Tenable
Identify Vulnerable Traffic With Non-Intrusive Continuous Visibility
Expecting a PDF?
We created this solution brief as a web page for better mobile optimization and accessibility. If you'd still like a PDF version of this use case, you can download it here:
Eliminating Blind Spots to Detect and Decrypt Deep Packet Traffic
When securing your network, obtaining useful data to reduce vulnerabilities is the epicenter of an infrastructure. To protect your data, acquiring a full picture of your network is important since various security issues arise when data traffic is missed. By gaining complete packet-level visibility, networks can ensure continuous monitoring by detecting vulnerabilities in potential blind spots. Because these files are difficult to detect, security devices require active scanning and continuous non-intrusive monitoring.
The Tenable OT Security and Garland Technology’s visibility solution provide fully comprehensive solutions for optimal data collection and continuous visibility. Delivering a full stream of network visibility and continuous monitoring, the solution completes active scanning with non-intrusive monitoring.
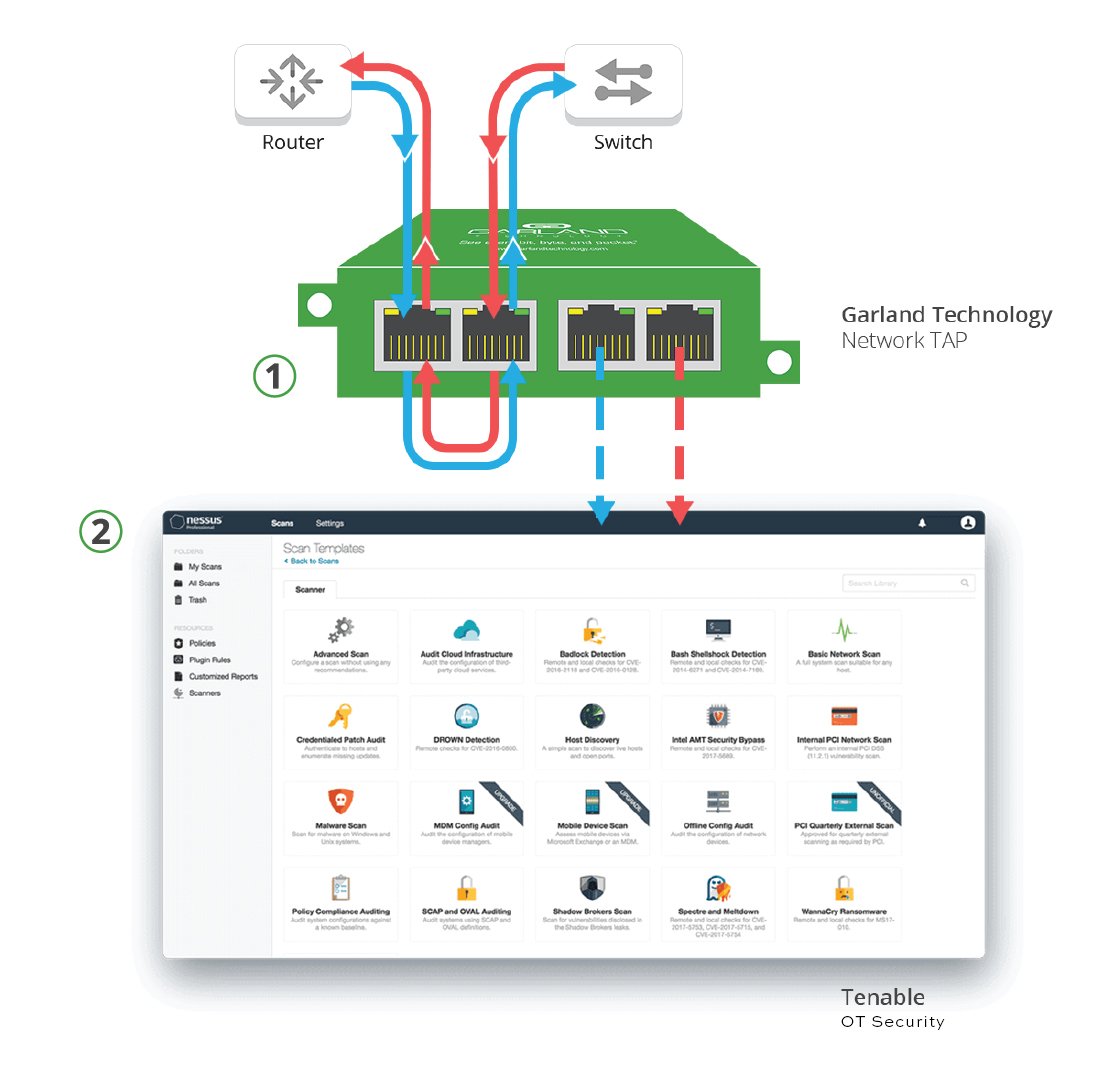
Portable Solution For Quick Monitoring Performance
