Improve SecOps Strategies at the Edge, Data center and Enterprise
IT Security
You can't secure, what you cannot see
IT security, whether deployed at the edge of the network, within a traditional data center or enterprise, all have a common theme — cybersecurity tools need proper packet visibility to protect. Or commonly stated — you can’t secure what you cannot see.
Threat detection, Intrusion detection systems (IDS) and forensics tools rely on complete packet data to properly analyze for network protection. Network blindspots and dropped or duplicated packets inhibit the performance of these tools, potentially missing anomalies or threats. In today's cybersecurity environments, this is not acceptable. Network TAPs ensure best practices for instrumenting packet visibility for out-of-band monitoring tools, over the commonly used switch SPAN.
“[An attacker's] worst nightmare is that out-of-band network tap that really is capturing all the data, understanding anomalous behavior that’s going on, and someone is paying attention to it. You’ve gotta know your network, understand your network, because [the attacker] is going to.”
-Rob Joyce, Director of Cybersecurity at the National Security Agency (NSA)
Simplify your security stack
Today’s cybersecurity strategies incorporate both inline and out-of-band solutions, with a suite of active blocking and passive monitoring tools. Many security teams are looking for ways to future proof their network ahead of the Edge explosion by architecting remote locations and data centers with purpose-built inline bypass, packet broker and cloud visibility solutions, which provide the resiliency and performance your tools need to ensure these segments are secure and scalable.
