Industrial Defender Platform Key Features
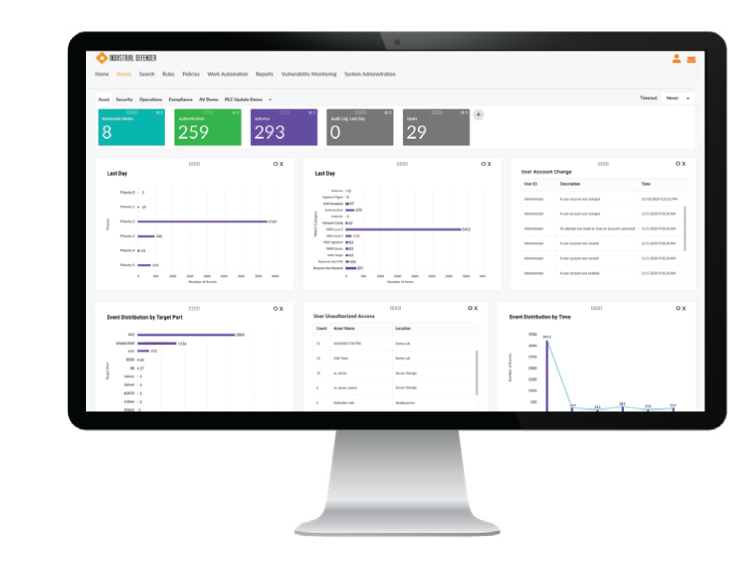
Leading OT asset management solution providing the deepest, most comprehensive OT asset information for security and compliance. Offers deep asset inventory details, including software versions, vulnerabilities, patches, firewall rules, and PLC key switch positions. It serves as a centralized solution for OT asset management, change and configuration management, vulnerability management, and policy compliance.
Combining Industrial Defender’s platform with Garland Technology’s Network TAPs enhances situational awareness of the OT environment.
Garland Technology TAPs Key Features

Provide the deepest levels of visibility into the packet level data, with no impact to the live network. By ensuring 100% of network traffic is copied and transmitted to monitoring tools in real time, TAPs improve uptime and guarantee comprehensive packet visibility for security solutions. Garland TAPs are independent and cannot be hacked as they do not have an IP address or a MAC address, making them invisible to the network.
Garland EdgeLens Solution
Garland’s EdgeLens series is an advanced bypass TAP with built-in packet broker functionality that centralizes network traffic, making network tools more efficient by sharing network traffic with monitoring and security tools. EdgeLens provides visibility for a hybrid configuration of an active, inline network device and out-of-band tools, such as LiveAction. EdgeLens provides identical network traffic streams through the active inline device and to the capture engine of LiveAction LiveWire or LiveCapture. The benefits of both devices seeing the same traffic are:
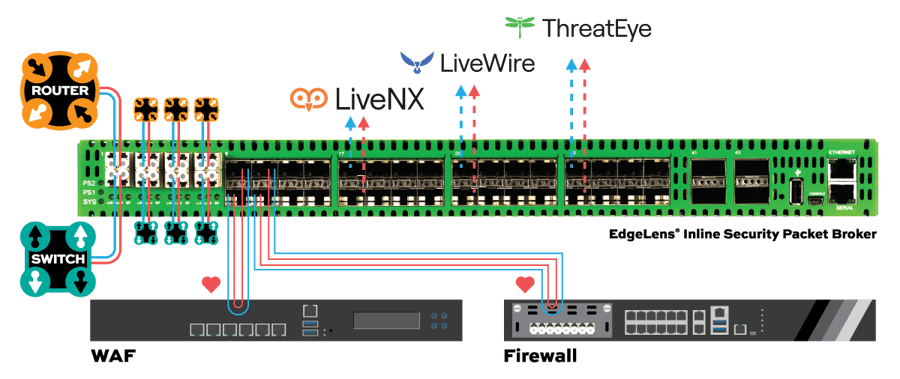
• Correlated data for real-time monitoring and root cause analysis using network packets.
• Historical look back and playback of the network traffic.
• Validating and updating network policy changes and spotting anomalies.
• Network data recording for compliance and security forensics.
• Root cause analysis for application and network related problems.
