Security Challenges
Critical infrastructure, manufacturing, healthcare, financial services, and other enterprise environments have evolved from previously air-gapped networks to converged IT and OT environments. The more connected these environments have become, the greater the attack surface and thus, more protection from cyberattacks is vital. Security teams are now realizing they need comprehensive visibility and security across the entire organization, not just the IT network. This has created several challenges that organizations must navigate. Visibility is the foundation of security. That’s why Garland Technology and ORDR have joined forces to provide organizations with unparalleled visibility into all assets connected to the network.
1. IoMT/OT/ICS systems weren’t designed with security in mind and often can’t be discovered via
traditional methods.
2. Tools are often deployed without consultation with the security team.
3. Limited collaboration across an organization’s IT, Security, Networking, and OT teams
negatively impacts security.
4. Cyberattacks against critical infrastructure are on the rise
How the Solution works
Visibility is the foundation of security. That’s why Garland Technology and ORDR have joined forces to provide organizations with unparalleled visibility into all assets connected to the network.
Garland EdgeLens Solution
Garland’s EdgeLens series is an advanced bypass TAP with built-in packet broker functionality that centralizes network traffic, making network tools more efficient by sharing network traffic with monitoring and security tools. EdgeLens provides visibility for a hybrid configuration of an active, inline network device and out-of-band tools, such as LiveAction. EdgeLens provides identical network traffic streams through the active inline device and to the capture engine of LiveAction LiveWire or LiveCapture. The benefits of both devices seeing the same traffic are:
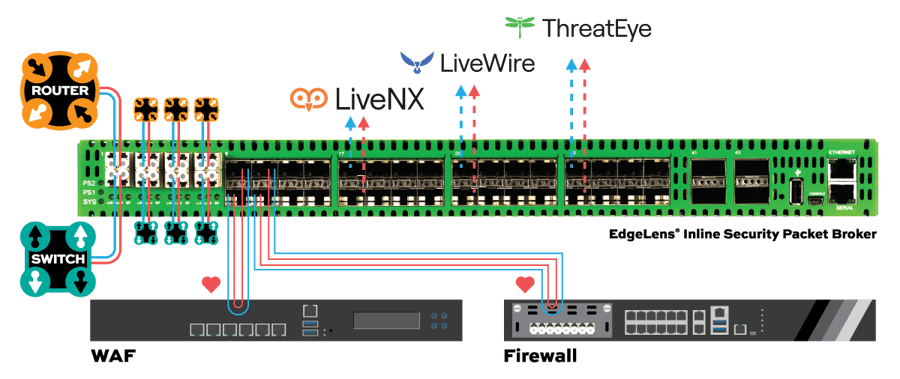
• Correlated data for real-time monitoring and root cause analysis using network packets.
• Historical look back and playback of the network traffic.
• Validating and updating network policy changes and spotting anomalies.
• Network data recording for compliance and security forensics.
• Root cause analysis for application and network related problems.
TAP -> TOOL
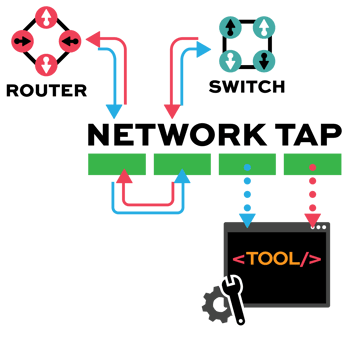
Network TAP Benefits
- Provide complete packet visibility with full-duplex copies of network traffic.
- Ensure no dropped packets while passing physical errors and support jumbo frames without delay or altering the data.
- Support speeds from 10/100M, 1G, 10G, 40G, 100G, and 400G are available in single-mode and multi-mode fiber or copper ethernet.
- Available in Tap ‘Breakout,’ aggregation, regeneration, bypass, and advanced filtering.
- Passive or failsafe – Does not affect the network.
- No IP address or MAC address, and cannot be hacked.

How It Works
1. Garland Technology Network TAPs provide full-duplex copies of both North-South and East-West traffic.
2. Tapped traffic, plus any additional SPAN feeds, is aggregated together and centralized in a convenient location via a Network Packet Broker (Aggregator) before being delivered to ORDR for analysis.
3. With a clear picture of the network, ORDR passively discovers and classifies assets from all categories including IT, IoT, BMS, and IoMT, providing a unified view of the entire environment in real time.
4. ORDR enriches the asset data with in-depth intelligence to pinpoint the most critical risks, eliminating blind spots while reducing alert fatigue and accelerating security response times.
Key Benefits
- Deliver complete visibility into previously undetectable network segments
- Continuous real-time asset inventory
- Risk-based Vulnerability Prioritization and Management
- AI-driven Threat Anomaly Detection and Response
- Automate remediation workflows to reduce risk
- Integration of ORDR sensors simplifies the deployment architecture, support and maintenance for the customer
- The Network TAP’s data diode design provides unidirectional traffic guarantees while eliminating concerns over the security risk of SPAN ports
About ORDR
ORDR is the leader in AI-powered asset risk and exposure management, trusted by top organizations across healthcare, pharmaceuticals, manufacturing, and financial services. With insights from over 100 million asset types, ORDR’s platform empowers security teams to identify their biggest risks and take swift, effective action. From maintaining security hygiene to real-time threat detection and protection using microsegmentation,
ORDR makes action not just possible but automated and simple — bringing ORDR to chaos. ORDR is backed by top investors including Wing Venture Capital, Ten Eleven Ventures, Battery Ventures, Mayo Clinic Ventures, and Kaiser Permanente Ventures. For more information, visit ordr.net and follow ORDR on Twitter and LinkedIn.
Schedule Your Network Solution Call Today
- How It Works
- Bypass TAP Benefits
- Full PDF Solution Brief
- How It Works
- How It Works
- How It Works
Bypass manages the availability of inline tools, preventing a single point of failure in the network by “bypassing” the device in the event it fails or needs to be updated. Reducing network downtime. Bypass is unique to the other TAP modes, as it is an inline use case not out-of-band.
• Keep up with Federal security mandates
• Expedited problem resolution
• Ability to pilot or deploy need security tools
• No maintenance windows
• Simple configuration ensures a quick set-up
• Zero subscription fees so O&M expenses don’t increase
■SOLUTION EDGESAFETM BYPASS TAP
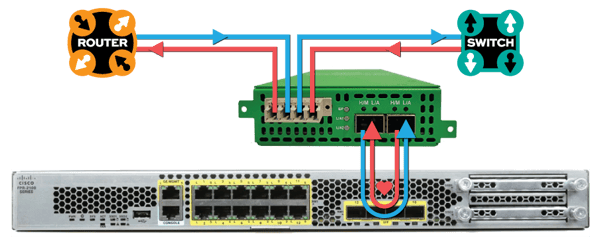
• Install a Garland Technology Bypass TAP between Cisco Firepower and the network
• Bypass TAP manages the availability of Firepower at any time without having to take down the network
• Bypass TAP continuously checks the health of Firepower with heartbeat packets and the Bypass TAP will bypass Firepower to keep the network up-and-running in the event Firepower becomes unavailable
| PROBLEM 1 PORT FAILURE | ||
|
■WITHOUT TAP • The network |
|
■WITH TAP • Uptime • Tool is bypassed while it is being updated |
| PROBLEM 1 PORT FAILURE | ||
|
■WITHOUT TAP • The network |

|
■WITH TAP • Uptime • Tool is bypassed while it is being replaced |





