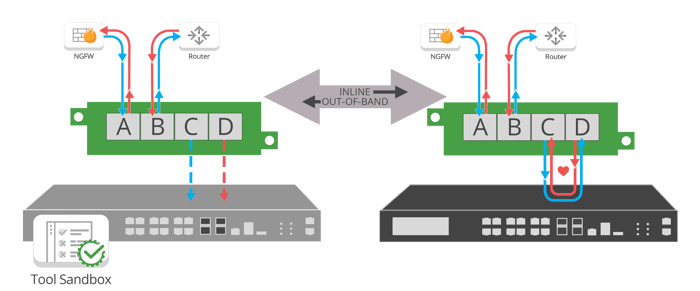
Utilizing an external Bypass TAP, and not relying on bypass functionality within your inline tool, offers the unique ability to implement inline lifecycle management. From sandboxing a new tool deployment to easily taking tools out-of-band for updates, installing patches, performing maintenance or troubleshooting to optimize and validate before pushing back inline, a Bypass TAP has quickly become the essential compliment to any inline tool.
Sandboxing or piloting new tools in your real environment with live packet data, without impacting the availability of the network, provides the ability to evaluate and optimize the tool out-of-band, before deploying it live in your network. The tool being tested is exposed to the same type of data it would be monitoring for a production deployment, rather than test data, increasing the confidence of the piloting being performed.
Benefits of Inline Bypass
Bypass Best Practices
Bypass TAPs solve many issues. Let's explore bypass use cases to see why:
Bypass functionality is essential to preventing inline security devices from causing network performance degradations and downtime. Many appliances have internal bypass capability, but external bypass devices are considered more reliable and offer more features.


"Knowing the loss of time and money was unacceptable, I designed the network bypass TAP. This solution continuously checked the health of the device and ensured the integrity of traffic flows regardless of their condition."
Jerry Dillard
Garland Technology, CTO - Developed the first bypass technology
Bypass Resources

3 Keys To Network Resiliency
The ability to update, repair, and replace security appliances without bringing down the network for a maintenance window, and reduce the risks of unplanned downtime, are the next step for network resilience.

Managing the Edge
Review the challenges when deploying inline security appliances, how to access data at the edge, how to chain the edge of your network with multiple inline devices and how to meet advanced edge management needs.
Additional White papers
Discover Garland's Bypass Products
TAP into Technology
Leading the way in Network Technology

The 101 Series: Out-of-Band vs Inline Network Security
| October 8, 2025
Designing a modern cybersecurity strategy is no easy feat, as it must protect all components of a complex network, while having a limited effect on..

Why Do Inline Security Tools Rely on External Bypass TAPs?
| August 20, 2025
As the modern cybersecurity stack grows with an array of threat detection and response tools critical to protecting IT data, active blocking tools..
The Deployment Defender: Ensuring Network Uptime with Bypass TAPs
| July 9, 2025
Summary In this comprehensive blog post, we explore the critical role of bypass TAPs in inline security deployments. By providing a fail-safe..









