Improve Tool Efficiency
IT Security Solutions
Challenge: How to ensure optimal tool performance?
Network monitoring and security tools need packet data to properly analyze the task at hand. Teams are typically tasked with getting more out of their existing tool investments, which becomes challenging with growing traffic volumes and legacy architecture.
• Network and security tools can themselves be oversubscribed
• Traffic growth outpaces existing tool capacity leading to reduced throughput and effectiveness
To get the data to these tools, your options are spanning a port from your switch or utilizing a network TAP. At the same time, it is imperative to not negatively affect the performance of these tools or the connected network.
SPAN ports generally do not affect the performance of the switch, though this varies with different SPAN port features / vendors, but can have an impact on your data and the tools and they are feeding, including:
• Designed for low-throughput situations, SPAN will drop packets if heavily utilized or oversubscribed.
• Can duplicate packets if multiple VLANs are used.
• Can change the timing of the frame interactions, altering response times.
• Will not pass corrupt packets or connection errors
Solution
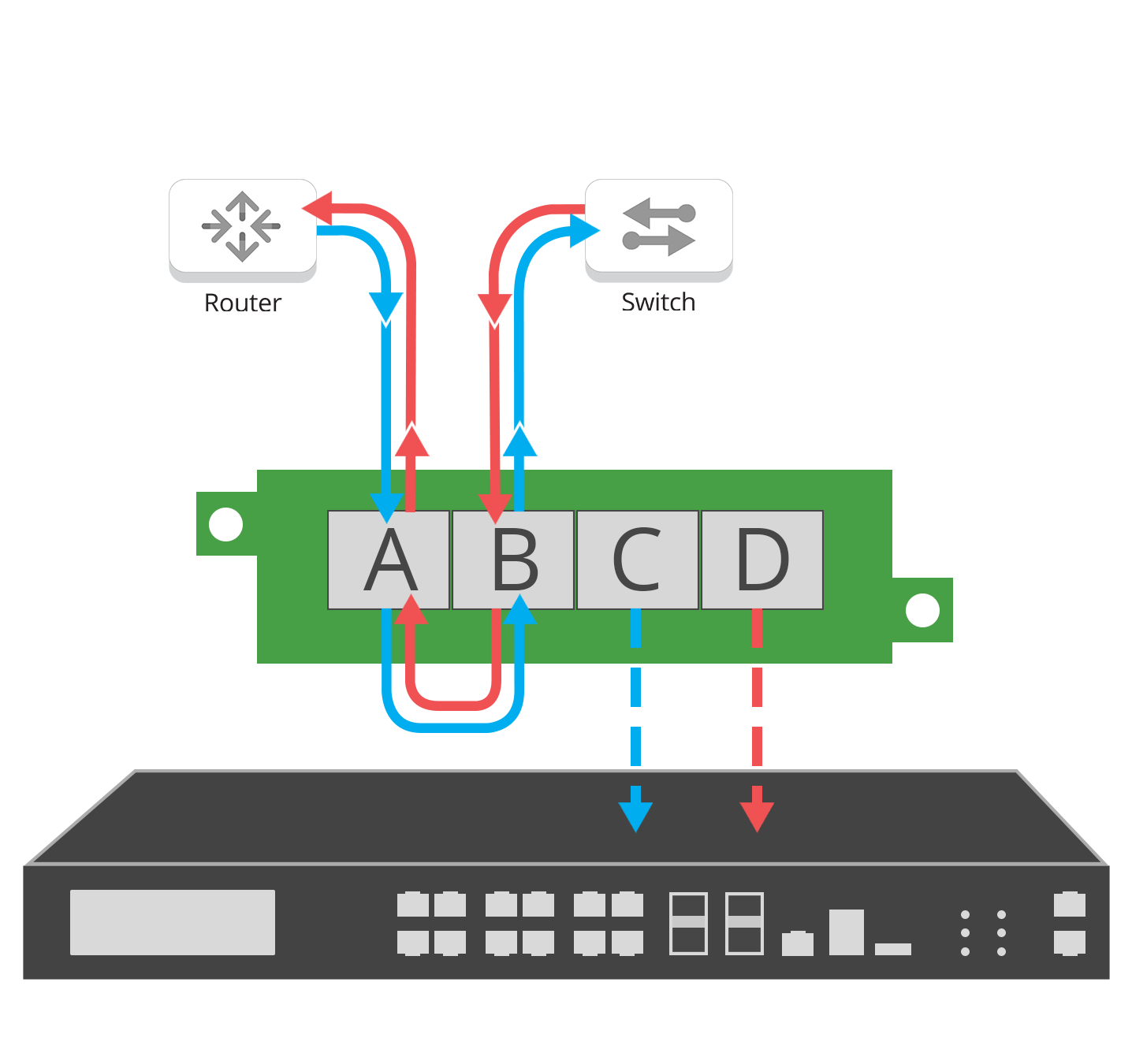
Network TAPs guarantee tools complete packet data
Network TAPs are purpose-built to pass 100% full duplex traffic, passing errors, without dropping packets or impacting the performance of the network, enhancing the monitoring and security tools they feed.
Network TAPs eliminate blindspots, one key issue monitoring tools face. But TAPs also enhance tool performance by ensuring no dropped packets if oversubscribed and no duplicate packets or altered frames. Network TAPs provide 100% full duplex copies of the traffic you are analyzing. Better data provides better tool performance and added value.
