Garland Technology & Forescout: Pioneering Complete Network Visibility and Security
Key topics covered:
- The importance of complete network visibility
- How Garland and Forescout's joint solution addresses security challenges
- Real-world use cases and customer success stories
- Future developments in network security and visibility
Watch the full interview to gain in-depth insights into how Garland Technology and Forescout are shaping the future of network visibility and security.
Forescout and Garland Technology Benefits
- Efficiently manage the security posture and lifecycle of all connected devices
- Combined passive and active detection to identify assets, location, cyber posture and detect anomalies
- Reduce risk with continuous identification and mitigation of all cyber assets
- Accelerate the remediation of non-compliant and compromised devices with automated policy-driven workflows
- Easy configuration and deployment improves reliability and reduces operational costs
- 100% network visibility with full-duplex copies of network traffic
- Provide secure visibility with data diode functionality without adding latency
- Illuminate blind spots that periodic scanning tools miss with on-connect device inventory and continuous monitoring
- Increasing network defense and operational productivity with automated context-aware policy-driven actions
Garland EdgeLens Solution
Garland’s EdgeLens series is an advanced bypass TAP with built-in packet broker functionality that centralizes network traffic, making network tools more efficient by sharing network traffic with monitoring and security tools. EdgeLens provides visibility for a hybrid configuration of an active, inline network device and out-of-band tools, such as LiveAction. EdgeLens provides identical network traffic streams through the active inline device and to the capture engine of LiveAction LiveWire or LiveCapture. The benefits of both devices seeing the same traffic are:
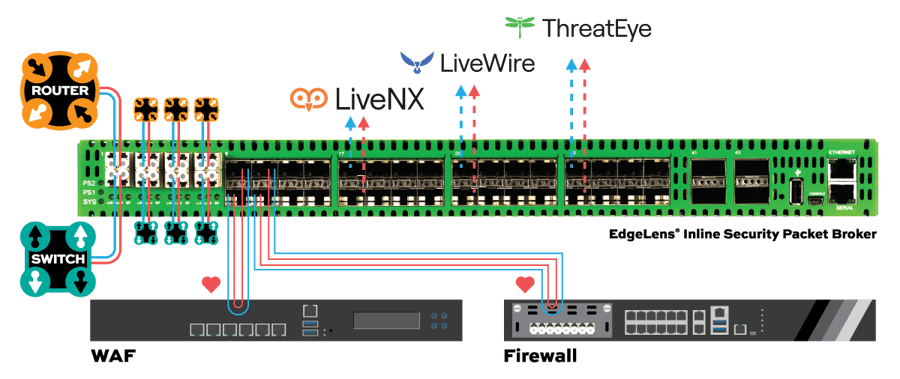
• Correlated data for real-time monitoring and root cause analysis using network packets.
• Historical look back and playback of the network traffic.
• Validating and updating network policy changes and spotting anomalies.
• Network data recording for compliance and security forensics.
• Root cause analysis for application and network related problems.
TAP -> TOOL
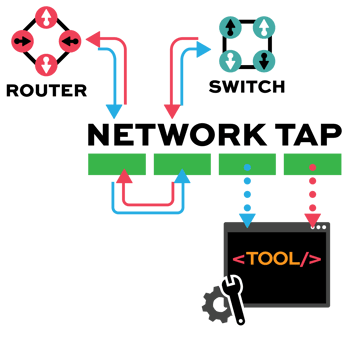
Network TAP Benefits
- Provide complete packet visibility with full-duplex copies of network traffic.
- Ensure no dropped packets while passing physical errors and support jumbo frames without delay or altering the data.
- Support speeds from 10/100M, 1G, 10G, 40G, 100G, and 400G are available in single-mode and multi-mode fiber or copper ethernet.
- Available in Tap ‘Breakout,’ aggregation, regeneration, bypass, and advanced filtering.
- Passive or failsafe – Does not affect the network.
- No IP address or MAC address, and cannot be hacked.
