Garland EdgeLens Solution
Garland’s EdgeLens series is an advanced bypass TAP with built-in packet broker functionality that centralizes network traffic, making network tools more efficient by sharing network traffic with monitoring and security tools. EdgeLens provides visibility for a hybrid configuration of an active, inline network device and out-of-band tools, such as LiveAction. EdgeLens provides identical network traffic streams through the active inline device and to the capture engine of LiveAction LiveWire or LiveCapture. The benefits of both devices seeing the same traffic are:
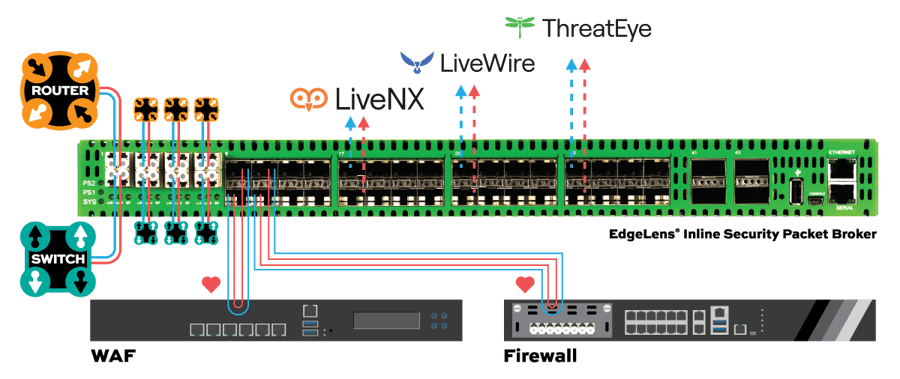
• Correlated data for real-time monitoring and root cause analysis using network packets.
• Historical look back and playback of the network traffic.
• Validating and updating network policy changes and spotting anomalies.
• Network data recording for compliance and security forensics.
• Root cause analysis for application and network related problems.
TAP -> TOOL
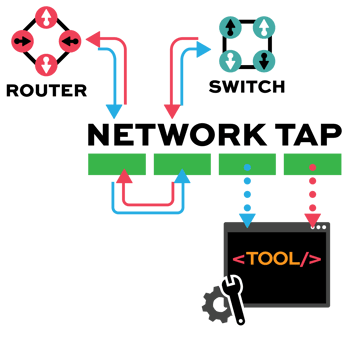
Network TAP Benefits
- Provide complete packet visibility with full-duplex copies of network traffic.
- Ensure no dropped packets while passing physical errors and support jumbo frames without delay or altering the data.
- Support speeds from 10/100M, 1G, 10G, 40G, 100G, and 400G are available in single-mode and multi-mode fiber or copper ethernet.
- Available in Tap ‘Breakout,’ aggregation, regeneration, bypass, and advanced filtering.
- Passive or failsafe – Does not affect the network.
- No IP address or MAC address, and cannot be hacked.

How It Works
1. Within the OT network, Garland Technology’s portable Network TAPs are deployed at key points within the network to provide access to the network traffic where there are unmanaged switches. The Network TAP provides complete packet level visibility to all of the traffic traversing the switch.
2. Portable Hardware Data Diodes are also used at other points within the environment where the SPAN port will be used as the access method, providing additional levels of security due to the unidirectional traffic guarantees ensured by the data diode.
3. Both the tapped traffic and the SPAN feeds are then sent to a Network Packet Broker to collect the traffic and aggregate, filter, and load balance to a LECS appliance.
4. With no configuration required, LECS can be deployed out-of-the box, to analyze the network traffic, detecting morphological and entropic anomalies using the triangulation of AI Analysis, Static and Heuristic engines. With its adaptive procedural responses, LECS can respond to threats instantly in an appropriate manner for the type and severity of the threat.
Key Benefits
Comprehensive network security and asset management
Rapid Deployment in Minutes
Quick, easy to deploy solution. Get started in as little as 10 minutes.
Intuitive Control & Visualization
Simplified control and visualization.
Always-On Passive Monitoring
Passive deployment, running 24/7 network monitoring.
Complete Packet-Level Insight
100% packet level visibility.
Advanced Multi-Tenant Management
Advanced multi-tenant control for IT/OT manager.
Rugged, Purpose-Built Hardware
Purpose-built hardware designed for extreme OT environments.
Extended Log Retention
Up to 30 days of log retention.
Untraceable Security Architecture
Secure and invisible to hackers since Network TAPs and Hardware Data Diodes have no IP or MAC address
Full PDF Solution Brief
Download our comprehensive solution documentation
What's Inside
- ✓ Technical specifications
- ✓ Diagram
- ✓ Use case scenarios
- ✓ ROI analysis
About Cyber Evolution
Detect, isolate, evolve
Today, in many business environments it is difficult to implement complex cyber security solutions and ecosystems especially to manage without specific know-how.
This is why simplifying the approach to cyber security allows companies and professionals to protect their infrastructure.
Our ethical mission therefore encompasses the deployment of scalable security solutions for all.
Schedule Your Network Solution Call Today
- How It Works
- Bypass TAP Benefits
- Full PDF Solution Brief
- How It Works
- How It Works
- How It Works
Bypass manages the availability of inline tools, preventing a single point of failure in the network by “bypassing” the device in the event it fails or needs to be updated. Reducing network downtime. Bypass is unique to the other TAP modes, as it is an inline use case not out-of-band.
• Keep up with Federal security mandates
• Expedited problem resolution
• Ability to pilot or deploy need security tools
• No maintenance windows
• Simple configuration ensures a quick set-up
• Zero subscription fees so O&M expenses don’t increase
■SOLUTION EDGESAFETM BYPASS TAP
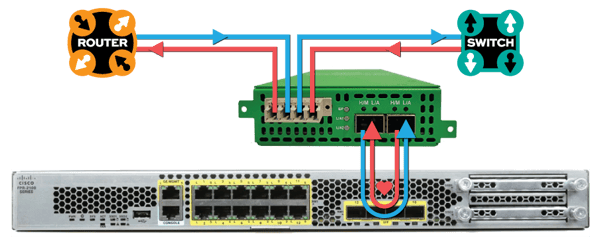
• Install a Garland Technology Bypass TAP between Cisco Firepower and the network
• Bypass TAP manages the availability of Firepower at any time without having to take down the network
• Bypass TAP continuously checks the health of Firepower with heartbeat packets and the Bypass TAP will bypass Firepower to keep the network up-and-running in the event Firepower becomes unavailable
| PROBLEM 1 PORT FAILURE | ||
|
■WITHOUT TAP • The network |
|
■WITH TAP • Uptime • Tool is bypassed while it is being updated |
| PROBLEM 1 PORT FAILURE | ||
|
■WITHOUT TAP • The network |

|
■WITH TAP • Uptime • Tool is bypassed while it is being replaced |