HOW IT WORKS
1. For easy network access, Garland’s Portable TAPs provide complete packet visibility from any segment.
2. The packets are delivered to the Tenable OT Security, which delivers continuous monitoring and profiling of assets and analyzes network traffic at the packet level to provide visibility to vulnerabilities with full asset discovery.
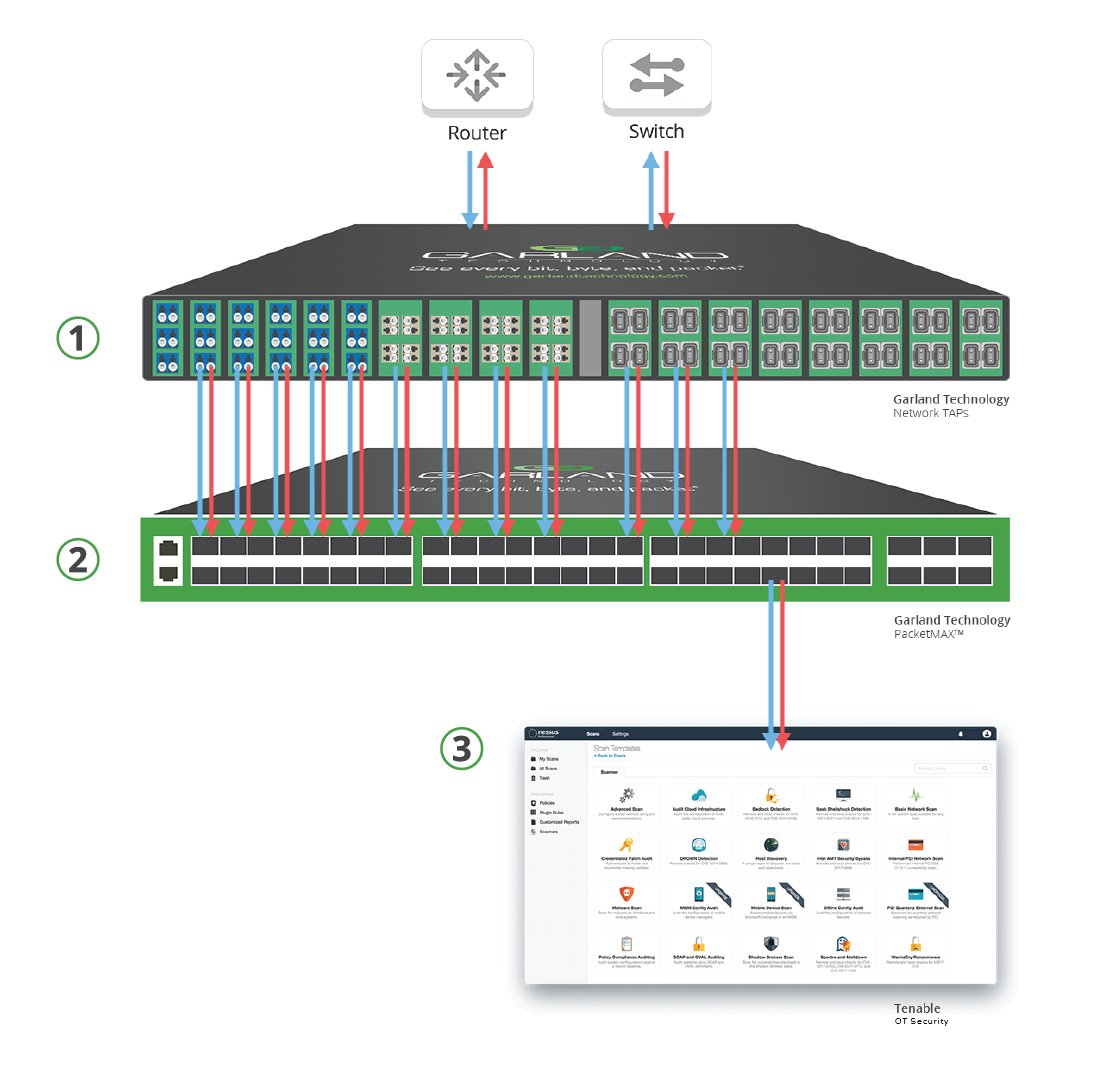
Scalable Security at the Perimeter of Your Network Infrastructure
HOW IT WORKS
1. The modular Garland SelectTAPTM provides complete packet visibility and scalability to maximize port efficiency.
2. The PacketMAXTM aggregates, load balances, filters, and then distributes the optimized tapped traffic.
3. The aggregated traffic is sent to the Tenable OT Security where the data traffic is managed and monitored.
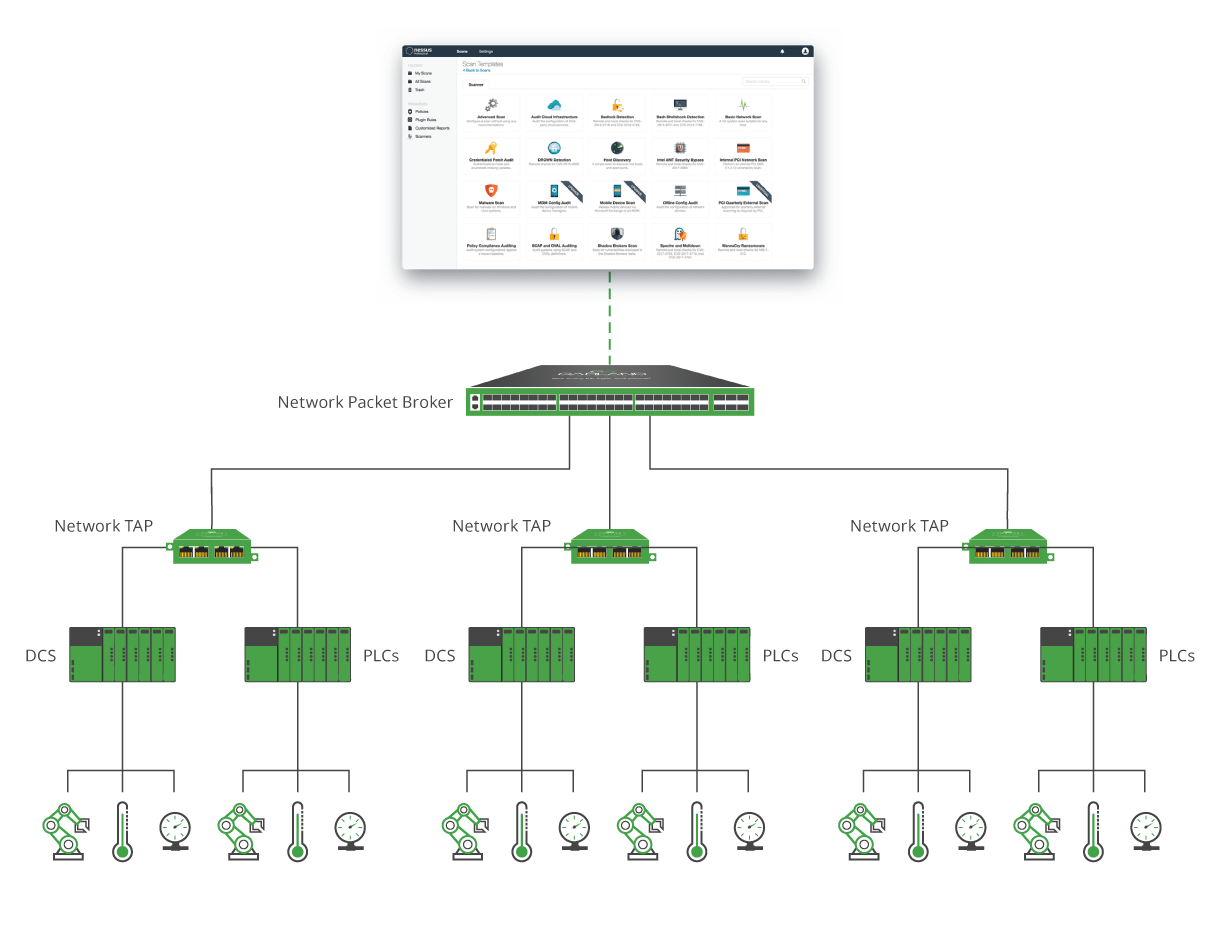
Eliminating Blind Spots And Continuous Monitoring Across Critical Infrastructures
HOW IT WORKS
1. Intelligent network visibility starts by using physical and virtual TAPs to copy full-duplex traffic from any IT and/or OT network at each layer and site. Garland’s network TAPs help overcome limitations that occur when SPAN/Mirror ports are used, providing complete network visibility from each DCS, PLC or segment that needs monitoring.
