OT TAP vs SPAN
ICS Visibility Solutions
Challenge: How do I access data for my tools?
Securing and monitoring your network is the ultimate goal. But OT teams face complex challenges when it comes to architecting connectivity throughout large and sometimes aging infrastructure that wasn’t initially designed with network security in mind.
There are two options to access network packets for security and monitoring solutions to properly analyze threats and anomalies, as well as performances and regulatory conditions — network TAPs and SPAN ports.
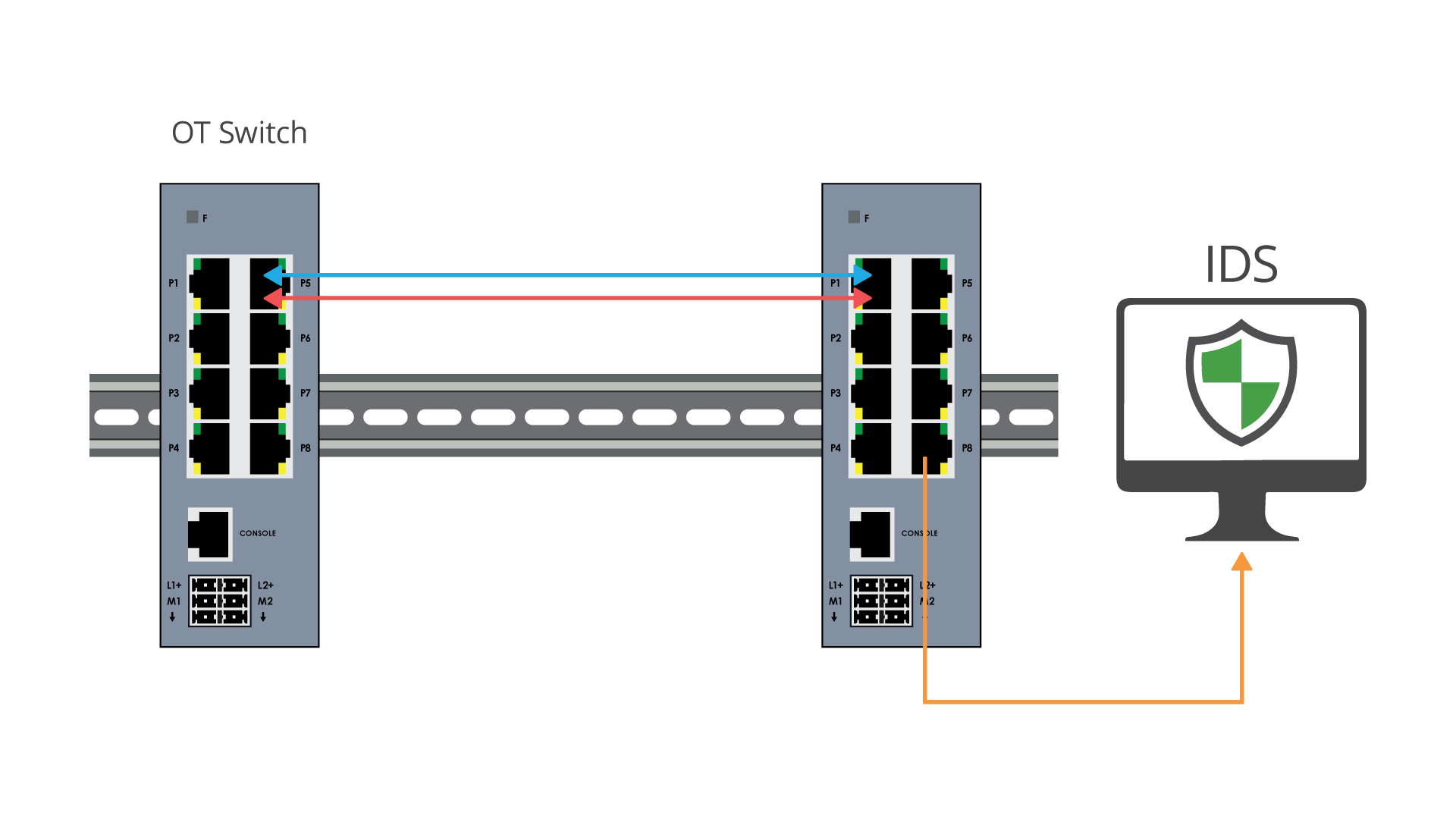
SWITCH SPAN PORTS
A common visibility use case is to route mirrored traffic from a SPAN port on the switch to a security or monitoring tool. Port mirroring also known as SPAN (switched Port Analyzer), is a designated port on a network switch that is programmed to mirror, or send a copy, of network packets seen on a specific port (or an entire VLAN), where the packets can be analyzed.