Garland Technology’s full line of inline bypass TAPs and packet brokers are designed to simplify modern security stacks, with the first integrated bypass family to handle your entire security strategy — from remote sites, data center and enterprise. Schedule a Design-IT Demo or consultation on how to implement these solutions into your environment.
How to Improve Threat Detection
and Threat Prevention Tools
Out-of-band Threat Detection
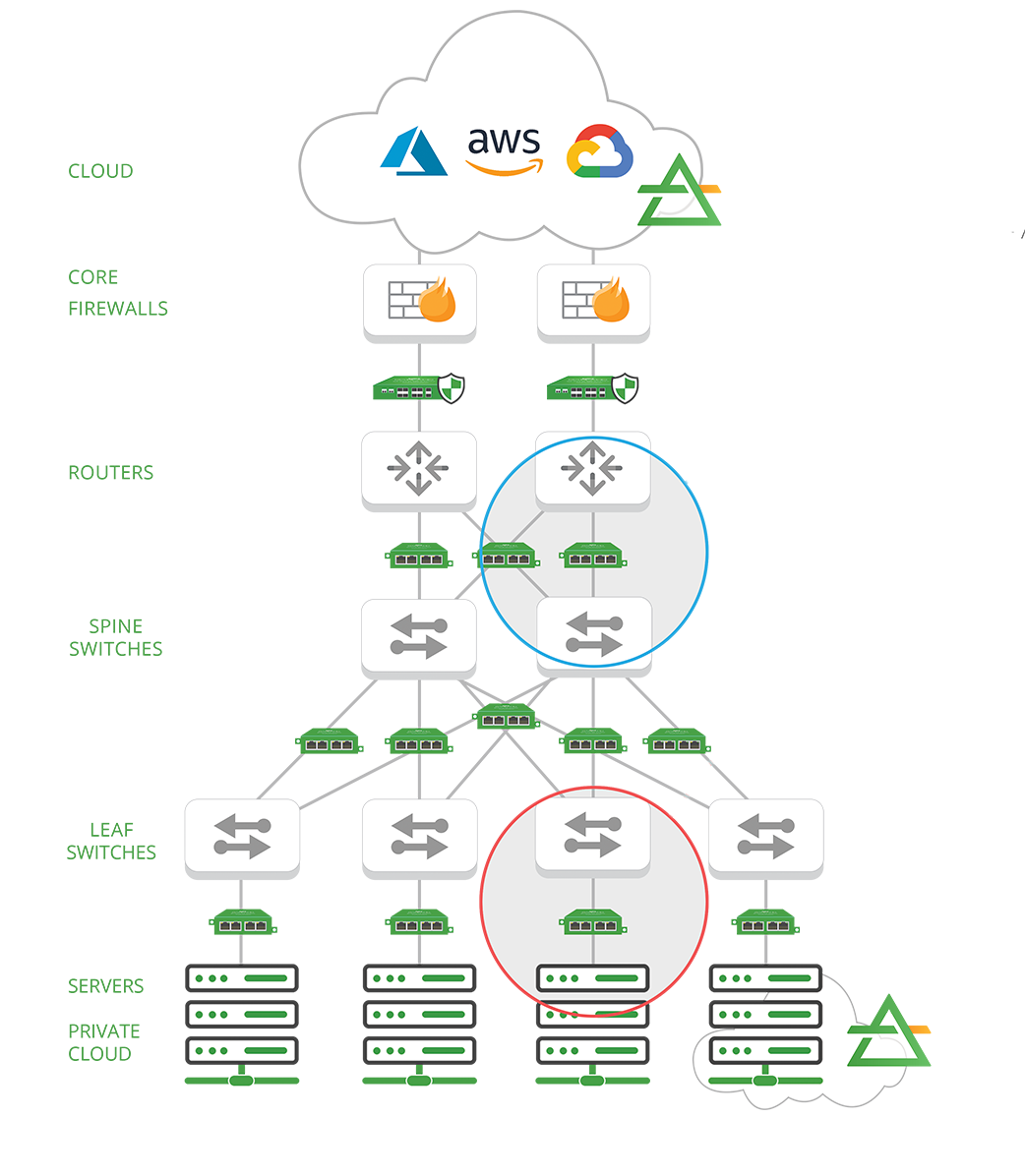
For out-of-band security threat detection tools like Intrusion detection systems (IDS), Network detection and response (NDR), Threat Intelligence, SIEM, DDoS, Data loss prevention and traffic analysis – providing a cohesive visibility fabric of network TAPs and Network Packet Brokers improves tool performance tasked with solving various security strategies, including:
• Improved forensics detection, ensuring no dropped packets and blindspots mask threats
• Reduce MTTR (Mean time to resolution) by guaranteeing data quality and integrity, leading to faster analysis and resolution
• Improve tool performance -- get more out of existing or lower speed tools
• Regain cloud visibility with traffic mirroring
• Provide CALEA (Commission on Accreditation for Law Enforcement Agencies) compliant forensics packet capture data in lawful interception cases
Inline Threat Prevention
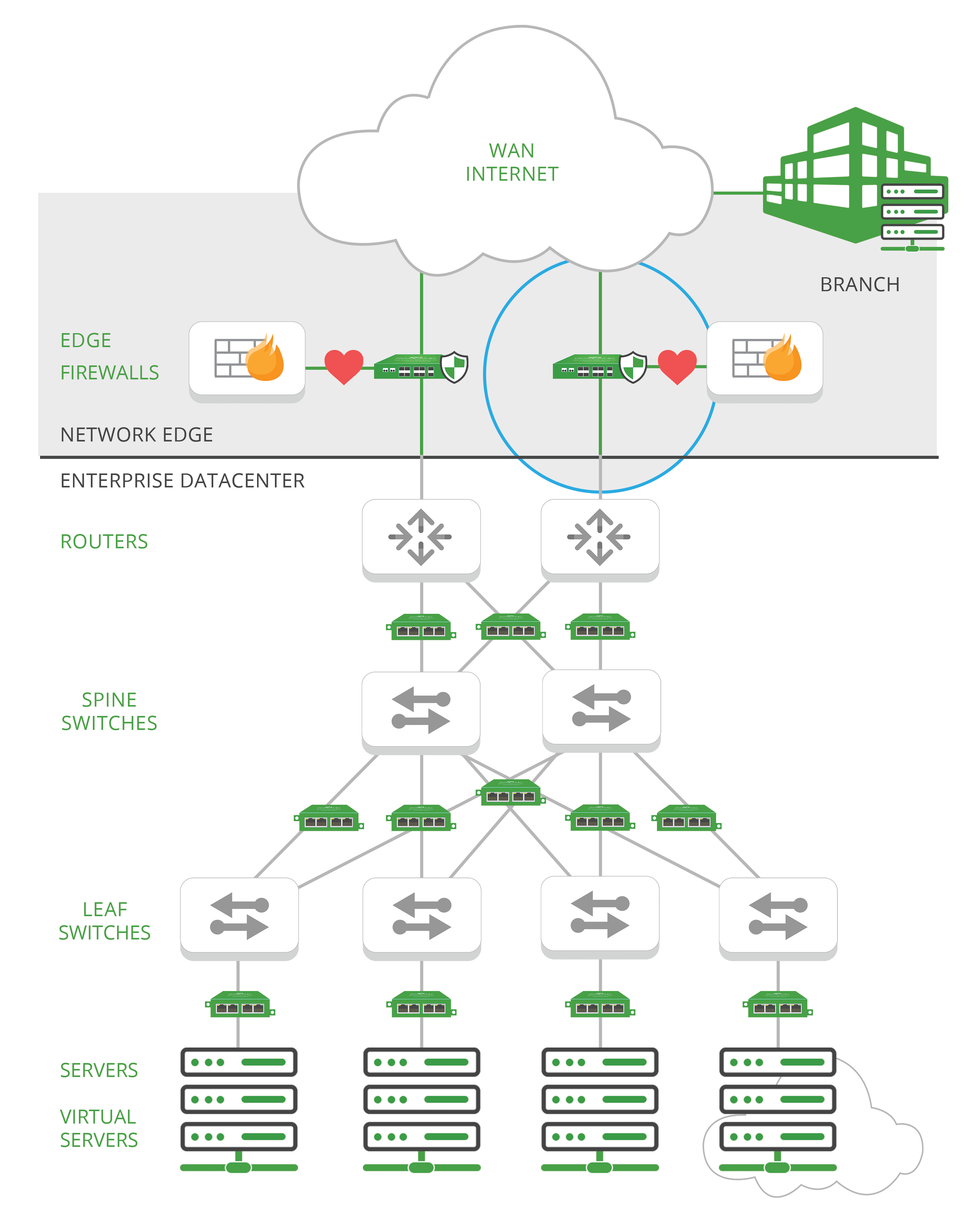
For inline security, threat prevention or active blocking tools like intrusion protection systems (IPS), firewalls, web application firewalls (WAF), and SSL decryption, that sit in the live network traffic, and are used to analyze traffic in real-time – inline bypass TAPs and Packet Brokers ensure their performance, optimization and resilience by:
