

For years now we all have read about the difference between data capture off a span/mirror port and a network TAP.
Packet Pioneer, Chris Greer was interested to see the difference between a data stream captured on a network TAP versus a SPAN port. So he set up a test with a few PCs, a TAP, a SPAN port, a couple of hardware network analyzers, and a healthy stream of data.
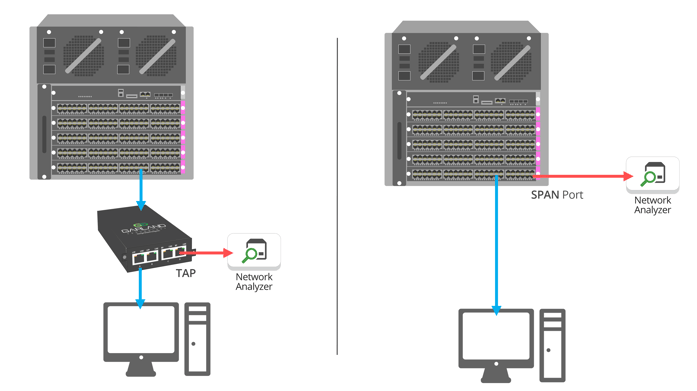
Packet Pioneer connected two PCs to a basic Cisco Catalyst Switch at 100Mbps. A throughput test using iPerf was configured and run between the two machines. On one of the PCs, he placed a 100Mbps TAP, and placed a hardware analyzer on it to capture. Lastly, he configured a SPAN on the switch to forward all traffic to and from this port to another hardware analyzer.
Below is a basic drawing of the setup.
The throughput test finished with a result of 93.1Mbps sustained for 10 seconds between the two PCs.
| TAP vs SPAN | Packets captured | Delta Time at TCP Setup |
| TAP Capture Results | 133,126 | 243uSec |
| SPAN Capture Results | 125,221 | 221 uSec |
The SPAN data capture showed almost 8,000 packets missing from the trace. This represents almost 8% of the total packets captured by the analyzer on the network TAP. We should also point out that this was on a 100Mbps interface, not a Gigabit interface, and there were no errored frames. The switch bus was not in a near overloaded state.
Also, the difference in the timing between the TCP SYN and SYN ACK in the two traces shows us that the switch is not treating both the SPAN and Destination ports the same. In fact, it was forwarding traffic to the SPAN port faster than the true destination. While the difference is only 21 uSec, it shows that the switch is affected when SPAN is enabled. It is not as seamless as it would appear, and this delay was under no load test. With the switch loaded with traffic, the losses and timing will show greater differential and also dropped packets.
Considering the results of their test, Chris Greer, a network analyst at Packet Pioneer, said, “I am now a full believer in using a real [network] TAP whenever possible, especially when timing and total view of the data is important!”
Looking to add a visibility solution to your next deployment, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do!
If the inline security tool goes off-line, the TAP will bypass the tool and automatically keep the link flowing. The Bypass TAP does this by sending heartbeat packets to the inline security tool. As long as the inline security tool is on-line, the heartbeat packets will be returned to the TAP, and the link traffic will continue to flow through the inline security tool.
If the heartbeat packets are not returned to the TAP (indicating that the inline security tool has gone off-line), the TAP will automatically 'bypass' the inline security tool and keep the link traffic flowing. The TAP also removes the heartbeat packets before sending the network traffic back onto the critical link.
While the TAP is in bypass mode, it continues to send heartbeat packets out to the inline security tool so that once the tool is back on-line, it will begin returning the heartbeat packets back to the TAP indicating that the tool is ready to go back to work. The TAP will then direct the network traffic back through the inline security tool along with the heartbeat packets placing the tool back inline.
Some of you may have noticed a flaw in the logic behind this solution! You say, “What if the TAP should fail because it is also in-line? Then the link will also fail!” The TAP would now be considered a point of failure. That is a good catch – but in our blog on Bypass vs. Failsafe, I explained that if a TAP were to fail or lose power, it must provide failsafe protection to the link it is attached to. So our network TAP will go into Failsafe mode keeping the link flowing.
Single point of failure: a risk to an IT network if one part of the system brings down a larger part of the entire system.
Heartbeat packet: a soft detection technology that monitors the health of inline appliances. Read the heartbeat packet blog here.
Critical link: the connection between two or more network devices or appliances that if the connection fails then the network is disrupted.