Asimily relies on passively ingesting raw network traffic within an environment to both compile an inventory, as well as assess customer vulnerabilities and threats. This can be done in a variety of ways including the use of SPANs, Packet Flow Switches, Packet Brokers, Passive and Active TAPS, etc.
The Problem
The Problem
1. SPAN ports cannot be used for whatever reason.
2. Supporting multiple large bandwidth connections (40GB or greater)
The Solution
The Solution
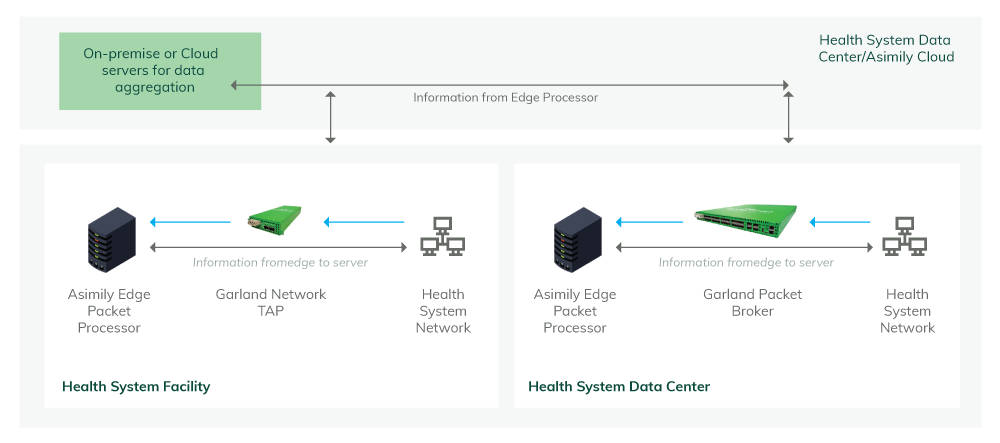
1. Enable packet capture without the use of SPAN ports by deploying Garland Network TAPs and Packet Brokers architected to meet your unique needs
2. Deploy a Garland Network Packet Broker to aggregate traffic from multiple high bandwidth connections and then feed that data into,
N-number of Asimily Edge Processors
The Benefits
The Benefits
1. Provides a more secure, quick and easyto- deploy alternative to the use of SPAN ports
2. Eliminates the need for supporting 10GB interfaces or using DAC cables to split a 40GB into 10GB links.
TAP -> TOOL
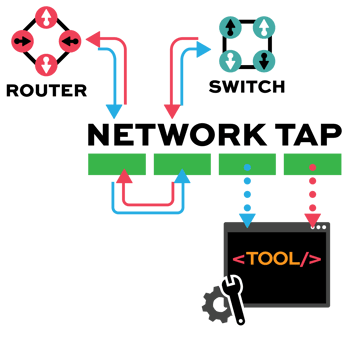
Network TAP Benefits
- Provide complete packet visibility with full-duplex copies of network traffic.
- Ensure no dropped packets while passing physical errors and support jumbo frames without delay or altering the data.
- Support speeds from 10/100M, 1G, 10G, 40G, 100G, and 400G are available in single-mode and multi-mode fiber or copper ethernet.
- Available in Tap ‘Breakout,’ aggregation, regeneration, bypass, and advanced filtering.
- Passive or failsafe – Does not affect the network.
- No IP address or MAC address, and cannot be hacked.
- How It Works
- Key Solution Benefits
- Full PDF Solution Brief
Network Diagram
Key Capabilities
1. Simple, easy to deploy
2. Cost-effective solution
3. Industry leading features and performance
4. Customizable solutions to meet customer requirements
Key Solution Benefits
1. Improve device monitoring and classification of risk with Asimily’s knowledge base of IoT Security Protocols
2. Faster threat context faster with Asimily Insight’s threat and anomaly detection interface
3. Identify potential compromises related to domains or IPs by easily viewing CrowdStrike’s verdict from the Asimily Insight console





