

"It's the Unicorn we've been looking for!"
This was the response I got the other day when I was explaining to a customer the benefits of looking back at packets before and after they pass through an active, inline device and a packet capture or forensics tool.
Simply put, how else will enterprise networks have real-time knowledge of an attempted attack, as well as the ability to look back and see how the packets were altered or dropped?
Historical lookback aka before & after, is solution that uses hybrid bypass TAPs with monitoring ports that allow both security tools, such as next-gen firewalls and intrusion prevention systems to share packets with multiple monitoring tools such as network packet capture, forensics, deep packet inspection, etc.
EdgeLens® Garland Technology's hybrid bypass TAP and In-line Security Packet Broker provides identical network traffic streams, both through the active, inline security tools (IPS/NGFW/WAF), and to the network packet capture, forensics, deep packet inspection and/or lawful intercept tools.
Because all devices see the same traffic, it is easy to correlate events generated by the active, in-line device with the PCAP data which is captured and indexed within the out-of-band packet analysis tools.
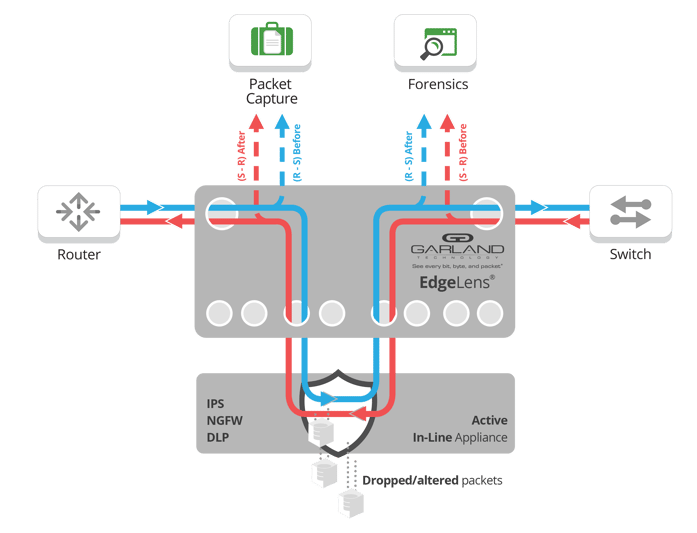
Once a breach or critical event is detected, it's imperative to facilitate a real-time security incidence response, including retrieval of full sessions and other detailed context around those critical events. Extracted PCAP files may be further analyzed by a variety of out-of-band tools for security forensics.
This solution can be deployed with most vendors network analyzer tools and security tools, the tools are independently managed through the EdgeLen's interface - the key here is that all the tools share the same packets via the identical network stream.
Looking to add IT Security solution to your security deployment, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do!
If the inline security tool goes off-line, the TAP will bypass the tool and automatically keep the link flowing. The Bypass TAP does this by sending heartbeat packets to the inline security tool. As long as the inline security tool is on-line, the heartbeat packets will be returned to the TAP, and the link traffic will continue to flow through the inline security tool.
If the heartbeat packets are not returned to the TAP (indicating that the inline security tool has gone off-line), the TAP will automatically 'bypass' the inline security tool and keep the link traffic flowing. The TAP also removes the heartbeat packets before sending the network traffic back onto the critical link.
While the TAP is in bypass mode, it continues to send heartbeat packets out to the inline security tool so that once the tool is back on-line, it will begin returning the heartbeat packets back to the TAP indicating that the tool is ready to go back to work. The TAP will then direct the network traffic back through the inline security tool along with the heartbeat packets placing the tool back inline.
Some of you may have noticed a flaw in the logic behind this solution! You say, “What if the TAP should fail because it is also in-line? Then the link will also fail!” The TAP would now be considered a point of failure. That is a good catch – but in our blog on Bypass vs. Failsafe, I explained that if a TAP were to fail or lose power, it must provide failsafe protection to the link it is attached to. So our network TAP will go into Failsafe mode keeping the link flowing.
Single point of failure: a risk to an IT network if one part of the system brings down a larger part of the entire system.
Heartbeat packet: a soft detection technology that monitors the health of inline appliances. Read the heartbeat packet blog here.
Critical link: the connection between two or more network devices or appliances that if the connection fails then the network is disrupted.