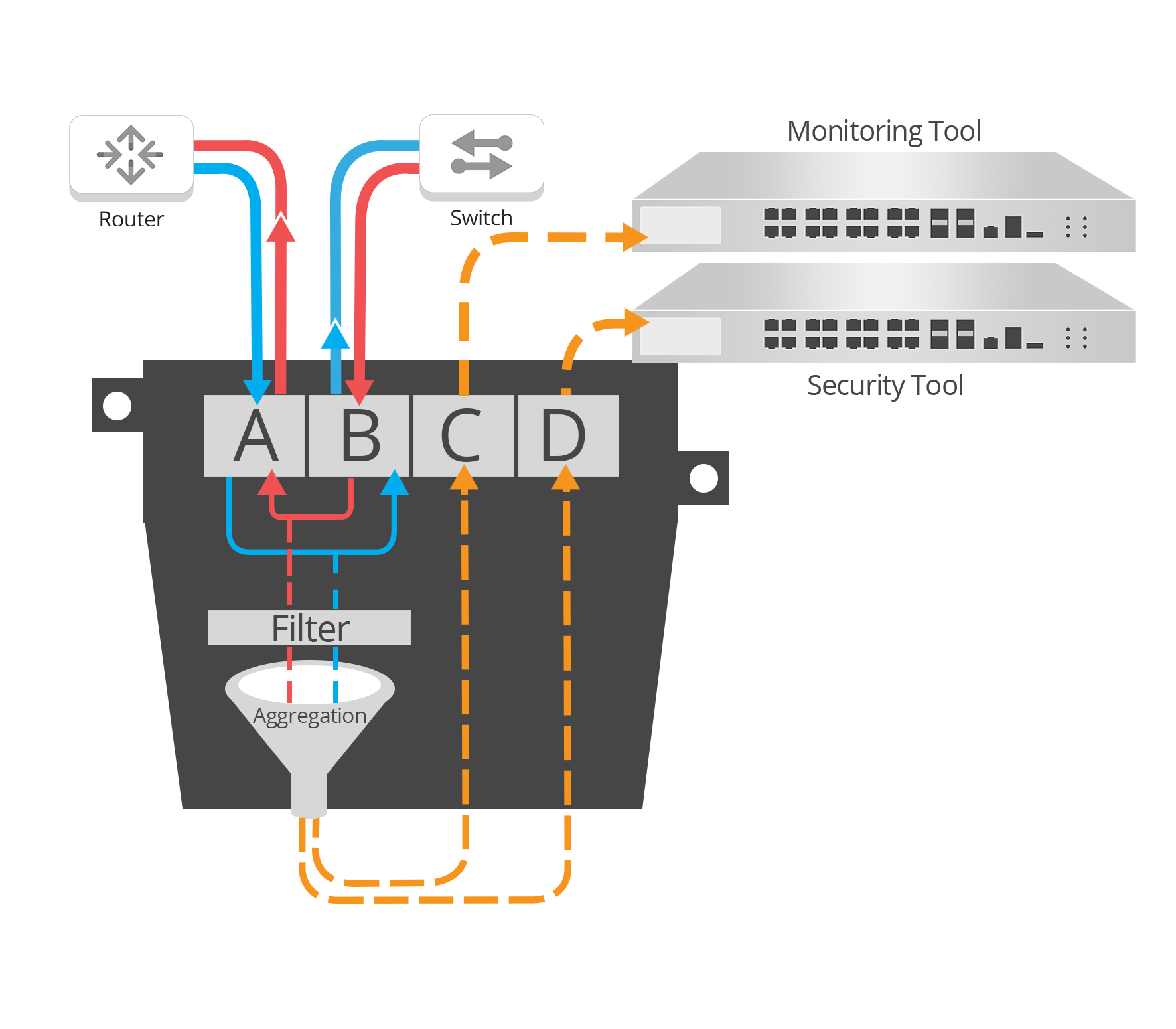
Using data filtering to improve tool efficiency
With the growth in network traffic, analyzing this data is not only time consuming but expensive, as it usually includes an extensive number of tools and network segments.
A more cost-effective technique, that can be used in specific scenarios, is to isolate data that needs to be inspected, like VOIP traffic only, or traffic that has a higher risk of being a security threat and focus on analyzing just that data. This unburdens current tools by reducing traffic load, increasing tool effectiveness and performance.
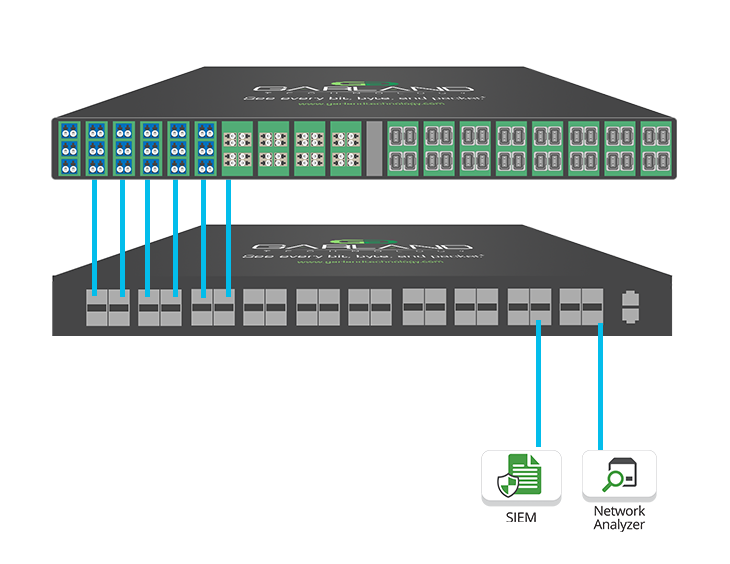
This approach can be accomplished at the TAP level, with Garland’s XtraTAP or with a PacketMAX packet broker that is aggregating many links at once.
• Set utilization alerts for each monitoring port
• Remotely manage alerts to avoid oversubscription
• Set up filtering rules on layers 2, 3 and 4
• Aggregating and load balancing traffic for optimal performance