

“Garland Technology triumphs in highly-volatile and critical environments, allowing us to provide visibility into our customers information, and help enterprises take proactive action against cyber-attacks.”
There is a huge industry dedicated to phishing awareness and prevention, with an increased emergence of companies built on the concept of simulating phishing emails and tracking how employees respond. It’s a step forward in terms of educating users and combating cyber security threats, but there still remains the need to partner with companies that can provide an overall security strategy.
Phishing is a human problem, and building a meaningful security-aware culture requires buy in from everyone, not just the security team. So as targeted phishing remains the primary cybersecurity threat to organizations, and the attacks come from all directions—email, web, and network, all it takes is one click, one message, or one network callback for a targeted attack to be successful.
[Want more on Identifying and Preventing Phishing Attacks? Check out the Infographic we put together with Area 1 Security.]
NetOps and SecOp teams have become bystanders to solutions that continue to miss the low volume, socially engineered, and highly-damaging phishing campaigns, but the teams remain vigilant in the goal to become active participants in the mission to identify how to stop phishing attacks across all traffic vectors.
Existing defenses struggle with highly-focused and sophisticated campaigns and users are constantly getting lured into taking phishing baits, leading to significant financial damage or data loss.
Area 1 Security’s offerings work to identify phishing campaigns, attacker infrastructure, and attack delivery mechanisms during the earliest stages of an attack cycle, and they turn to Garland Technology to ensure maximum reliability and functionality for their globally-distributed sensors, massive scale web crawling, and comprehensive pre-attack analytics requirements.
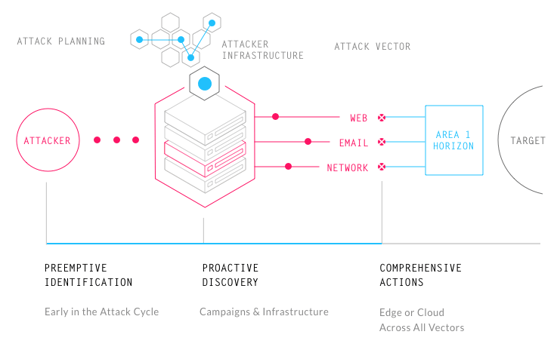
Garland Technology has enabled Area 1 Security to maintain 100% reliability in the most extreme environments to include recent and large-scale security threats from humans, machine, and natural disasters alike. Thus complete functionality and comprehensive reliability at their global data centers were the largest determining factors helping their customers stay ahead of these looming cyber-attacks.
Garland Technology’s reliability and power superiority levels for Area 1 Security customers extended even further into providing 100% accurate False Tolerance analysis, granting a proactive view into early stage targeted attacks, resulting in Area 1 Security customers being able to take quick action and respond to looming threats. While proactive patterns are critical, the ability for Area 1 Security’s global data centers to obtain and maintain 100% full power with the magnetic failover feature from Garland Technology TAPs, have yielded their only full-scale and 100% reliable network TAP solutions to date.
“After utilizing other similar TAPs, Garland Technology remains second-to-none delivering 100% reliability, pricing, and logistics at full scale.”
Area 1 Security continues to turn to Garland Technology for the speed of their global logistics, the unparalleled integration support, capacity planning, and modeling surrounding future deployments.
If the inline security tool goes off-line, the TAP will bypass the tool and automatically keep the link flowing. The Bypass TAP does this by sending heartbeat packets to the inline security tool. As long as the inline security tool is on-line, the heartbeat packets will be returned to the TAP, and the link traffic will continue to flow through the inline security tool.
If the heartbeat packets are not returned to the TAP (indicating that the inline security tool has gone off-line), the TAP will automatically 'bypass' the inline security tool and keep the link traffic flowing. The TAP also removes the heartbeat packets before sending the network traffic back onto the critical link.
While the TAP is in bypass mode, it continues to send heartbeat packets out to the inline security tool so that once the tool is back on-line, it will begin returning the heartbeat packets back to the TAP indicating that the tool is ready to go back to work. The TAP will then direct the network traffic back through the inline security tool along with the heartbeat packets placing the tool back inline.
Some of you may have noticed a flaw in the logic behind this solution! You say, “What if the TAP should fail because it is also in-line? Then the link will also fail!” The TAP would now be considered a point of failure. That is a good catch – but in our blog on Bypass vs. Failsafe, I explained that if a TAP were to fail or lose power, it must provide failsafe protection to the link it is attached to. So our network TAP will go into Failsafe mode keeping the link flowing.
Single point of failure: a risk to an IT network if one part of the system brings down a larger part of the entire system.
Heartbeat packet: a soft detection technology that monitors the health of inline appliances. Read the heartbeat packet blog here.
Critical link: the connection between two or more network devices or appliances that if the connection fails then the network is disrupted.