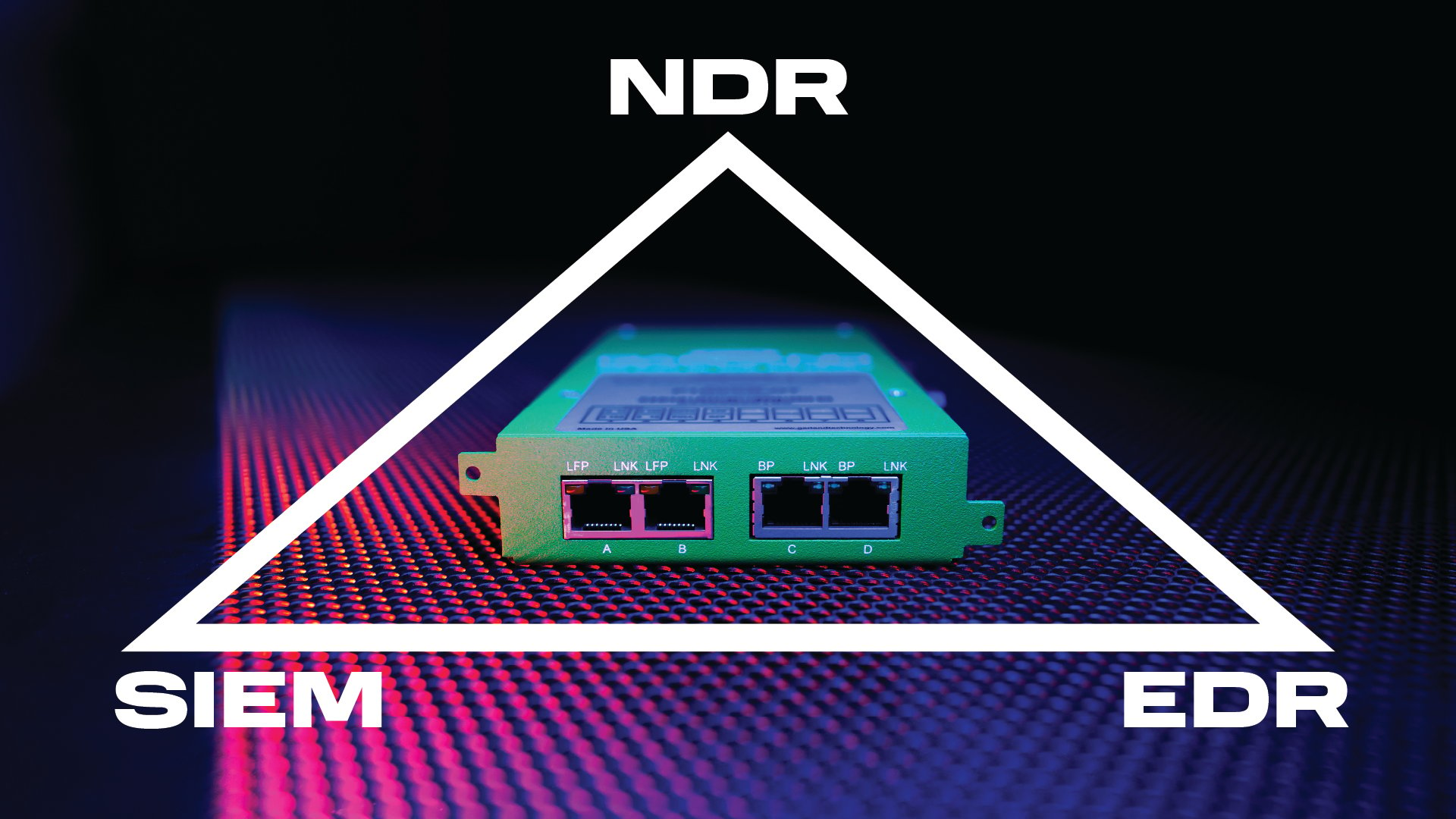
Supporting the SOC Visibility Triad with Network TAPs
To put it bluntly, organizational IT and security teams have never been in a more difficult position than they are today. The non-stop need for businesses to adopt any-and-all devices has...