
Part 1 in this two-part series on how to troubleshoot the network focused on the most common challenges you’ll face—connectivity, performance, and latency troubleshooting scenarios. And in a perfect world, these would be the most difficult network problems you’d ever face.
But the reality is that troubleshooting has grown increasingly complex over the last decade. Now, network speeds are faster than ever, you’re processing exponentially more data, and cyber threats have become increasingly sophisticated. As a result, it’s harder than ever to find root causes and solutions to network problems.
That’s where network forensics comes into play. Here in Part 2 of our series, we’re going to focus on the role of network forensics in solving performance and security problems and how to troubleshoot when these tools have issues of their own.
Troubleshooting Scenario for Network Forensics
Network forensic analysis tools (NFATs) play an important role in troubleshooting more advanced problems across your business. They enable you to capture, record, and analyze network packets to uncover the source of an issue.
The primary use case for network forensics is in cybersecurity, where NFATs let you identify incidents, preserve relevant records, collect necessary digital evidence, examine patterns, analyze attacks, and respond to incidents. But you can take advantage of key capabilities of NFATs, including data capture, data discovery, and analysis, to troubleshoot intermittent performance issues, monitor for policy compliance, identify data leaks, and more.
There’s a wide variety of NFATs you could use to troubleshoot issues across your network. Some of the more common ones include:
- Wireshark: The free and open-source packet analyzer that’s used most often for protocols.
- Xplico: Another open source tool that reconstructs the contents of data gathered by a packet sniffer like Wireshark or dumpcap.
- NetworkMiner: This NFAT can be used as a passive packet sniffer and makes it easy to conduct advanced analysis that focuses on hosts and their attributes as opposed to raw packets.
The problem is that when you rely on NFATs to capture, store, and analyze network events, you’re assuming one thing—that these tools have 100% visibility into your traffic. What happens when you see evidence that your network has been compromised but your NFATs aren’t reporting any issues?
This is when you have to start troubleshooting your network forensics by manually looking at the host system experiencing a problem. Consider a potential scenario where a host system is compromised by a rootkit system. An attacker works around NFATs by manipulating the data sent between a host system and a user. This is where it’s critical to be able to compare the data on a link with activity expectations.
Long before a troubleshooting scenario has come up, you should have created a baseline of traffic behavior for your network. Then, when a problem comes up with your network forensics tools, you can manually tap into the link in question to get a clean, unbiased view of activity. By comparing the data packets on the link to baseline expectations, you can identify the issues that NFATs weren’t able to identify because of the rootkit.
Regardless of the specific issue you’re facing, the key to troubleshooting network forensics is to analyze data packets at the lowest level. Packets don’t lie. And even though you rely on NFATs for recording packets, they can’t effectively complete the job without proper visibility. That’s why your most powerful tool for troubleshooting digital forensics problems is a network TAP.
>> Download Now: TAP vs SPAN [Whitepaper]
What You Need to Troubleshoot Network Forensics
If you have a network forensics problem to troubleshoot, that means you have a packet capture issue on your hands. And when network forensics tools are failing, you don’t have time to waste hunting for a root cause. When you know there's a network forensics issue, it’s likely your company is facing a cyber attack and every second counts when you’re responding.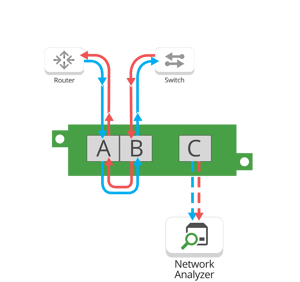 Network TAPs give you the ability to capture 100% of all traffic on a link without interrupting the dataflow and enable you to analyze packets in real time. In a perfect world, TAPs would already be built into the fabric of your network design and you could dig deep into network forensics issues at any time. However, there are times when you experience issues on links that aren’t already tapped.
Network TAPs give you the ability to capture 100% of all traffic on a link without interrupting the dataflow and enable you to analyze packets in real time. In a perfect world, TAPs would already be built into the fabric of your network design and you could dig deep into network forensics issues at any time. However, there are times when you experience issues on links that aren’t already tapped.
This is why a portable network TAP is such a crucial component of any field test monitoring and troubleshooting kit. For field engineers that need to troubleshoot network forensics issues quickly, it’s important to have a highly efficient TAP that can enable analyzers to properly inspect 100% of data packets.
This is what makes the new FieldTAP, ideal for 10M/100M or 10M/100M/1G field test monitoring, these pocket-sized portable network TAPs make it easy for you to tap a problematic link, check for internet connection, network connectivity, and deeper issues with your NFATs.
One of the key scenarios where FieldTAPs are most helpful is when Wireshark users experience issues. When you need to troubleshoot a Wireshark issue, you can quickly connect the FieldTAP to collect packets directly off the wire and identify problems efficiently. This is equally useful for any other network analyzers or dedicated forensics tools.
Visibility starts at the packet level. When you have a forensics issue, you need a purpose-built, non-intrusive hardware device that will copy all network data so you can get a true look at the problem. To help you do this, our FieldTAPs include key features like:
- The ability to collect full-duplex 1G of traffic
- Monitoring on USB 3.0
- Network aggregation
- Available in a packet size mini or portable form-factors with 1U rack mount
- USB2/USB3 powered or with external power supply
From common troubleshooting scenarios to more urgent, advanced network forensics problems, FieldTAPs give you the efficient way to reliably view network activity. If you want to add them to your troubleshooting kit, contact us and tell us about your needs.