• Provides access to packets for monitoring
• SPAN sessions do not interfere with the normal operation of the switch
•Configurable
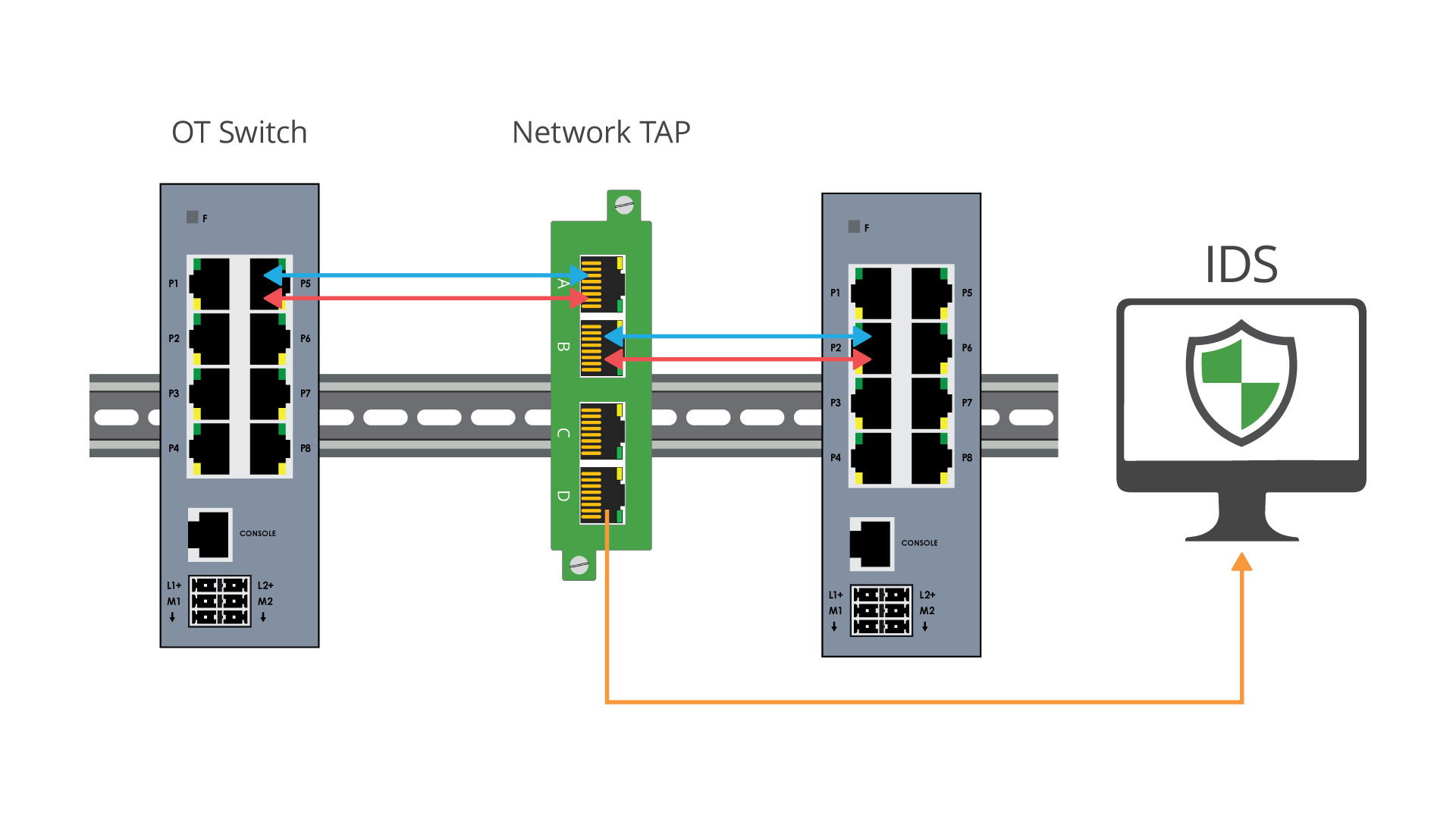
NETWORK TAPs
The industry best practice for packet visibility are network TAPs (Test access points). Network TAPs are purpose-built hardware devices that create an exact copy of the network packet data, continuously 24/7 without compromising network integrity.
•Network TAPs make a 100% full duplex copy of network traffic
•Network TAPs do not alter the data or drop packets
•Network TAPs are scalable and can either provide a single copy, multiple copies (regeneration), or consolidate traffic (aggregation) to maximize the production of your monitoring tools

• Provides 100% full duplex copies of network traffic
• Ensures no dropped packets, passing physical errors and supports jumbo frames
• Does not alter the time relationships of frames
• Passive or failsafe, ensuring no single point of failure (SPOF)
• TAPs are secure, do not have an IP address or MAC address, and cannot be hacked
• CALEA (Commission on Accreditation for Law Enforcement Agencies) approved for lawful intercept, providing forensically sound data, ensuring 100% accurate data captured with time reference
• Data Diode TAPs provide unidirectional traffic to protect against back flow of traffic into the network
• Scaleable for traffic optimization and can aggregate multiple links down to one
• Provides access to packets for monitoring
• Can take up high value ports on the switch
• SPAN traffic is the lowest priority on the switch
• Some legacy switches do not have SPAN available
• SPAN ports drop packets, an additional risk for security and regulation solutions
• Will not pass corrupt packets or errors
• Can duplicate packets if multiple VLANs are used
• Can change the timing of the frame interactions, altering response times
• Bidirectional traffic opens back flow of traffic into the network, making switch susceptible to hacking
• Administration/programming costs for SPAN can get progressively more time intensive and costly
Following critical infrastructure’s guiding principles — you want your network to be built to last, while ensuring minimal to no network downtime. These concepts rest on the network infrastructure and visibility architecture. Being built by incorporating best practices are what’s going to help you achieve these goals.