2. To optimize the network traffic, the tapped data is delivered to a Garland PacketMAX Packet Broker for aggregation, load-balancing and any necessary filtering.
3. Once aggregated, the packet-level data feed Tenable OT Security for efficient and continuous monitoring.
Integration Benefits
By capturing and sending packet traffic from anywhere in the network from the Garland visibility products, the Tenable OT Security can gain full visibility for deep packet inspection and vulnerability assessment. Tenable OT Security executes an intuitive vulnerability assessment for less time and effort to assess, prioritize, and remediate issues. The solution provides compliance and configured templates to audit against CIS benchmark and best practices. The scalable modular solution allows for future growth with port efficiency and zero overall cost per-port.
IT Ops and Sec Ops Benefits
• Live discovery of any digital asset across any computing environment.
• Continuous visibility into where an asset is secure or exposed, and to what extent.
• Prioritization of remediation based on business risk.
• Measurement of cyber exposure as a key risk metric for strategic decision support.
• Complete network visibility bypassing all live wire data ensuring no dropped packets for out-of-band tools.
• Over 450 out of the box, pre-configured templates are included for a range of IT and mobile assets to help quickly
understand where there are vulnerabilities.
• Reliable traffic aggregation, load balancing, and filtering – full control over traffic behavior and flexibility for aggregation
and regeneration.
About Tenable
Tenable® is the Exposure Management company. Approximately 43,000 organizations around the globe rely on Tenable to understand and reduce cyber risk. As the creator of OT Security, Tenable extended its expertise in vulnerabilities to deliver the world’s first platform to see and secure any digital asset on any computing platform. Tenable customers include approximately 60 percent of the Fortune 500, approximately 40 percent of the Global 2000, and large government agencies. Learn more at www.tenable.com

Garland Technology and Tenable provide a continuous visibility and monitoring solution for IT environments. Looking to add this solution, but not sure where to start? Join us for a brief network Design-IT Demo or consultation. No obligation - it’s what we love to do.
