
To put it bluntly, organizational IT and security teams have never been in a more difficult position than they are today. The non-stop need for businesses to adopt any-and-all devices has significantly expanded the size of enterprise networks — widening the attack surface for cyber actors to exploit while creating subsequent IT visibility challenges.
Endpoint detection and response (EDR) is typically the first go-to solution for monitoring activity and halting an attack at the endpoint. However, it usually only accounts for specific devices, such as computers or laptops. Other network components, such as printers, network routers, and even some mobile phones, remain vulnerable despite providing excellent targets to penetrate a network.
To make matters worse, resource scarcity has only added more roadblocks. A shortage of qualified cybersecurity and network engineering candidates to fill critical positions has caused employees currently in those roles to exceed capacity and experience significant burnout. At the same time, security leaders are walking tightropes trying to navigate all the products on the market, many of which are only focused on incident prevention while on a slim budget.
In the end, understand that network intrusion is nearly inevitable, especially with today's sophisticated attack vectors. Therefore, organizations must adopt a robust security strategy that focuses on recognizing a breach and mitigating its impact in addition to trying to prevent attacks. Security and network teams must also deploy those controls on all areas of the network, not just on the endpoints.
So what's the best way to manage network traffic and obtain comprehensive visibility?
Introducing the SOC visibility triad
Developed in 2015 by Gartner, the SOC visibility triad offers the framework for network observability across an enterprise. It operates on the assumption that, with enough time, attackers will eventually breach a network perimeter. This puts the focus on threat identification and incident resolution to stop an attacker before they can steal sensitive data, shut down a system, or accomplish other objectives.
Before Gartner created the triad, security operation centers (SOC) mainly relied on activity logging through security information and event management (SIEM) tools and antivirus software to discover anomalies and potential incidents. Of course, this left tons of blindspots and process gaps. Only the users and endpoints were accounted for, and there was no automated, 24/7 threat solution to address an attack once identified.
This pushed basic endpoint detection tools, like antivirus, to transition into EDR and created the need for extended threat detection on other network components, like printers and routers. From there, the official triad of visibility elements was formed — adding network detection and response (NDR) as the third piece to go along with SIEM and EDR solutions.
The focus on the network visibility fabric
Many experts believe the triad could evolve into a visibility quad and incorporate the separate need for application detection and response solutions, mainly because of the massive spike in cloud software adoption. For now, however, the NDR component will adhere to those requirements.
To serve their function correctly, SOC teams need to deploy a strategy that fully considers the enterprise's network while finding ways to obtain non-stop access to network packets. By default, they'll need the relevant knowledge on network management and monitoring technology — something that's, unfortunately, often left out of today's security training.
Deploying NDR will remove departmental silos between SOC and network engineering teams through shared access to network data. Data packet copies should be collected and stored from EVERY network location to ensure complete IT visibility with no blind spots.
Obtaining comprehensive visibility using network TAPs
There are two main routes for getting copies of network packets from NDR tools. One is to reconfigure the switches to mirror network data to a spare port, also called a switched port analyzer (SPAN). The other and more effective method is installing network test access points (TAPs) in areas that need monitoring. Why?
TAPs are reliable and 100% guaranteed to deliver packet copies to the monitor port. They also are a far more secure and cost-friendly option compared to SPAN. Plus, since it acts as a broker independent of the switches and routers, any TAP operational failure will not impact other parts of the network.
Alternatively, SPAN often gets quickly overloaded with packets to the point where data unexpectedly gets dropped. SPAN also alters the timing of network packets and will not withstand any packet errors, which is problematic if the errored packets are an indication of a breach.
At the same time, SPAN requires a lot of setup and maintenance costs to manage. Plus, since SPAN is directly part of the network, any system-wide shutdown or network misconfiguration will cause the SPAN port to miss data.
Seeing the benefits and outcomes of network packet brokers
Whether physical or virtual, network TAPs are a core component to maintaining reliable and wholesome visibility. However, complex networks that require multiple monitoring feeds for the NDR tools could demand an additional linking step. This is where network packet brokers help take TAP, SPAN, and virtual tunnel feeds and aggregate the data into one location.
