Stamus Networks
Watch how Garland Technology helps Stamus Networks.
Network TAPs and Network-based High Performance Threat Detection.
- PROBLEM
- SOLUTION
- BENEFITS
- ABOUT STAMUS NETWORKS
PROBLEM
Keeping an enterprise network and associated assets secure is an immense responsibility. Organizations large and small cannot properly deliver on their promise to stakeholders without a well-functioning and secure network infrastructure. At the same time, the pressures on cyber defenders to quickly assess and respond to threats such as attacks from ransomware and spyware, in realtime, is intense. Lack of visibility into segments of the network or a single ignored warning can turn a demanding day into a stressful scramble at best, and possibly even a serious breach.
SOLUTION
Effective enterprise network-based threat detection and response is possible with the Stamus Security Platform (SSP) from Stamus Networks. Stamus Security Platform delivers broad-spectrum threat detection in an open system, providing defenders with response-ready and high-fidelity notifications from machine learning, stateful logic, and signatures.
To do so, SSP inspects all network traffic from a Garland Technology Network TAP. Network TAPs are the most reliable way to ensure the Stamus Security Platform has full visibility into all segments of the enterprise network. Garland’s Network TAPs deliver copies of full duplex traffic from the network to the Stamus Security Platform immediately upon installation. SSP then helps SecOps and NetOPs with automated detection, proactive threat hunting, incident investigation, and IT policy enforcement.
BENEFITS
The joint solution from Stamus Networks and Garland Technology ensures threat detection and insights are prompt and turnkey. This solution offers complete visibility of enterprise network traffic, detecting threats that other methods miss. This complete
visibility into network activity, coupled with high-fidelity detection and automated event triage, allows security operations personnel to focus on serious and imminent threats. Also, this visibility with over 4,000 unique elements of network metadata allows network operations teams to effectively maintain and troubleshoot the network.
An added benefit of connecting the Stamus Security Platform using Network TAPs is the added peace of mind that Network TAPs will not be an added vulnerability in the network. Network TAPs cannot be hacked because they do not have an IP address or MAC address. Also, because Network TAPs do not drop packets, the Stamus Security Platform is guaranteed to receive all the network traffic needed to perform its job properly. Network TAPs will never oversubscribe the Stamus Security Platform or negatively affect network uptime.
About Stamus Networks

Stamus Networks believes in a world where defenders are heroes, and a future where those they protect remain safe. As organizations face threats from well-funded adversaries, we relentlessly pursue solutions that make the defender’s job easier and more impactful. A global provider of high-performance network-based threat detection and response systems, Stamus Networks helps enterprise security teams know more, respond sooner and mitigate their risk with insights gathered from cloud and on-premise network activity. Our solutions are advanced network detection and response systems that expose serious and imminent threats to critical assets and empower rapid response.
HOW THE SOLUTION WORKS
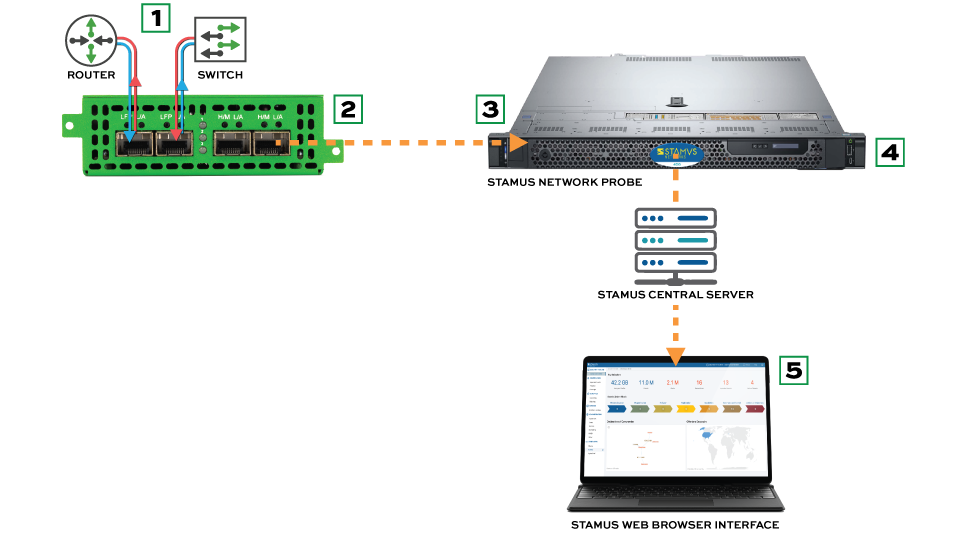
1. Network TAPs from Garland Technology connect to the on-premise IT network by installing between two network devices.
2. One or more Stamus Network Probes connect to the network TAPs.
3. Network TAPs copy full-duplex traffic and send the copies to the out-of-band Stamus Network Probes.
4. The Stamus Network Probes, which are based on the Suricata open-source network security engine, receive copies of the traffic and perform real-time threat detection, enrich the resulting events with extensive metadata, and capture network protocol transactions.
5. Stamus Network Probes then feed the Stamus Central Server for additional threat detection and advanced analytics along with a guided threat hunting interface. Users access the entire system via web browser.