TAP -> TOOL
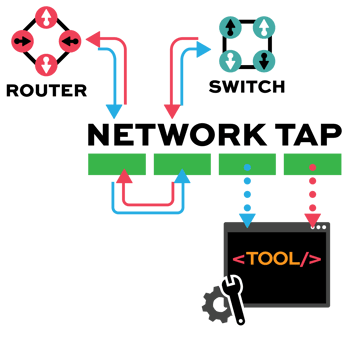
Network TAP Benefits
- Provide complete packet visibility with full-duplex copies of network traffic.
- Ensure no dropped packets while passing physical errors and support jumbo frames without delay or altering the data.
- Support speeds from 10/100M, 1G, 10G, 40G, 100G, and 400G are available in single-mode and multi-mode fiber or copper ethernet.
- Available in Tap ‘Breakout,’ aggregation, regeneration, bypass, and advanced filtering.
- Passive or failsafe – Does not affect the network.
- No IP address or MAC address, and cannot be hacked.
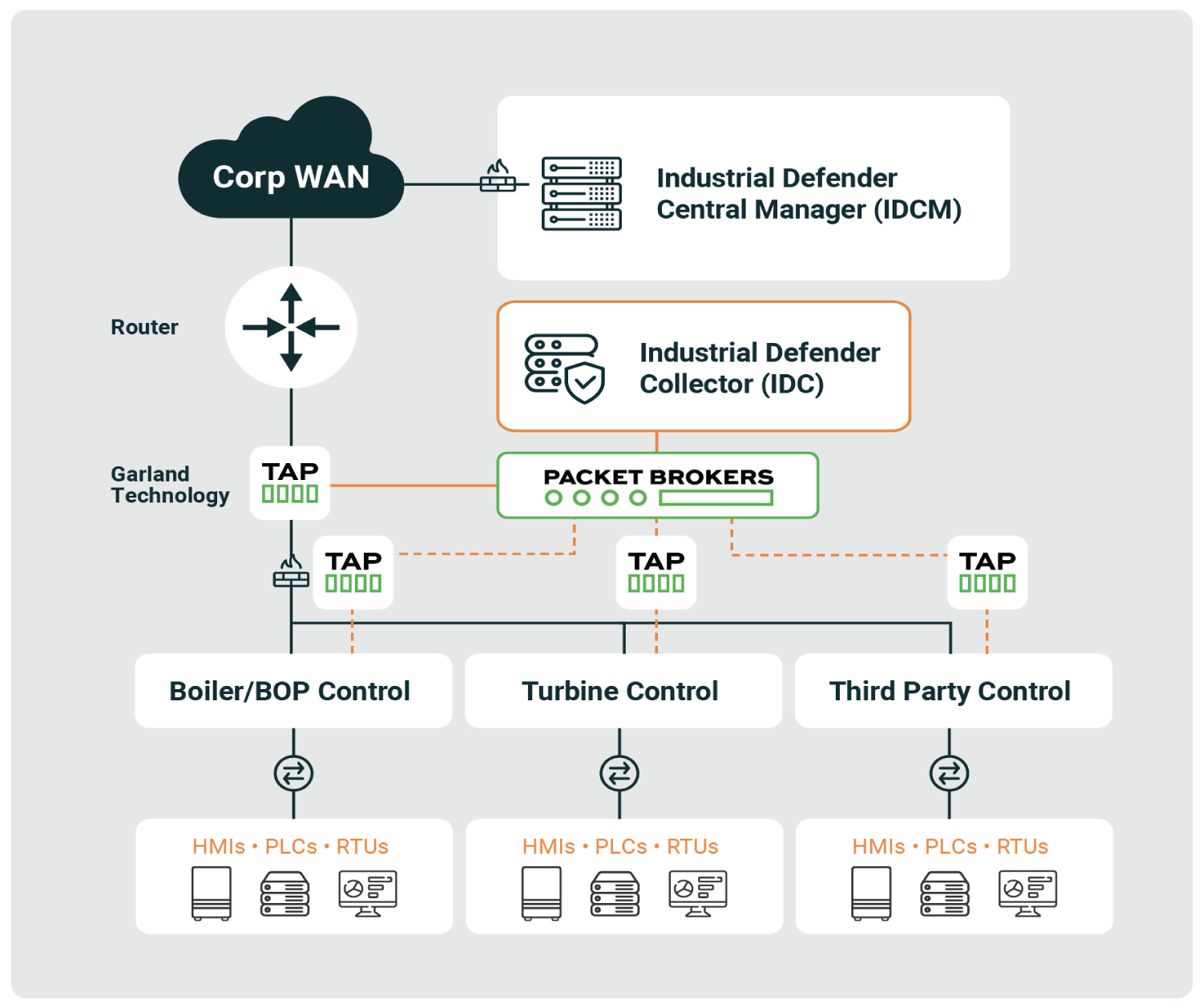
How it Works
Garland Network TAPs: Analyze data from OT networks by mirroring network traffic. The tapped traffic can then feed into the Network Packet Broker, which combines, filters, and load balances the tapped traffic at scale into the Industrial Defender IDC data collector and/or management system.