• Eliminating single points of failure within your network
• Reduce network downtime, with inline lifecycle management cutting deployment time and saving budget
• Optimize inline tool performance to ensure threat protection
• High availability (HA) inline deployments adds additional layers of resiliency and reliability
IT Security Best Practices
Ready to solve an issue? Let's explore network security use cases:
Out-of-Band
Inline
Bypass functionality is essential to preventing inline security devices from causing network performance degradations and downtime. Many appliances have internal bypass capability, but external bypass devices are considered more reliable and offer more features.

IT Security Resources

IT Security
Today’s security strategies incorporate both inline and out-of-band solutions, of active blocking and monitoring tools. This whitepaper will review how these tools are being used and what industry best practices and use cases may help improve your next deployment.

3 Keys to Network Resiliency
Learn how to expedite troubleshooting & shorten your maintenance windows with the ability to update, repair, and replace security appliances without bringing down the network.
Webinars
- How To Build a Zero Trust Security Visibility Architecture
- How to Mirror Cloud Packets for Incident Response and Threat Hunting
- The Threat You Can't See -TLS & Cybersecurity
- Architecting Visibility into Blind Spots through SSL Decryption
- Complete Network Visibility and Security for Mission-Critical IT operations
TAP into Technology
Leading the way in Network Technology













