Providing 100% visibility, in real-time, all the time
Network TAPs
Network Test Access Point (TAP)
Guarantee 100% data capture in real time, all the time
Test Access Points (TAPs) are a simple, yet important concept. A network TAP is a purpose-built hardware device that allows you to access and monitor your network traffic by copying packets without impacting or compromising network integrity. The TAP allows network traffic to flow between its network ports without interruption, creating an exact copy of both sides of the traffic flow, continuously, 24/7, 365. The duplicate copies are then used for monitoring and security analysis.
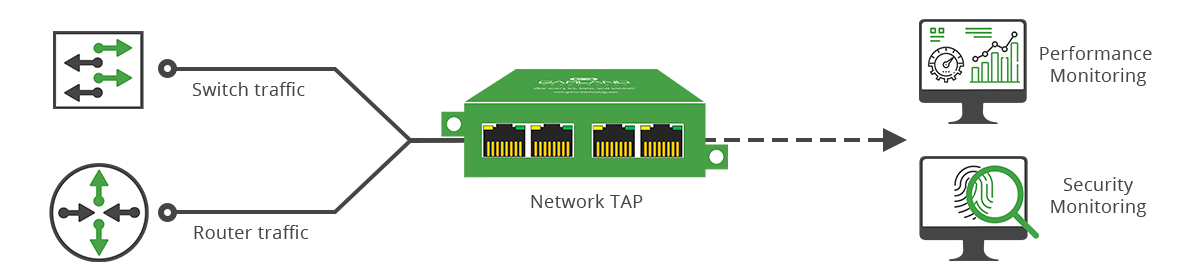
Network visibility is more critical than ever. Networks are getting more complex with higher speeds carrying an increasingly unprecedented amount of data, in addition to the ever evolving threat of sophisticated cyber security risks. With the growing number of analysis and security tools needed to process this data, a granular visibility approach into the packet data running on the wire is a must.
“EMA recommends that enterprises use TAPs as much as possible in the access layer to avoid network performance impacts and assure packet fidelity.”
-EMA [Enterprise Management Associates]
How do network TAPs work?
Instead of two network segments, say a router and switch, connected directly to each other, a network TAP is placed in between them, connecting both devices.
The data is still transmitted between the two network devices (e.g. routers and switches) in both directions, east and west traffic. TAPs then copy the transmit signals from each device and sends them to separate monitoring ports. This ensures every packet is copied and eliminates any chance of oversubscription, without additional impact or burden to the network.

