e2e assure
Expecting a PDF?
We created this solution brief as a web page for better mobile optimization and accessibility. If you'd still like a PDF version of this use case, you can download it here:
Full network visibility and 24/7 threat detection is best left to the professionals
Today, no business, corporation, or institution is immune to cybersecurity threats. Malicious actors are growing more sophisticated and creative by the day, forcing organizations to regularly invest in network security. The damage caused by cyberattacks can be measured in tangible and intangible ways: ransomware payments, network downtime, disruption of services, and loss of reputation. Cybersecurity is both a capability and cost of doing business that cannot be delayed.
With a seemingly infinite number of security solutions in the marketplace and a shortage of trained professionals in the workforce, protecting a network poses major challenges for entities large and small. Fortunately, there are Security Operations Center (SOC) services available to companies interested in outsourcing the management of their network security.
e2e and Garland Technology provide peace of mind
e2e is a leading UK SOC provider with a global presence. Their network threat detection expertise protects the networks of public and private organizations. Cumulo - e2e’s in-house developed, maintained, and evolving SOC platform - delivers Protective Monitoring and SOC Services. Working with Garland Technology, e2e has a complete picture of the network threats and network traffic. Garland’s network TAP (Test Access Point) and Packet Broker solutions guarantee 100% of network packets are sent to e2e’s sensors, enabling them to view the live traffic and identify any threats in real-time. Businesses can rest easy knowing e2e and Garland have eyes on their networks.
Business Benefits
• Prevent unexpected and unplanned costs resulting from cyberattacks
• Avoid risks to operations, services, and competitive advantage if attacked
• Increased security monitoring coverage at a reduced cost
• Eliminate need to recruit and hire in-house, cybersecurity capabilities
• Eliminate need to invest in network security hardware and software
• Access to the latest expertise, training, and processes to keep the network protected
• Focus on the core competencies of the organization
• Flexibility and scalability - adjust protections as you grow
Functionality Benefits
• 100% network visibility (including pcap) with full-duplex copies of traffic sent to the security sensor
• No dropped packets and no blind spots in the network
• Network TAPs do not have an IP address or MAC address, and cannot be hacked.
• A single holistic view of risk and threats across the enterprise, including private and public cloud infrastructure
• Speed of delivery - can be rapidly integrated into your environment
• Identify threats before they become incidents
• Assists standards compliance for ISO27001:2013, Cyber Essentials Plus, and PCI
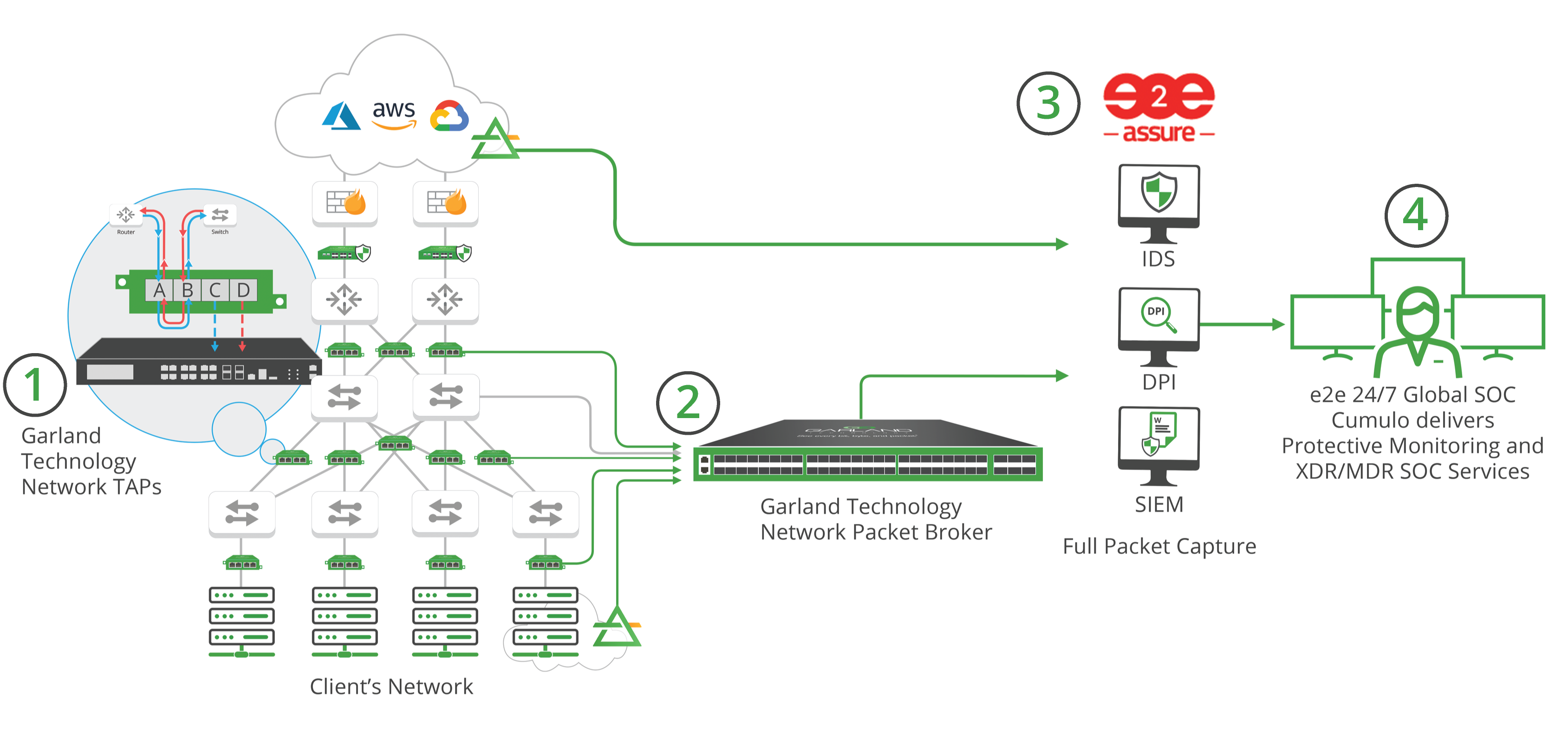
HOW IT WORKS
-
Physical and virtual network TAPs copy full-duplex traffic from the network.
-
SPAN and/or Tapped traffic is delivered to Garland Technology’s PacketMAXTM Advanced Features Packet Broker for aggregation, load-balancing, and deduplication.
-
e2e processes the optimized data provided by Garland Technology in a full packet capture environment with Intrusion Detection Systems (based on Talos SNORT), deep packet inspection, and SIEM log/event data.
- e2e’s fully-staffed, 24/7 Global SOC - Cumulo delivers Protective Monitoring and XDR/MDR SOC Services - analyzes data to identify any threats to the network’s security to ensure a real-time incident response.
About e2e
e2e-assure is a specialist SOC-as-a-Service XDR an MDR provider. We provide our service as a full outsource, a hybrid model, or as a platform-as-a-service to end customers as well as partners. We can either provide all the SOC technology with the service or we integrate with and leverage existing investments in cybersecurity including SIEM, cloud security, and endpoint solutions so we can deliver our service quickly and effectively, without duplicating costs.
We have the UK and Australia-based SOCs and focus on recruiting and training the best talent. We service customers globally from SMEs to large multinationals and large government
organizations. We have specialist security-cleared in-country teams for the UK and Australia defence, government, and critical national industry customers.

Garland Technology and e2e provide complete packet-level visibility and threat detection. Looking to add this solution, but not sure where to start? Join us for a brief network Design-IT Demo or consultation. No obligation - it’s what we love to do.
