
The ability to detect and remediate cyber attacks pose an existential threat to IT organizations worldwide. A study from IBM and Ponemon found that companies that detect and contain data breaches within 30 days save, on average, more than $1 million compared to organizations that take longer to respond.
Managing the Network Edge is vital to secure and protect these critical corporate assets, ensure network performance, identify systemic anomalies and identify insider/outsider cyber threats. This applies to banking, healthcare, telecom, brick-and-mortar retail as well as water/energy utilities.
To begin, let’s review what is defined as the Network Edge. The Network Edge is the specific boundary of WAN to LAN connectivity and ownership in a network. The Edge protects the critical assets of a corporation and is typically the demarcation point of local connectivity to wider Internet connectivity. This is different from Edge computing which is an industry directive to decentralize traditional data centers and bring compute resources closer to where they will be consumed. This blog series will touch on Edge compute monitoring in a later segment.
The edge of the network is quickly evolving as companies manage decentralized workforces and migrate to hybrid public/private cloud environments. The Network Edge is the critical location to monitor/protect data transfer and identify threats. With the right security and monitoring infrastructure, organizations can safely mitigate threats across a more mobile workforce, increasing the number of IoT devices, remote network locations and hybrid clouds.
Monitoring the Network Edge can vastly improve performance, response times, and bandwidth across your organization, which ultimately helps organizations deliver more innovative end user experiences. Securing the Network Edge is a parallel effort that entails safely accessing remote workloads, identifying inbound cyber threats, monitoring network vulnerabilities and encrypting/decrypting critical communications. The good news is both of these initiatives can be integrated with a properly architected monitoring and security implementation and toolset.
But how exactly does it work? As Network Edge and datacenter design are both quickly evolving away from traditional architectures, it’s important to understand key components to address challenges and monitoring/security options.
Key Components of Managing the Network Edge
Regardless of your industry, architecting for effective edge monitoring introduces a wide variety of moving parts— many of which are physically (and virtually) deployed outside of the enterprise data center. There are remote users and IoT devices to account for resulting in an array of additional challenges. When you’re starting to think about the network edge, there are key components that you’ll need to include in your design:
- Hybrid Cloud: The steady shift toward hybrid cloud and multi-cloud models for enterprise data centers have changed the landscape and blurred the “edge” in defining the Network Edge. Defining critical workloads and applications across new environments is key efficiency in paradigm shift as well as key area to focus in regards to monitoring and security.
- Network Edge: The network edge is the physical or virtual boundary (or set of boundaries) in a network design that demarcates WAN access to (and typically -ownership of) the enterprise network. Traditionally, the enterprise network consisted of a wired/wireless corporate LAN and physical data centers managed by the company's IT department. That specific ‘demarcation’ point is both multiplying and moving across the hybrid cloud environment.
- Branch Locations: These are remote or smaller locations within your organization containing critical assets that may require a separate set of security/monitoring layers.
- Inline vs Out-of-band Tools: Inline tools are ‘active’ devices like firewalls and Intrusion Prevention System(s) that interact with live network traffic. Out of band tools receive monitor data and are used to enable metrics on network performance, application performance, network vulnerabilities, traffic inspection and detect network/security anomalies. The architecture, mix and placement of these tools will enable (or compromise) the level of monitoring and security over an organization’s infrastructure.
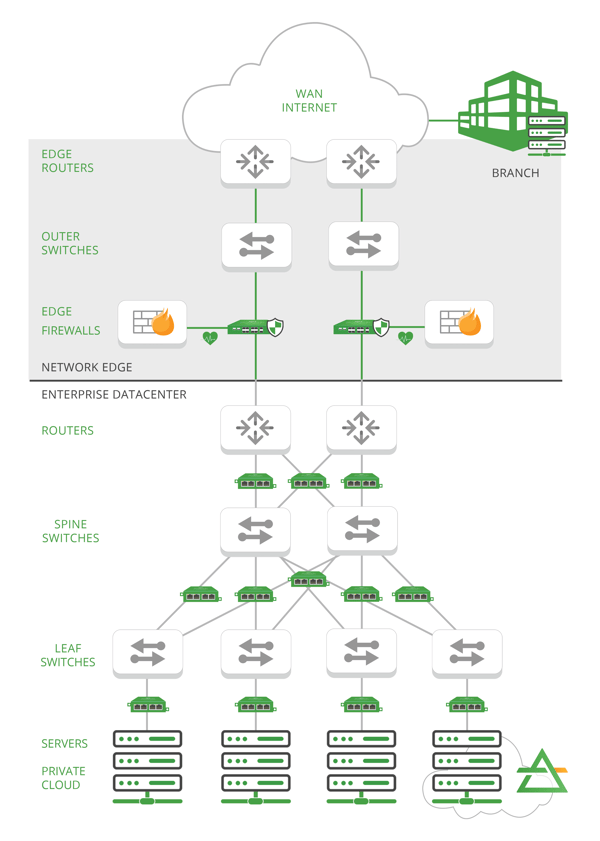
The right network design and combination of inline/out-of-band tool placement will enhance network edge monitoring and security. The result will be optimal network performance, minimal latency to end devices, quality of experience for key services and best in class security monitoring.
