Security Challenges
Increasing convergence of IT and OT environments has expanded the attack surface and introduced new security risks for critical infrastructure. Older and inherently vulnerable Industrial Control Systems (ICS) that were previously ‘air gapped’ or isolated are becoming increasingly exposed to threats as IT and OT converge. Additionally, as the number of industrial IoT devices has risen dramatically over the past several years, the overall level of visibility for security teams into these assets has decreased, creating easy entry points for attackers.
OT security teams continue to suffer from a growing skills shortage, tight budgets, and are understaffed compared to the IT security teams. Furthermore, as United States and European regulations on OT/ICS tighten, critical infrastructures must find a way to improve their OT security posture with an easy to deploy solution providing visibility across all Purdue Levels.
Key Solution Benefits
• Increased visibility across OT, IT, and IioT to Purdue level 1 where there is lacking existing switching infrastructure.
• Protocol and technology agnostic.
• Illuminates points of IT/OT convergence.
• Reduces risk of misconfigured switch ports.
• Guarantees unidirectional traffic flow with data diode protection.
•Reduce complexity of deployment in distributed networks.
• TAPS do not have an IP or MAC address so are not hackable from a network standpoint.
• Zero hardware subscription fees from Garland Technology.
Garland EdgeLens Solution
Garland’s EdgeLens series is an advanced bypass TAP with built-in packet broker functionality that centralizes network traffic, making network tools more efficient by sharing network traffic with monitoring and security tools. EdgeLens provides visibility for a hybrid configuration of an active, inline network device and out-of-band tools, such as LiveAction. EdgeLens provides identical network traffic streams through the active inline device and to the capture engine of LiveAction LiveWire or LiveCapture. The benefits of both devices seeing the same traffic are:
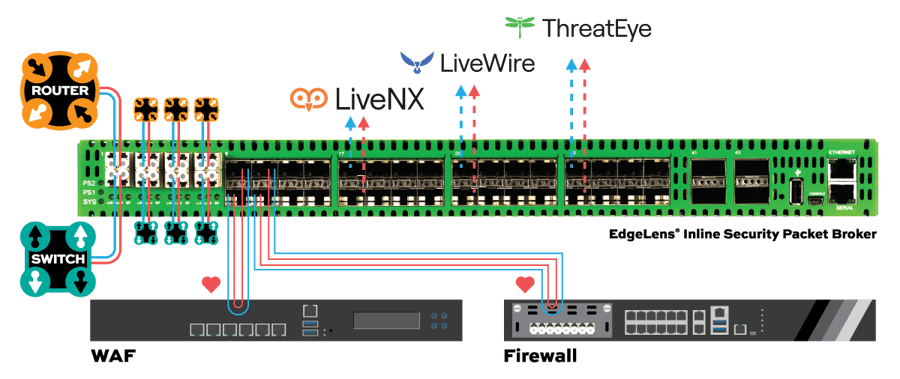
• Correlated data for real-time monitoring and root cause analysis using network packets.
• Historical look back and playback of the network traffic.
• Validating and updating network policy changes and spotting anomalies.
• Network data recording for compliance and security forensics.
• Root cause analysis for application and network related problems.
TAP -> TOOL
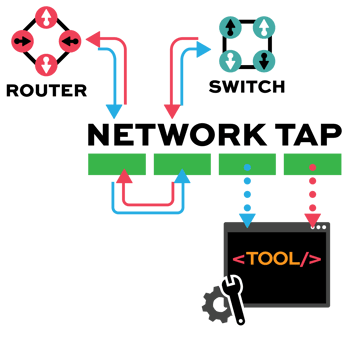
Network TAP Benefits
- Provide complete packet visibility with full-duplex copies of network traffic.
- Ensure no dropped packets while passing physical errors and support jumbo frames without delay or altering the data.
- Support speeds from 10/100M, 1G, 10G, 40G, 100G, and 400G are available in single-mode and multi-mode fiber or copper ethernet.
- Available in Tap ‘Breakout,’ aggregation, regeneration, bypass, and advanced filtering.
- Passive or failsafe – Does not affect the network.
- No IP address or MAC address, and cannot be hacked.
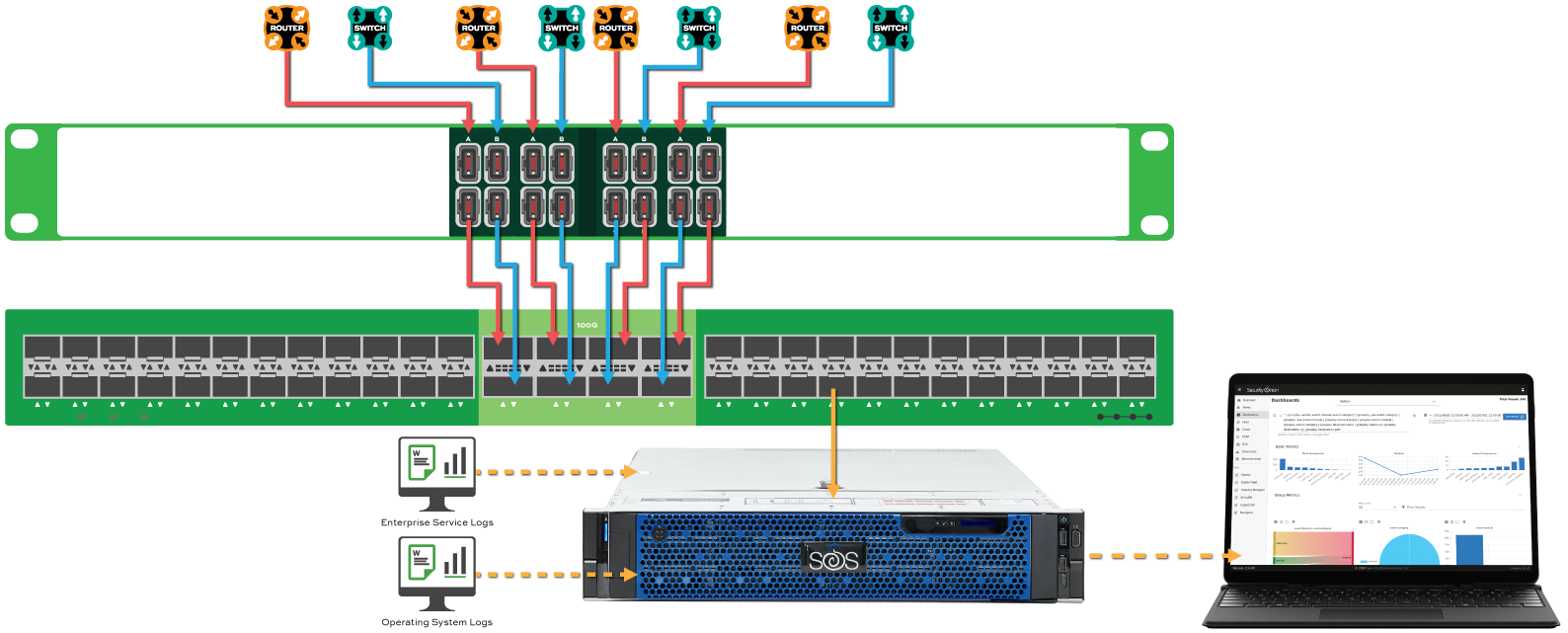
Enterprise Security Monitoring
Security Onion Solutions understands the hardware requirements for Security Onion in the enterprise environment. By leaving the hardware research, testing, and support to SOS, you can focus on what’s important for your organization. Security Onion Solutions produces a variety of appliances which can be combined to support almost any monitoring requirement from 1G up to 100G. Garland Technology ensures complete packet visibility by delivering a full platform of network TAP (test access point), inline bypass, network packet brokers, and data diode solutions.

