Eliminate Blind Spots
IT Security Solutions
Challenge: How do I eliminate blind spots in my network?
“Blind spots” refer to the inability to analyze the data between certain segments in a network, and may seem “hidden” to your monitoring tool and can compromise network performance and security. If a network expands without a proper visibility fabric in place, blind spots may become apparent. These blind spots happen for a variety of reasons, including:
• There has been an addition of new network equipment or applications. The additions are not properly architected or the team overseeing this data is not planned out.
• New deployments can lead to network complexity. When new links, new equipment or remote locations are introduced, they can be configured with separate management or teams, making it hard to track what is happening in these segments
• SPAN ports present a host of opportunities for blind spots – SPAN port contention issues, dropping packets and creating a loss of information, improper SPAN port programming – all resulting in incorrect or missing data captures.
• Introducing virtualization – the migration to a virtualized data center environment is known for introducing blindspots into the network. The evolution of Kubernetes & Containers has created blind spot challenges, along with a maturing industry that is just catching up with proper mirroring technology.
Solution
Network TAPs Guarantee Tools Complete Packet Data
Network performance monitors (NPMs) can be used to determine areas within a network that aren’t performing as they should, letting you know where the visibility problem may be located. Network TAPs, an industry best practice over SPAN ports, create a “foundation of visibility,” providing the ability to capture network monitoring data without compromising the network, removing blind spots.
"Research found that 83 percent of current network visibility fabrics use TAPs for at least half of the fabric access layer.” -EMA [Enterprise Management Associates]
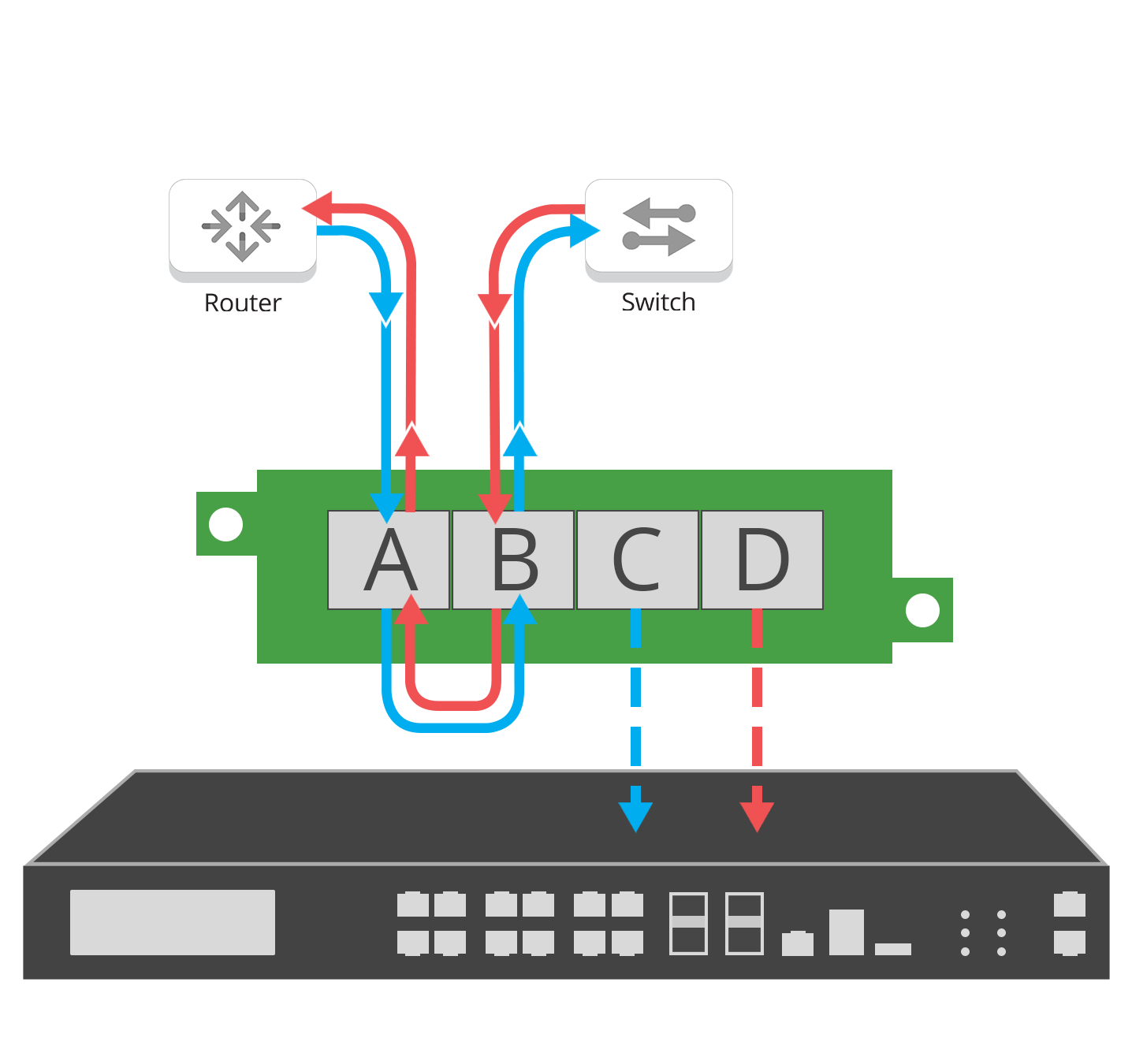
Network TAPs are used to help IT teams easily monitor all network data. A network TAP is a purpose-built hardware device that allows you to access and monitor your network traffic by copying packets without impacting or compromising network integrity.
