BluVector
Advanced Threat Detection
Expecting a PDF?
We created this solution brief as a web page for better mobile optimization and accessibility. If you'd still like a PDF version of this use case, you can download it here:
Real-Time Advanced Threat Detection and Network Visibility
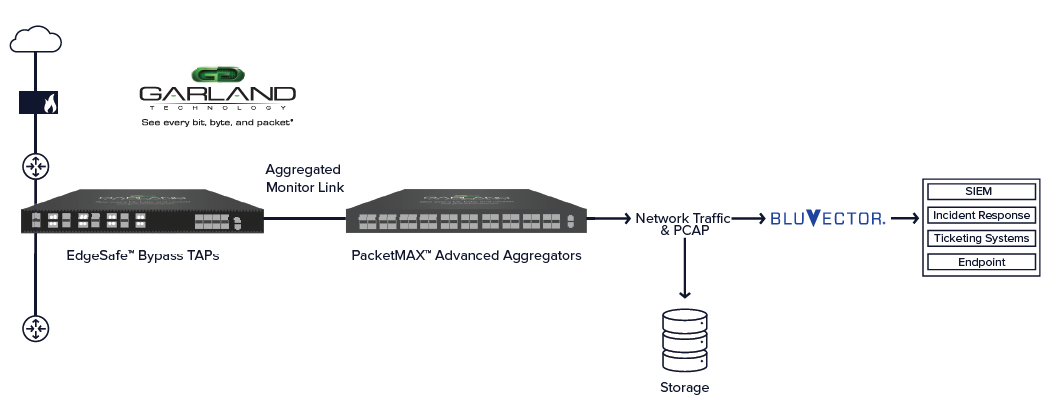
Responding quickly to cyber security threats is no longer a world where minutes matter. Today, every second matters. To address this reality, Garland Technology and BluVector have partnered by integrating Garland’s high-performance test access points (TAPs) and Advanced Aggregators with BluVector’s AI-driven network security platform to deliver high-fidelity detection, at scale, in real-time, across the enterprise network.
Delivering Sophisticated Threats in Real Time
Garland’s EdgeSafe™ Bypass TAPs and PacketMAX™ Advanced Aggregators provide 100% visibility, delivering complete copies of network traffic along with other data sources like PCAP files. BluVector is revolutionizing network security with its state-of-the-art AI and machine learning platform, sensing and responding to the world’s most sophisticated threats in real time.
The BluVector sensor delivers real-time analysis of both file-based and fileless threats. The network visibility provided by Garland Technology combined with BluVector’s sensors allow security professionals the ability to detect and triage events with an increase of up to 400% efficiency.
In addition to triaging malicious “incidents” in minutes, the BluVector solution provides Zeek (formerly known as Bro) users with associated Bro logs for each of these events. The logs are easily usable by non-Zeek users via BluVector’s targeted logging function. For advanced Zeek users, BluVector provides a full searchable log environment for threat hunting.
BluVector AI-Driven Network Security
BluVector® is an AI-driven sense and response network security platform. Designed for mid-sized to very large organizations, the platform makes it possible to accurately and efficiently detect, analyze and contain sophisticated threats including fileless malware, zero-day malware, and ransomware in real time.
Key Capabilities
• Intelligent Decision Support – Delivers context and visibility to threat security teams and their investigations by pre-correlating and highlighting log entries associated with events prioritized for analysis.• Hunt Process Automation – An extensible Connectors Framework increases analyst efficiency by up to 400% with automated incident investigation and confirmation.
• Flexible Deployment – A rich connectors framework makes it possible for BluVector to receive and correlate data from a variety of threat intelligence sources, send events to SIEMs like Splunk and QRadar, and integrate with network or Endpoint Detection and Response (EDR) solutions to enable blocking.
About BluVector
BluVector® a Comcast Company is an AI-driven sense and response network security platform. Designed for mid-sized to very large organizations, the platform makes it possible to accurately and efficiently detect, analyze and contain sophisticated threats including fileless malware, zero-day malware, and ransomware in real time.
As a leader in advanced threat detection, BluVector is empowering security teams to get answers about real threats, allowing businesses and governments to operate with greater confidence that data and systems are protected. For more info, please visit: bluvector.io

Garland Technology and BluVector provide a continuous threat detection solution. Looking to add this solution, but not sure where to start? Join us for a brief network Design-IT Demo or consultation. No obligation - it’s what we love to do.

