Check Point
Cyber Security
Expecting a PDF?
We created this solution brief as a web page for better mobile optimization and accessibility. If you'd still like a PDF version of this use case, you can download it here:
Insights
For enterprise networks that manage multiple security and monitoring tools, the integration of Check Point Quantum Security Gateways and/or Check Point Quantum DDoS Protector with Garland EdgeLens® In-line Security Network Packet Broker provides a fail-safe bypass TAP along with advanced filtering, aggregating, regeneration and load balancing functionality.
100% Network Visibility and Access
Through the integration with Garland Technology EdgeLens, Check Point Next-Generation Firewalls (NGFW) and/or DDoS Protector products can be configured in serial (chaining) or in parallel (load balancing) to meet your network security needs for up to four in-line devices.
Manage Multiple Inline Security Tools
The EdgeLens is a fail-safe bypass TAP with a built-in network packet broker for complete management of the edge of your network. Deploy multiple in-line security tools and out-ofband monitoring tools while gaining 100% network access and visibility.
DEPLOYMENT OPTIONS
When your 1G tools can no longer keep up with your 10G network or if you need to connect multiple tools to one network link, EdgeLens provides flexibility and scalability for your network needs.
• TAP once and connect multiple in-line security appliances
• TAP a 1G link - or - a 10G link and deliver data to 1G and 10G tools
• TAP a 10G link and deliver data to 1G and 10G tools
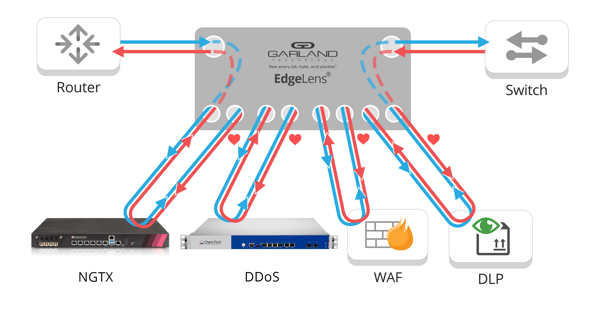
10g Chaining of up to Four in-Line Security Devices
Chaining or serial deployment creates a unified visibility layer by connecting all security appliances to each other and to EdgeLens. In a chaining scenario, all network traffic enters EdgeLens; it then sends data packets through the in-line security appliance chain. Each appliance analyzes the data, after the data is cleared EdgeLens copies and stores it for forensics analysis. This full visibility allows administrators to monitor data packets both before and after they pass through the security stack while maintaining network efficiency.
Advanced Load Balancing of Four 1g in-Line Security Devices
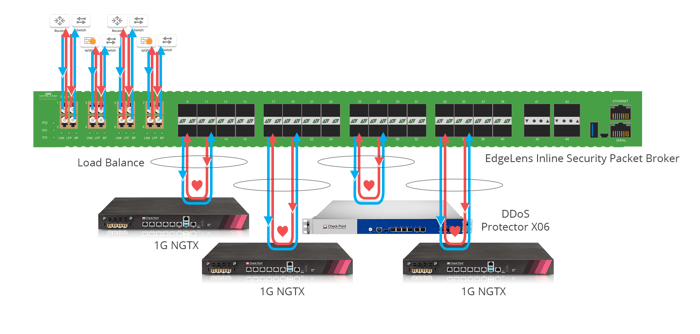
Advanced load balancing is a cost-effective strategy when you have a 10G link and multiple 1G appliances. Here, you see an EdgeLens packet broker with 12 ports. Traffic comes in from the 10G link between a router and a switch and is copied to two out of-band solutions, a forensics application, and Wireshark. The traffic is then load balanced across four separate 1G Check Point NGFWs.
Benefits for IT Security Teams
• Support up to four active, inline tools and multiple out-of-band monitoring tools
• Chaining (or serial)the configuration provides 100% visibility allowing each appliance to analyze data
• Advanced load balancing (or parallel) configuration is a cost-effective solution to maximize your 1G NGFW or DDoS investment
• Query before and after packet capture stores to validate policy changes
•Complete visibility and real-time monitoring both in-line and out-of-band tools
• Take appliances off-line for updates, maintenance or trouble shooting
About Check Point
Check Point Software Technologies Ltd. is a leading provider of cybersecurity solutions to governments and corporate enterprises globally. Its solutions protect customers from cyber-attacks with an industry leading catch rate of malware, ransomware, and other types of attacks. Check Point offers a multilevel security architecture that defends enterprises’ cloud, network, and mobile device-held information, plus the most comprehensive and intuitive one point of control security management system. Check Point protects over 100,000 organizations of all sizes.

Garland Technology and Check Point provide security and resiliency at the edge of your network. Looking to add this solution, but not sure where to start? Join us for a brief network Design-IT Demo or consultation. No obligation - it’s what we love to do.