Industrial Defender Collector (IDC): Analyzes the traffic, inventories all OT assets, and identifies vulnerable devices, cyber threats, and operational anomalies on your network.
Industrial Defender Central Manager (IDCM): Industrial Defender centralizes data with other OT asset management and configuration management data collected across the environment, making it reportable and actionable.
Together, Industrial Defender and Garland Technology deliver a robust, integrated OT asset management and security monitoring solution, allowing for enhanced compliance and operational resilience for industrial organizations.
Benefits Summary
- Comprehensive OT Asset Data: Deliver the most detailed OT asset data needed to protect industrial operations and prove compliance.
- Non-Intrusive Network Monitoring: Gain a detailed view of all the traffic traversing a network, including communications between OT assets. This comprehensive visibility helps in identifying and monitoring all assets connected to the network.
- Anomaly Detection: Identify anomalies and irregularities in network traffic, which could indicate compromised devices or malicious activities. Early detection of such issues is critical in preventing significant security incidents.
- Configuration and Change Management: Maintain the integrity of all configurable elements of hardware or software, including capturing a baseline build or settings for any specific asset, detecting new configurations, and managing the deployment of new builds or configurations.
- Vulnerability Management: Proactively identify and mitigate vulnerabilities to minimize the window of opportunity for attackers, and make progress with prioritization and tracking of your patching and mitigation efforts as part of your compliance workflow.
- Optimize Tool Performance: Improve and air gap tool performance by providing complete unidirectional packet visibility while optimizing and aggregating traffic.
- Packet Visibility for Legacy Networks: Provide OT security tools packet visibility for legacy networks with unmanaged switches that cannot utilize SPAN.
- Automate Compliance Efforts: With built-in policy management and reporting templates, automate compliance efforts for standards including NERC CIP, IEC 62443, TSA SD, NIS2, AESCSF, CMMC, and more.

Industrial Defender protects the world’s critical infrastructure from cyberattacks. As the leader in OT cybersecurity innovation, the company’s scalable platform is used by the largest organizations in the world to empower security stakeholders with actionable data about their OT and IIoT infrastructure, enabling them to make informed risk management decisions. Learn more at IndustrialDefender.com.
- How It Works
- Bypass TAP Benefits
- Full PDF Solution Brief
- How It Works
- How It Works
- How It Works
Bypass manages the availability of inline tools, preventing a single point of failure in the network by “bypassing” the device in the event it fails or needs to be updated. Reducing network downtime. Bypass is unique to the other TAP modes, as it is an inline use case not out-of-band.
• Keep up with Federal security mandates
• Expedited problem resolution
• Ability to pilot or deploy need security tools
• No maintenance windows
• Simple configuration ensures a quick set-up
• Zero subscription fees so O&M expenses don’t increase
■SOLUTION EDGESAFETM BYPASS TAP
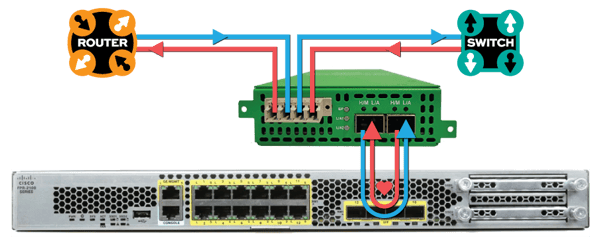
• Install a Garland Technology Bypass TAP between Cisco Firepower and the network
• Bypass TAP manages the availability of Firepower at any time without having to take down the network
• Bypass TAP continuously checks the health of Firepower with heartbeat packets and the Bypass TAP will bypass Firepower to keep the network up-and-running in the event Firepower becomes unavailable
| PROBLEM 1 PORT FAILURE | ||
|
■WITHOUT TAP • The network |
|
■WITH TAP • Uptime • Tool is bypassed while it is being updated |
| PROBLEM 1 PORT FAILURE | ||
|
■WITHOUT TAP • The network |

|
■WITH TAP • Uptime • Tool is bypassed while it is being replaced |