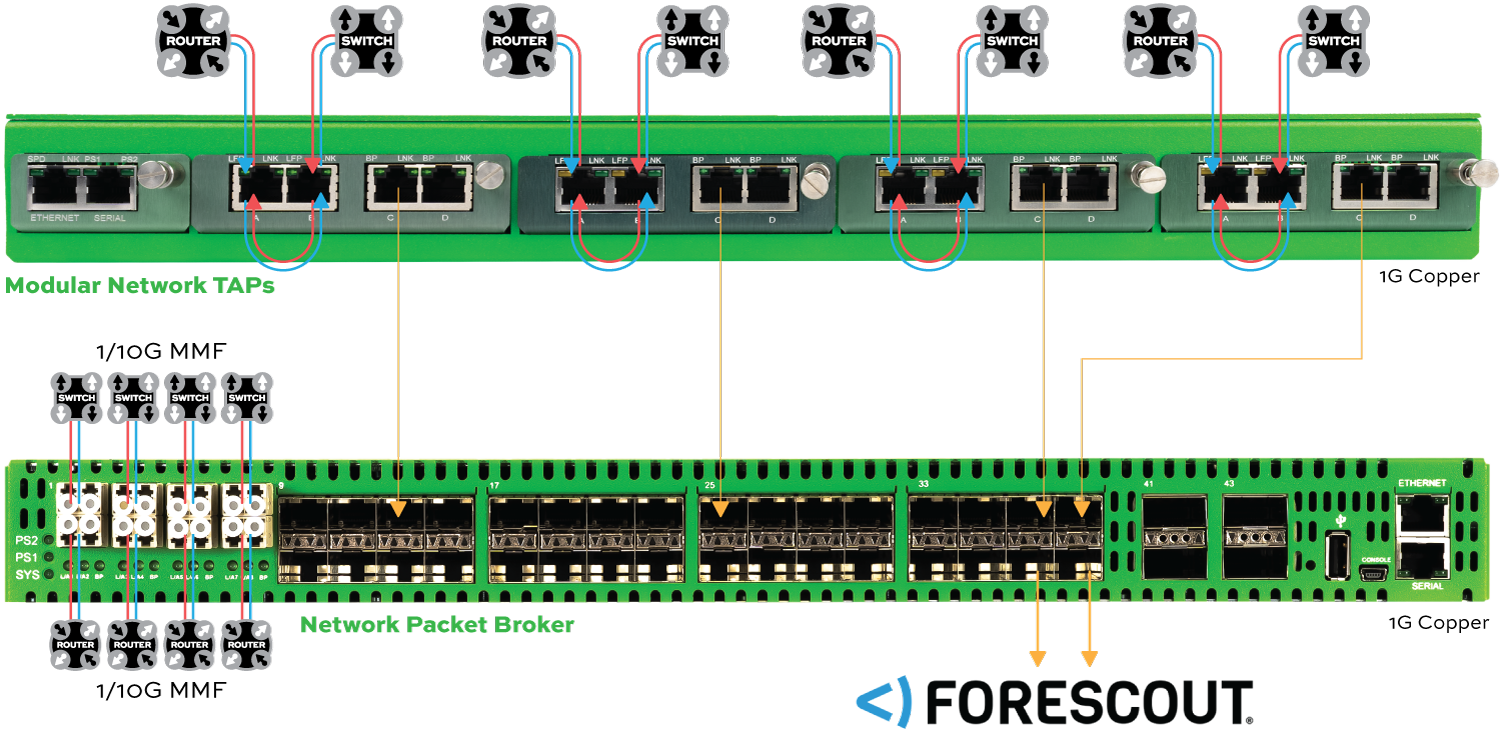
How it Works
- Intelligent network visibility starts with using Garland Technology Network TAPs to copy full duplex traffic from the IT and/or OT network. Garland’s TAPs help overcome limitations that occur when SPAN/mirror ports are used, while providing data diode functionality to guarantee unidirectional traffic flow.
- To optimize the network, the tapped traffic is delivered to a Garland Network Packet Broker for aggregation, load balancing and filtering.
- The Forescout Platform processes the groomed data in real-time to automate the discovery, assessment and governance of all OT, IoT and IT assets. Forescout uses this data to provide network security, risk and exposure management, and extended detection and response.
- Forescout’s continuously expanding Industrial Threat Library and ICS-specific Indicator of Compromise (IOC) and Vulnerabilities (CVE) database works to protect asset owners from advanced cyberattacks, network misconfigurations and operational errors.

Forescout is the only automated cybersecurity vendor with a single platform for continuously identifying and mitigating risk across all managed and unmanaged assets – IT, IoT, IoMT and OT – from campus to data center to edge. For more than 20 years, we have delivered cybersecurity innovations that protect many of the world’s largest, most trusted organizations in finance, government, healthcare, manufacturing and other industries. www.forescout.com
- How It Works
- Bypass TAP Benefits
- Full PDF Solution Brief
- How It Works
- How It Works
- How It Works
Bypass manages the availability of inline tools, preventing a single point of failure in the network by “bypassing” the device in the event it fails or needs to be updated. Reducing network downtime. Bypass is unique to the other TAP modes, as it is an inline use case not out-of-band.
• Keep up with Federal security mandates
• Expedited problem resolution
• Ability to pilot or deploy need security tools
• No maintenance windows
• Simple configuration ensures a quick set-up
• Zero subscription fees so O&M expenses don’t increase
■SOLUTION EDGESAFETM BYPASS TAP
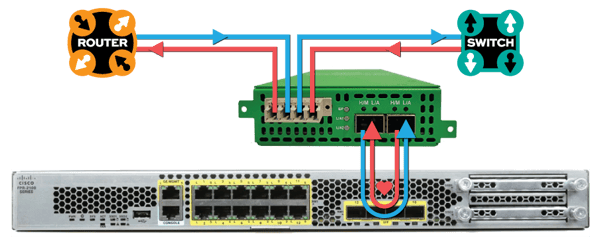
• Install a Garland Technology Bypass TAP between Cisco Firepower and the network
• Bypass TAP manages the availability of Firepower at any time without having to take down the network
• Bypass TAP continuously checks the health of Firepower with heartbeat packets and the Bypass TAP will bypass Firepower to keep the network up-and-running in the event Firepower becomes unavailable
| PROBLEM 1 PORT FAILURE | ||
|
■WITHOUT TAP • The network |
|
■WITH TAP • Uptime • Tool is bypassed while it is being updated |
| PROBLEM 1 PORT FAILURE | ||
|
■WITHOUT TAP • The network |

|
■WITH TAP • Uptime • Tool is bypassed while it is being replaced |