In addition to collecting and centralizing information, packet brokers are useful for other functions, such as data filtering, tagging, timestamping, slicing, and masking. They can also transport data to remote locations and load balance traffic into various NDR tools across numerous interfaces as needed.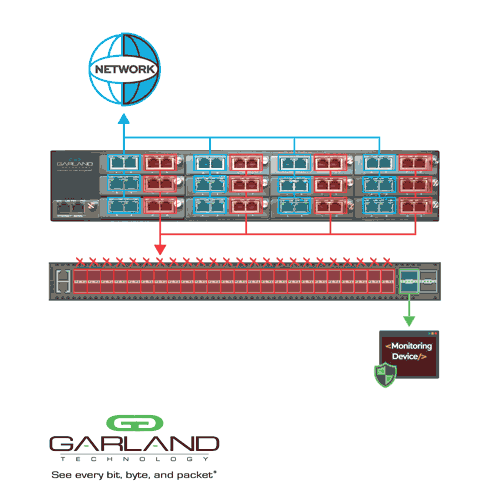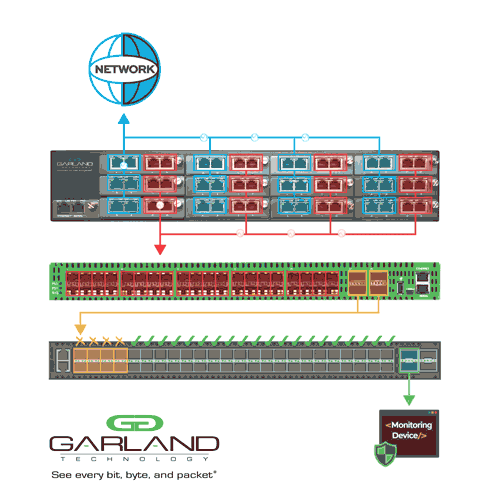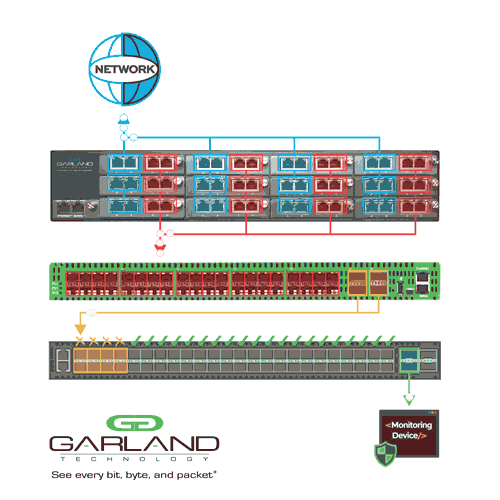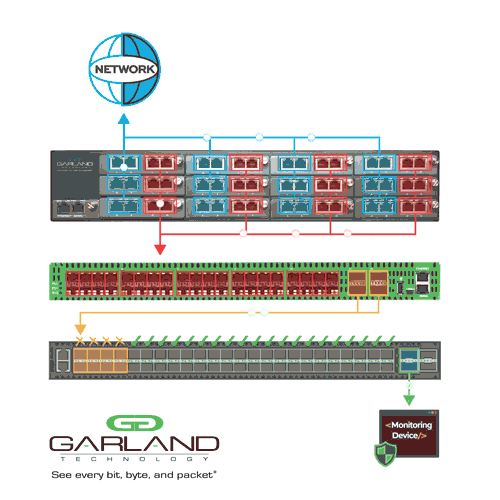
This network visibility fabric has benefits that expand beyond just cybersecurity. Completing resource-intensive functions within an NDR solution, such as data deduplication while maintaining solid network speeds, can also be achieved using a high-quality packet broker. The TAP flexibility even enables IT personnel to accommodate changes in a network infrastructure more efficiently.
Finally, network TAPs reduce operational costs since there are no configuration overhead costs involved and a much longer mean time between failures (MTBF) — helping lessen the negative impact of the labor shortage. The ultimate result of using packet brokers for network visibility is a more efficient system for network threat detection, system maintenance, and NDR configuration.
Combine TAPs into the SOC triad of visibility with Garland Technology
Looking to utilize network TAPs in your SOC triad and visibility strategy but need help figuring out where to start? Join us for a brief network design-IT consultation and demo. No obligation - it's what we love to do!