They are typically placed between any network devices like switches, routers, and firewalls, creating an exact copy of both sides of the traffic flow, continuously, 24/7/365. The duplicate copies can be used for monitoring, security, and analysis, while the network flow continues uninterrupted. TAPs do not introduce delay, or alter the data. They are either passive or “failsafe,” meaning traffic continues to flow between network devices if power is lost or a monitoring tool is removed.
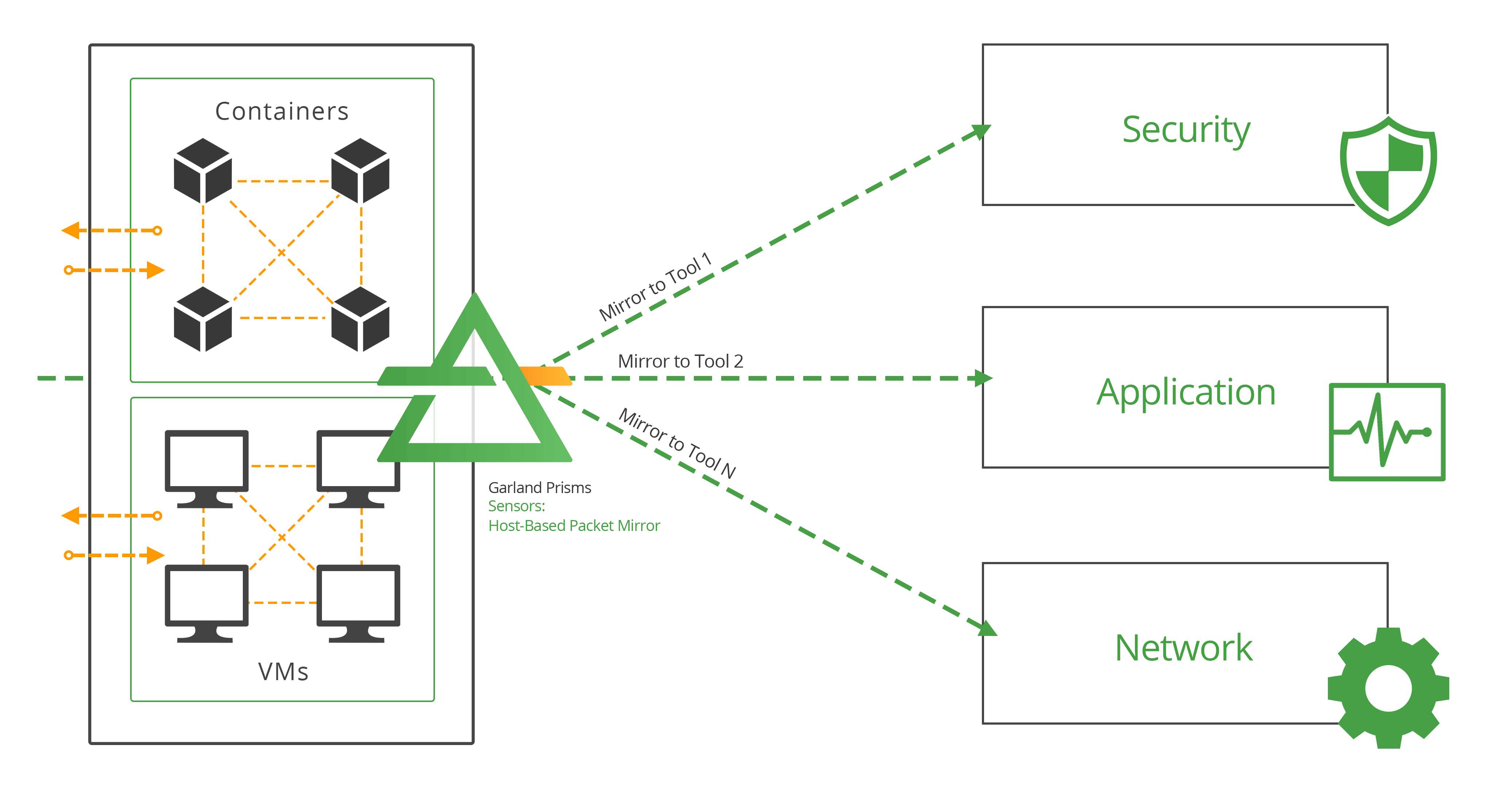
Provide Complete Cloud Traffic Mirroring
A cloud traffic mirroring solution like Garland Prisms, enables your network-based tools to see deeper into your modern compute environments, providing visibility into Kubernetes and cloud environments without impacting performance or architectures and without modifying your deployment architectures. Acquire traffic from your dynamic workloads, scaling with them so packets are never missed, helping you achieve true network traffic analysis visibility so that you can maintain control over your cloud environments. By guaranteeing 100% packet capture from your clouds, you’re able to leverage additional visibility tools to satisfy advanced filtering and aggregation use cases.