>> Download Now: Managing the Edge [Free whitepaper]
Challenges of Managing the Network Edge
According to IBM estimates, the approximately 15 billion connected edge devices deployed today will grow to 55 billion by 2022. The explosive growth of connected devices at the edge means management of hundreds, thousands, or even millions of new endpoints in the coming years. Combined with network transformations to hybrid cloud and software defined networking (SDN), traditional approaches to centralized management aren't well-suited to support the diversity of devices and business operations.
The massive scale of these transformations highlights key challenges in monitoring and securing all of these devices, people, and clouds environments.
Security Vulnerabilities at the Edge
The mobile transformation and cloud-oriented network design evolution is changing the approach to ‘traditional’ physical protections and security consistency associated with centralized, private IT environments. The defenses established in a private data center do not extend to the modern Network Edge designed for multi-cloud operations, IoT, edge computing remote sites and mobile workforces.
Data protection must be a focal point from the very start of Network Edge design. If data is compromised at the edge, risk and new cyber threats will propagate across the core data center and give attackers a foothold in your organization. Maximizing and maintaining visibility of activity across the network edge. This entails use of appropriate inline and out-of-band active and analytic tool sets.
The Blurring Network Edge
The migration towards moving workloads to public cloud environments like AWS, Azure, Google Cloud or combining with private virtual environments are changing the traditional network edge boundary across these more dynamic, virtual environments. WAN/LAN boundaries, Internet Access and firewall placement that were once singular physical locations are now dispersed across a broad landscape of physical and virtual environments. A massively scaled (and blurred) network edge will inevitably introduce new blind spots. Applying traditional network monitoring approaches will need to evolve to a more elastic network edge that leverages physical as well as cloud and virtual monitoring nodes. This is a unique challenge that requires a sustained, elastic approach to monitoring strategy, tool placement and security strategies.
Branch/Remote Locations
Dispersed critical assets and a more dispersed, remote workforce introduces another layer of complexity. Introduction of remote tools and monitoring may be needed to complement centralized tool deployments. Addition of remote inline tools like firewalls are critical tools, but will require new approaches in automation and lifecycle management to assure performance and vulnerability assessment at these locations.
Edge Monitoring: A Requirement for Effective Edge Networking
A well planned network edge design with a proper tool set will enable comprehensive monitoring to identify and resolve performance/security issues. Forcing traditional solutions into a modern network edge design would result in significant blind spots and significant risks to cyber attacks. A flexible network edge monitoring approach with combination of inline and out-of-band tool sets is key.
Garland’s innovative inline edge visibility products enable this new design approach. Architectural assets include bypass TAPs, inline packet brokers and cloud monitoring solutions that eliminate blind spots across edge, enterprise, datacenter and cloud networks. These building blocks ensure 100% packet visibility, network/security tool optimization, network performance, improved tool lifecycle aimed at detecting and mitigating performance issues and security threats throughout your evolving IT infrastructure.
Some of our most critical edge solutions include:
- EdgeLens® Inline Security: EdgeLens is a failsafe bypass TAP with a built-in network packet broker for complete management of your network edge. It enables you to deploy multiple inline, active security tools and out-of-band monitoring tools while gaining 100% network access and visibility.
- EdgeSafe™ Bypass Network Tap: This is the first line of defense for security threats and breaches, providing 100% visibility for security tools like firewalls, IPS, web application firewalls, data loss prevention, DDoS protection, and SSL decryption to protect and monitor. As the edge of your network expands, bypass technology is essential for avoiding costly network downtime.
- Garland Prisms: Advanced packet visibility for security monitoring and packet inspection in your cloud environments. The air gapped cloud traffic mirroring, TLS decryption, and tunneling that come with Garland Prisms is ideal for edge networking scenarios because it enables deep visibility into the data traveling from the edge to the core data center and back.
While modern network edge can seem complicated compared to traditional data center architectures, Garland has the critical components needed to ensure success. Ensuring comprehensive visibility, monitoring, and security across this new physical/virtual/cloud landscape is key.
But this is just one aspect of mastering the edge of the network. In Part 2 of this series, we’ll dig deeper into the security conversation. Looking to add inline or out-of-band security monitoring solutions, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do.

