Watch how Garland Technology helps Corelight.
Capture all data on the wire, transforming high-volume traffic into high-fidelity security data and insights.
Click to Learn More
When most cyber-attacks must cross the network, extracting relevant data from network traffic is essential for security operations. Many security teams have limited or no traffic visibility at the perimeter, leaving them blind to attackers who hide and establish malicious C2 server communications, deploy malware, and exfiltrate sensitive data.
Finding a way to reliably and cost-effectively capture and transform traffic into usable security data can be challenging, especially in environments with limited data center space and high throughput traffic. The Corelight and Garland solution takes minutes, not months, to deploy and emit actionable insights. The solution provides 100% visibility of your network for up to 10x peak performance gains and is packed with additional enterprise functionality from the creators and maintainers of Zeek.
Click to learn Integration Benefits
Integration Benefits
The Corelight and Garland Technology solution offers a scalable way to capture and efficiently make sense of 100% the network traffic no matter the environment. By dramatically accelerating network security operations with Zeek data, the solution reliably reduces blind spots in the network and the risk of any malicious data on the wire. Whether a lean or robust security team, the easy deployment and infinite features with Zeek data provide a comprehensive solution for security performance.
Click to view IT and Sec Ops Team Benefits
IT and Sec Ops Team Benefits
• Full visibility across on-premise data centers and private, public (AWS, Azure, Google), or multi-cloud environments.
• Easy access and monitoring of network traffic from physical, virtual, and cloud networks.
• Reduce network downtime, improve reliability, reduce costs, and gain better device utilization by spreading the load data across multiple tools.
• Extract over 400 fields of data from network traffic in real-time across 35+ protocols from Layer 3 to 7 (HTTP, DNS, SSL, ext.)
• The logs provide nearly the fidelity of full traffic at less than 1% of the file size.
•Logs are organized by protocol with fields extracted specifically for SOC / DFIR teams so that they can make fast sense of their network to threat hunt and resolve incidents more efficiently.
•Preloaded with the Core Collection, a set of Zeek packages curated and certified for performance and stability.
•Provide specific threat detection, data enrichment, and operational insight capabilities, such as identifying port scanning behavior or extracting URLs from email bodies for filtering.
TAP -> TOOL
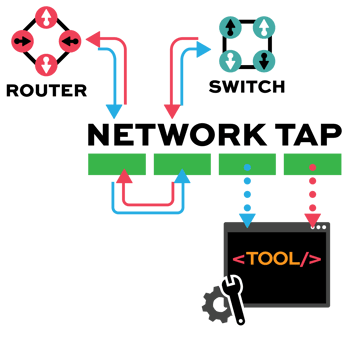
Network TAP Benefits
- Provide complete packet visibility with full-duplex copies of network traffic.
- Ensure no dropped packets while passing physical errors and support jumbo frames without delay or altering the data.
- Support speeds from 10/100M, 1G, 10G, 40G, 100G, and 400G are available in single-mode and multi-mode fiber or copper ethernet.
- Available in Tap ‘Breakout,’ aggregation, regeneration, bypass, and advanced filtering.
- Passive or failsafe – Does not affect the network.
- No IP address or MAC address, and cannot be hacked.
- Base Deployment
- Scalable Deployment
- Full PDF Solution Brief
- BLOG
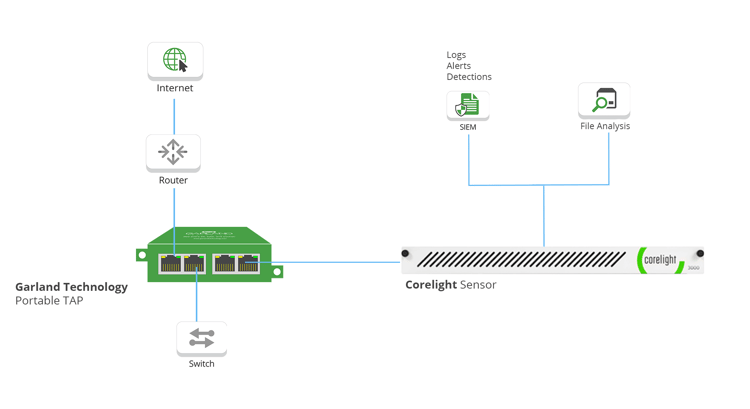
Base Deployment for Network Visibility and Security
-
Garland Technology’s compact, high-performance network TAPs provide 100% wire data.
-
A complete copy of network traffic is delivered to the out-of-band Corelight Sensor.
-
The Corelight Sensor captures and converts traffic for comprehensive protocol logs via the power of the Zeek Network Security Monitor.
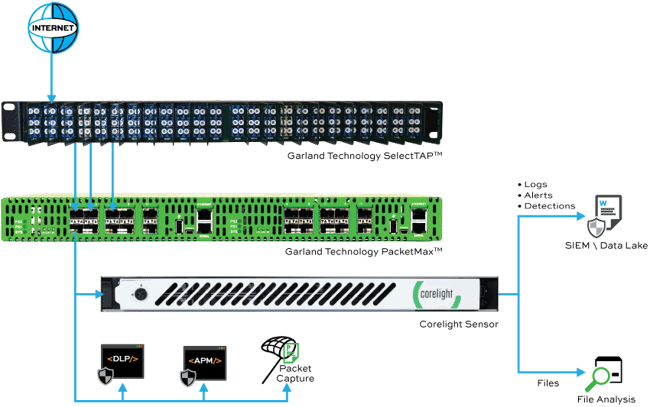
A Scalable Deployment For Growing Network Infrastructures
-
Garland Technology Network TAPs deployed at any links in a network create a 100% copy of the network traffic.
-
The tapped network traffic is then sent to a Network Packet Broker for traffic grooming, using features such as aggregation, load balancing, and deduplication.
-
The groomed traffic is then mirrored to the out-of-band Corelight sensor for analysis. Traffic is captured and converted to rich, correlated protocol logs and detections, providing users with critical security context of their network traffic.
-
Additional ports on the Garland Packet Broker can also send the same copies of the network traffic to additional security and monitoring tools as needed.