Figure 2. East/West traffic flow
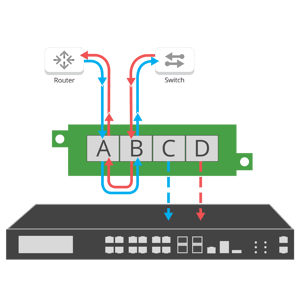
Figure 2. East/West traffic flow with network TAP
Different Types of TAPs
Network TAPs are purpose-built for a variety of different environments and specifications, as they accommodate different requirements needed to perform - all providing the same full duplex visibility.
• Passive TAPs support out-of-band “listen-only” monitoring tools, and are simple, reliable and require no power. Passive TAPs are typically 1G to 100G fiber or 100M copper.
• Active TAPs support additional functionality like aggregation and regeneration as well as advanced functions like filtering and bypass. Active TAPs include failsafe technology to protect against device or power failure.
• Virtual TAPs support virtualized environments, mirroring traffic out of containers, VMs, and Kubernete workloads to your trusted monitoring tools.
For each of these different types:
• TAPs are available in various media types, including copper or fiber (LC, MTP/MPO, BiDi), SFP, SFP+ and can perform Media Conversion.
• TAPs are available in various speeds from 10/100/1000M all the way to 100G.
• TAPs form factors including pocket-size portable, rack mount portable, 1U and 2U modular and high density chassis.
TAP Modes
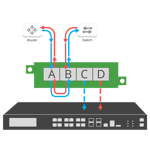
Tap 'Breakout' mode
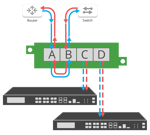
Tap Aggregation
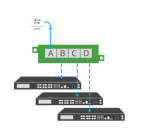
Regeneration
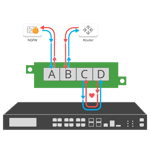
Inline Bypass
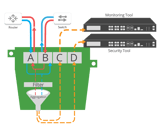
Advanced Filtering
Not all TAPs are created equal — Some Network TAPs can perform multiple functions and modes within the same device, which allows you the flexibility to optimize your tools and network. These functions reflected in the above diagrams include:
- TAP 'Breakout' (often referred to as just TAP or TAP mode) is the most common function TAPs provide. 'Breakout' sends each side of traffic to separate monitoring ports. Ensuring that no packet is lost to high-priority monitoring tools.
- Aggregation merges both sides of the traffic streams into one monitoring port to reduce appliance costs or consolidate packet broker ports, often used in combination with filtering TAPs, (e.g. filter and aggregate data streams).
- Regeneration/SPAN creates multiple copies of network data to support multiple devices from a single tapped link. This allows you to send the same data to multiple destinations.
- Bypass manages the availability of inline tools, preventing a single point of failure in the network by “bypassing” the device in the event it fails or needs to be updated. Reducing network downtime. Bypass is unique to the other TAP modes, as it is an inline use case not out-of-band.
- Filtering, usually associated with network packet brokers, allows you filter specific data streams you want tapped and monitored. Filtering also prevents ports from becoming oversubscribed during aggregation. Another feature to help optimize the function of your tools and network.
Copper Network TAP Configurator
Find the perfect TAP solution for your network in just a few steps!
Why use our configurator?
- Save time in product selection
- Ensure compatibility with your network
- Get personalized recommendations
Why use a Network TAP?
Network TAPs solve many issues. Let's explore network TAP use cases to see why:
Creating a foundation of visibility is key for network management. Once deployed, network TAPs allow you to access that point in your network at any time. Many organizations have adopted the stance of tapping all critical links for easy access during troubleshooting or inevitable security breaches.
Industry Best Practice
"SPANs can add overhead on a network device, and that SPAN port will often drop mirrored packets if the device gets too busy. Therefore, TAPs are a better option.”
-EMA [Enterprise Management Associates]
• Do a little research, as not all TAPs are equal. Before making a decision on which TAP to go with, look into the quality, testing, where they are manufactured, hardware warranties, optical transceivers, Mean Time Between Failure (MTBF) rates and first time pass rate (FTPR).
• A common TAP misconception is that it’s an unnecessary single point of failure (SPOF). Most TAP failures can be traced to improper cabling, unclean connectors or user error. With a zero failure rate in the field, Garland Technology tests and verifies all TAPs with live network data ensuring your network has full access and visibility.
• Some Active TAPs offer battery backup to extend usage during power failures. We do not recommend this due to the dangers associated with having lithium ion batteries in your network. Most high quality TAPs have power failsafe, do not need any power source, or they have a backup AC source.
Network TAPs Resources

Network TAPs 101
This eBook provides fundamental information on network connectivity for a variety of monitoring, security and analytical deployment scenarios.

TAP vs SPAN
An in-depth look into network visualization access, and what security, monitoring, management, compliance, and capture today’s networks require.
Additional Resources
TAP into Technology
Leading the way in Network Technology

The 101 Series: Out-of-Band vs Inline Network Security
| October 8, 2025
Designing a modern cybersecurity strategy is no easy feat, as it must protect all components of a complex network, while having a limited effect on..

The 101 Series: Passive Network TAPs
| July 23, 2025
Companies that are using network monitoring tools, either for analyzing security threats, packet flow or Key Performance Indicators (KPIs) – all have..

The 101 Series: Bypass Network TAPs Protectors of the Critical Link
| May 14, 2025
Introduction Typically, a network TAP (test access point) is a device that creates a full duplex copy of 100% of the network traffic flowing between..








