
Cybercrime on local and state governments is continuing to rise, as cybercriminals understand the government possesses lots of data and information that are vital and highly classified. The risks to these federal IT systems are increasing, with insider threats from witting or unwitting employees, escalating threats from around the globe, and the emergence of new more destructive attacks. The U.S. Government Accountability Office reports that over 35,000 security incidents were reported by federal executive branch civilian agencies to the Department of Homeland Security in fiscal year 2017.
In response, the government has adopted a Zero Trust (ZT) strategy, which shifts focus toward individual access and away from protecting wide segments of the network, away from a perimeter-based only cybersecurity approach. As we reviewed in our previous blog, “Building A Zero Trust Visibility Architecture,” a few main architecture concepts, including ZT Network Requirements, ZT Framework, and ZT Visibility fabric. Here we will introduce how to implement a regular cycle of monitoring, maintenance and updating.
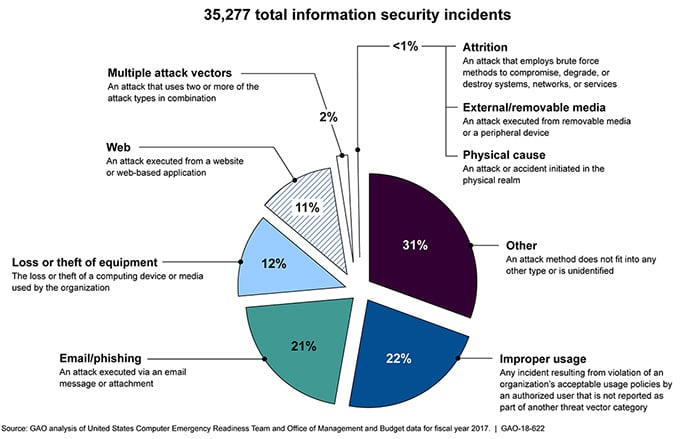
The key concept in a Zero Trust cybersecurity strategy is that organizations need to proactively control all interactions between people, data, and information systems to reduce security risks to acceptable levels. If agencies properly adopt Zero Trust, they have the potential to substantially change and improve their ability to protect their systems and data.
Agencies are expected to modernize their aging cybersecurity architectures to address new threats and service requirements, despite budget challenges and overtaxed workforces.
Zero Trust strategy
A recent assessment of ZT technologies by ACT-IAC and the Federal CIO Council concluded that modern IT security solutions need to incorporate several minimum characteristics:
- Segregate users, devices, data, and services, within a trust framework, to ensure every access request is validated and deliberately permitted or disapproved;
- Be resistant and resilient to attack without a large administrative burden; and
- Be able to easily and rapidly adjust to an ever-changing service environment also without a large administrative burden.
>> Download now: Zero Trust Cybersecurity [Whitepaper]
With all of the new regulations and standards guiding the transition to Zero Trust, we get that it can be overwhelming for IT leaders tasked with upgrading highly complex government networks. And while this isn’t a transition that will happen overnight, it’s not as if you need to completely rip and replace your existing security infrastructure to implement Zero Trust.
When considering your Zero Trust strategy, these five steps can help simplify your implementation:
- Identify the Protect Surface
- Map the Data Flows
- Building a Zero Trust Visibility Architecture
- Create a Zero Trust Policy
- Monitor and Maintain
Monitor and Maintain Zero Trust Environment
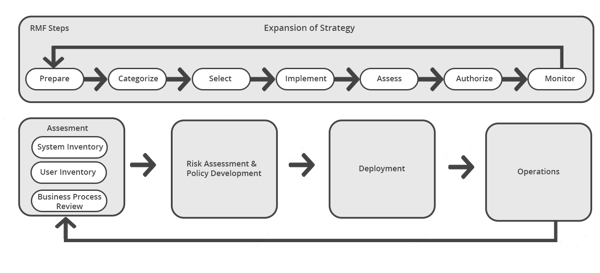
Implementing a Zero Trust model will be an incremental process for your governmental agency. A Zero Trust Architecture requires organizations to have detailed knowledge of its assets (physical and virtual), users, and business processes, which includes a survey of assets, users, data flows, and workflows.
Once this foundation information is documented, a regular cycle of monitoring, maintenance and updating is implemented. This final step is all about taking advantage of visibility tools to support continuous monitoring of the Zero Trust Architecture so you can maintain effectiveness as needs evolve.
Bypass TAPs play an important role in this step of Zero Trust maintenance and updating. Their inline lifecycle management capabilities make it easy to take inline tools out-of-band for updates, install patches, conduct troubleshooting tasks, and sandbox/optimize/validate the tools before pushing them back inline, without taking the network down.
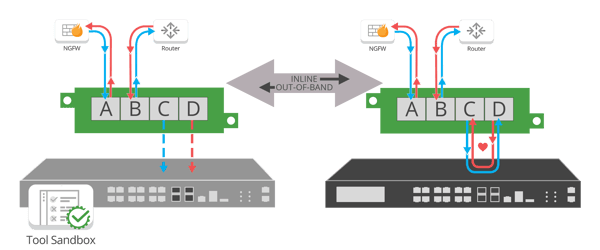
Maintaining Zero Trust with Inline lifecycle Management provides:
- Reduced risk of unplanned downtime
- Sandbox new appliances using real-time data
- Alerting/reporting on inline appliance failure / performance
- Cost reduction of security appliances
- Reduced network complexity
It is critical to build a Zero Trust Architecture that allows you to monitor and maintain your Zero Trust environment, by guaranteeing total network visibility that meets the highest government cybersecurity maturity levels.
Garland Technology is here to help you succeed on the path to Zero Trust. Our full portfolio of network TAPs, network packet brokers, bypass technology, and cloud visibility solutions will simplify your cybersecurity upgrades. Set a free Design-IT meeting with one of our network engineers for a no obligation, Visio network design session.

