Claroty
Reveal, Protect, and Manage OT, IoT, and IIoT Assets.
Comprehensive Visibility and Security For OT, IoT and IoMT Environments
- Problem
- Solution
- Benefits
- ABOUT Claroty
Problem
From hospitals to industrial control environments, organizations today face growing threats due to the convergence of IT, OT and IoT. Healthcare providers must safeguard IoMT devices and patient data, while industrial operators must secure operational continuity against increasingly sophisticated cyberattacks. Whether protecting patient data in a hospital or securing critical production systems in a factory, visibility into every network-connected device is foundational.
Solution
Claroty and Garland Technology deliver real-time visibility and behavioral threat detection across industrial control systems and OT networks. Garland’s network TAPs ensure Claroty receives complete, unfiltered traffic to build baselines, detect anomalies, and secure critical assets.
Benefits
1. Deliver complete visibility into previously invisible industrial networks.
2. Continuously detect anomalies, known and emerging threats, and zero-day attacks.
3. Automatically provide root-cause analysis and risk-based scoring for all alerts.
4. More effectively detect, investigate, and respond to incidents that could potentially impact OT availability, reliability, and safety.
5. Reduce network downtime and monitoring deployment time with easy plug-and-play options that do not require configuration changes to existing infrastructure
About Claroty
![]()
Claroty is the industrial cybersecurity company trusted by the world’s largest enterprises. Claroty’s comprehensive platform seamlessly integrates with existing infrastructure while providing complete cybersecurity controls for visibility, threat detection, risk management, and secure remote access across OT, IoT, and IoMT environments.
For more information or technical support regarding the joint solution, please contact partners@garlandtechnology.com.
Visit Claroty at claroty.com.
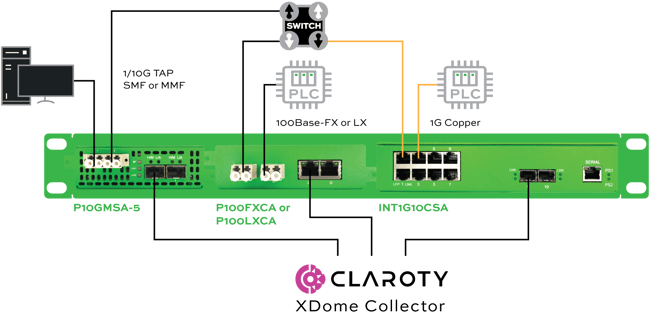
How It Works
- Garland Network TAPs are deployed between network appliances like switches, routers and firewalls from an IT, OT or IoT segment.
- TAPs send the full-duplex copies of traffic directly to the Claroty CTD or xDome sensors.
- To optimize traffic in distributed networks, Aggregator TAPs or Packet Brokers can aggregate multiple TAP or SPAN links from various segments back to the Claroty sensor.
- Claroty establishes behavioral baselines and detects threats within IT, OT and IoT environments for optimal threat detection.