Garland EdgeLens Solution
Garland’s EdgeLens series is an advanced bypass TAP with built-in packet broker functionality that centralizes network traffic, making network tools more efficient by sharing network traffic with monitoring and security tools. EdgeLens provides visibility for a hybrid configuration of an active, inline network device and out-of-band tools, such as LiveAction. EdgeLens provides identical network traffic streams through the active inline device and to the capture engine of LiveAction LiveWire or LiveCapture. The benefits of both devices seeing the same traffic are:
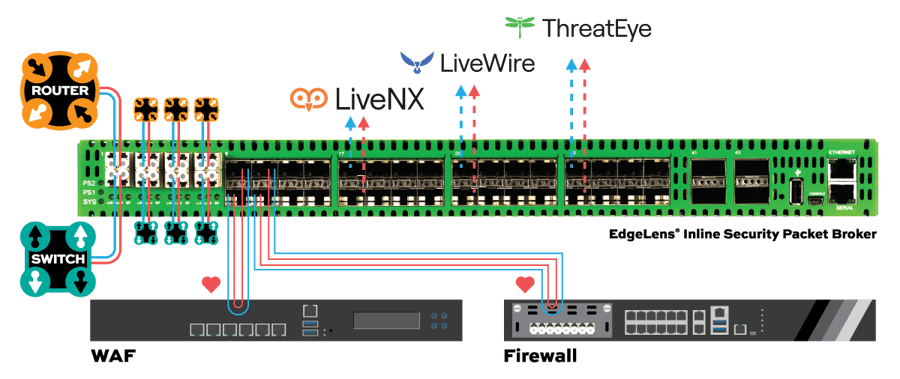
• Correlated data for real-time monitoring and root cause analysis using network packets.
• Historical look back and playback of the network traffic.
• Validating and updating network policy changes and spotting anomalies.
• Network data recording for compliance and security forensics.
• Root cause analysis for application and network related problems.
TAP -> TOOL
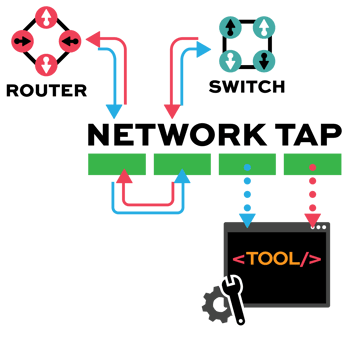
Network TAP Benefits
- Provide complete packet visibility with full-duplex copies of network traffic.
- Ensure no dropped packets while passing physical errors and support jumbo frames without delay or altering the data.
- Support speeds from 10/100M, 1G, 10G, 40G, 100G, and 400G are available in single-mode and multi-mode fiber or copper ethernet.
- Available in Tap ‘Breakout,’ aggregation, regeneration, bypass, and advanced filtering.
- Passive or failsafe – Does not affect the network.
- No IP address or MAC address, and cannot be hacked.

How It Works
1. Deployed at strategic locations at the remote sites, Garland’s Copper and Fiber Network TAPs provide a complete copy of the network traffic.
2. Tapped network feeds plus SPAN/Mirror feeds are then aggregated by a Garland Packet Broker before being encapsulated via GRE or VXLAN.
3. Powered by Blue Ridge’s patented technology DPF (Data Privacy Facility), CyberCloak™ isolates, conceals, encrypts, and authenticates network communications, securing traffic end to end, in a zero-trust context.
4. Within the data center infrastructure, traffic flows back into a separate Packet Broker to send onwards to various security and monitoring tools.
5. The BorderGuard is the root of trust and the secure connection controller for all data and management plane communications. It serves as the backbone of the CyberCloak solution. It can handle multiple CyberCloak Clients, RemoteLink, and EdgeGuard connections.
6. A RemoteLink is a plug-and-play client device that creates secure enclaves. Using crypto-ignition tokens, A RemoteLink securely connects local devices or network segments over any communication medium to the rest of the enterprise via connection to one or more BorderGuards.
Key Benefits
Comprehensive network security and asset management
Cloaking of critical infrastructure OT systems within CyberCloak-enabled Zero Trust secure enclaves.
Encrypted secure communications only from authorized devices and users within secure enclaves.
Reduces network complexity. Integrates seamlessly with existing network infrastructure.
Agnostic to transport and communications protocol, 100% packet visibility across the OT/ICS network.
Data Diode functionality built into Network TAPs guarantees unidirectional traffic.
Easy to deploy, manage, operate, rapid scalability and compatibility, cost effective and efficient operations.
Full PDF Solution Brief
Download our comprehensive solution documentation
About Blue Ridge Networks
Preemptive Protection for Your Critical Assets, Data, & Operations
Blue Ridge Networks, Inc., (BRN) is a recognized leader in providing advanced zero-trust segmentation and secure access cybersecurity solutions that dramatically reduce the cyberattack surface and vulnerabilities to potential breaches. CyberCloak™ utilizes BRN patented methodologies to isolate, conceal, encrypt, and authenticate network communications in a zero-trust context. Solutions built and deployed on the CyberCloak™ foundation have consistently proven to be the most resilient, compatible, least disruptive, and cost effective to deliver high assurance cybersecurity protection. For more information on Blue Ridge’s technology, visit BlueRidgeNetworks.com.
Schedule Your Network Solution Call Today
- How It Works
- Bypass TAP Benefits
- Full PDF Solution Brief
- How It Works
- How It Works
- How It Works
Bypass manages the availability of inline tools, preventing a single point of failure in the network by “bypassing” the device in the event it fails or needs to be updated. Reducing network downtime. Bypass is unique to the other TAP modes, as it is an inline use case not out-of-band.
• Keep up with Federal security mandates
• Expedited problem resolution
• Ability to pilot or deploy need security tools
• No maintenance windows
• Simple configuration ensures a quick set-up
• Zero subscription fees so O&M expenses don’t increase
■SOLUTION EDGESAFETM BYPASS TAP
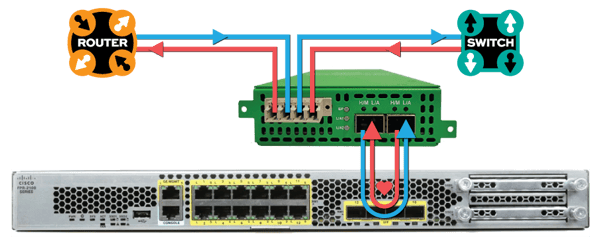
• Install a Garland Technology Bypass TAP between Cisco Firepower and the network
• Bypass TAP manages the availability of Firepower at any time without having to take down the network
• Bypass TAP continuously checks the health of Firepower with heartbeat packets and the Bypass TAP will bypass Firepower to keep the network up-and-running in the event Firepower becomes unavailable
| PROBLEM 1 PORT FAILURE | ||
|
■WITHOUT TAP • The network |
|
■WITH TAP • Uptime • Tool is bypassed while it is being updated |
| PROBLEM 1 PORT FAILURE | ||
|
■WITHOUT TAP • The network |

|
■WITH TAP • Uptime • Tool is bypassed while it is being replaced |