- Incident Response
- Cloud
- Full PDF Solution Brief

Peel back the layers of your rapid response events with Security Onion Solutions (SOS) Response-Ready (R2) kits. Quickly deploy the power of Security Onion to hunt for adversaries or respond to incidents. SOS R2 kits are designed for easy mobility on commercial transportation and robust capability onsite. By partnering with Garland Technology, Security Onion Solutions offers customizable kit configurations with portable TAPs and aggregators to meet the needs of your teams in the field.
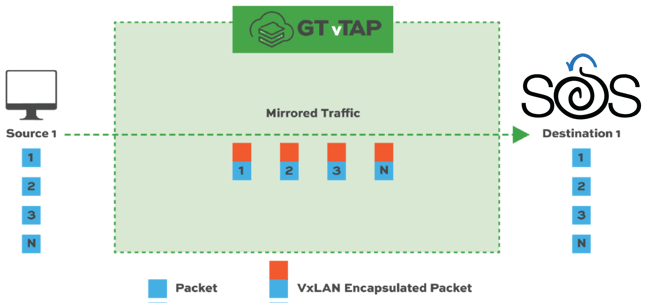
Security Onion is deployable in cloud and hypervisor environments. Security Onion Solutions maintains machine images in Azure, AWS, and Google Cloud Platform. When coupled with the Garland Technology vTAP for out-of-band packet mirroring, Security Onion can see deeper into your modern compute environments, providing visibility into Cloud and On-Premise environments without impacting performance or architectures and without modifying your deployment architectures. GT vTAP complements native cloud mirrors, providing added visibility and replication [1:N] to multiple destinations while allowing you to fuel network or information security tools.
- How It Works
- Bypass TAP Benefits
- Full PDF Solution Brief
- How It Works
- How It Works
- How It Works
Bypass manages the availability of inline tools, preventing a single point of failure in the network by “bypassing” the device in the event it fails or needs to be updated. Reducing network downtime. Bypass is unique to the other TAP modes, as it is an inline use case not out-of-band.
• Keep up with Federal security mandates
• Expedited problem resolution
• Ability to pilot or deploy need security tools
• No maintenance windows
• Simple configuration ensures a quick set-up
• Zero subscription fees so O&M expenses don’t increase
■SOLUTION EDGESAFETM BYPASS TAP
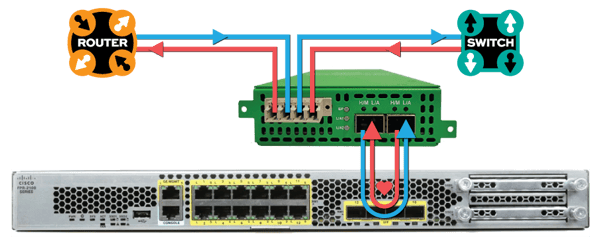
• Install a Garland Technology Bypass TAP between Cisco Firepower and the network
• Bypass TAP manages the availability of Firepower at any time without having to take down the network
• Bypass TAP continuously checks the health of Firepower with heartbeat packets and the Bypass TAP will bypass Firepower to keep the network up-and-running in the event Firepower becomes unavailable
| PROBLEM 1 PORT FAILURE | ||
|
■WITHOUT TAP • The network |
|
■WITH TAP • Uptime • Tool is bypassed while it is being updated |
| PROBLEM 1 PORT FAILURE | ||
|
■WITHOUT TAP • The network |

|
■WITH TAP • Uptime • Tool is bypassed while it is being replaced |






